Today I want to talk about modern OS Deployment for Windows Autopilot Enrollments using OSDCloud. Also, I will show you where we came from with regards of OS Provisioning and which customizations we made to OSDCloud to make it fit our needs even more.
OSD using a SCCM Task Sequence
When we started using Windows Autopilot back in 2018/19, we needed a solution to prepare existing devices for the enrollment with Autopilot and since we started using Pre-Provisioning (aka. WhiteGlove) as well, the official way for Autopilot for existing devices using the exported .json Profile was not an option. We started using a basic SCCM Task Sequence to install the base Windows Image and upload the Autopilot Hash as described here: https://mikemdm.de/2023/01/29/can-you-create-a-autopilot-hash-from-winpe-yes/ and here: https://mikemdm.de/2023/02/12/automate-autopilot-uploads-with-azure-automation-runbooks/
The Task Sequence looked something like this, and contained basically three things besides the OSD itself, the Autopilot Upload, the “Tennant Lockdown” Feature using a script based on the solution of Michael Niehaus: https://oofhours.com/2022/05/31/requiring-a-network-connection-during-oobe/ and a part for handling drivers (not visible in the Screenshot).
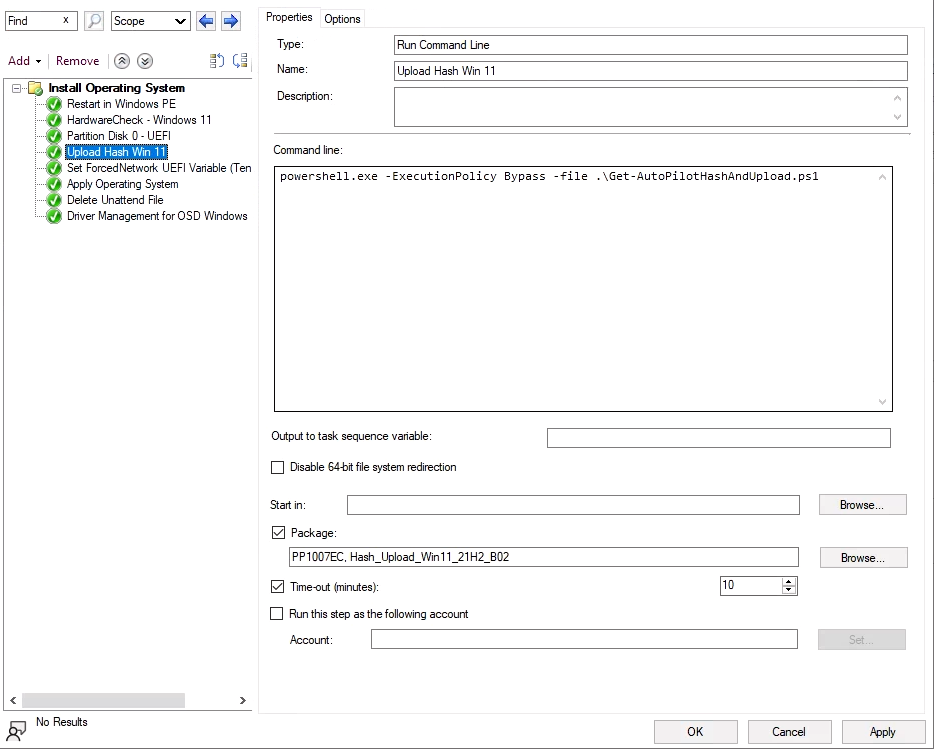
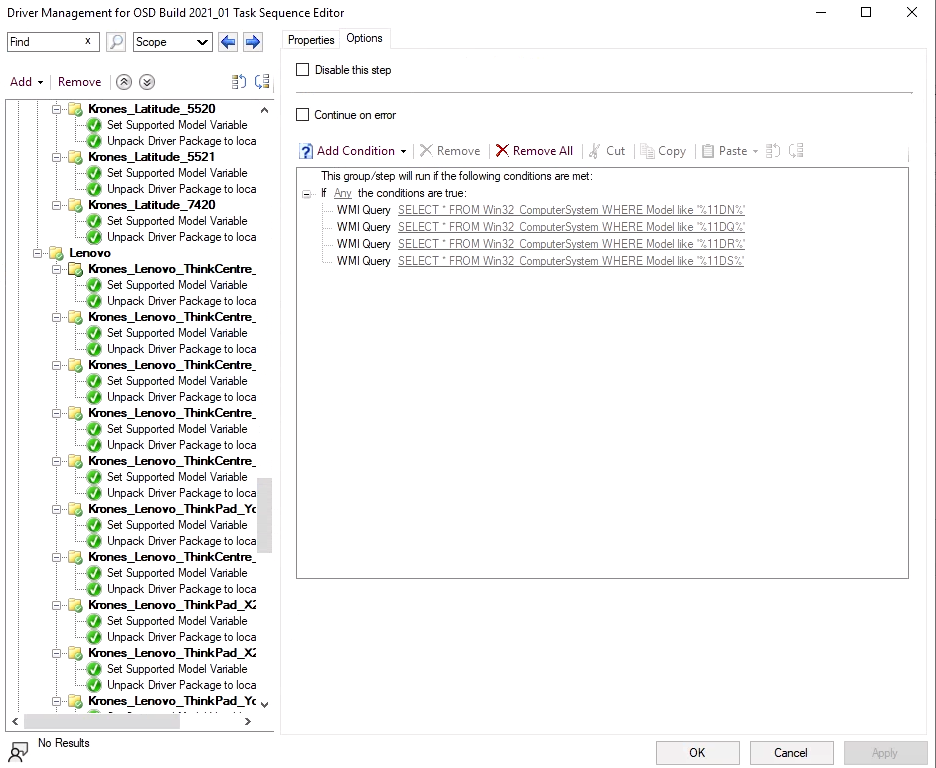
While this solution worked pretty reliable, we had one issue with this solution, the driver management. Since we had to support more than 100 different hardware models from Dell, HP and Lenovo, we needed to provide drivers for all of these models for the inital installation. Additional to that, we wanted to have a way to allow installation of even more models in case something was not available in a specific region. All this created the need for a pretty large Task Sequence that needed to be maintained and also needed more than 100GB of storage on our around 30 Distribution Points all around the world.
Modern OS Provisioning using OSDCloud
Our Solution for this issue came with the wonderful Project OSDCloud, that supported nearly all of our hardware models out of the Box, by downloading drivers directly from the OEMs, eliminating the need of local repositories for these driver packs. Additionally with the support to download drivers from Windws Update, it even can support new / unknown models.
Since we already wanted to get rid of our SCCM Infrastructure and most of our newly bought devies are already uploaded by the OEM, we decided to go with an bootable USB Drive Solution, which in combination of the integrated Wi-Fi support allows us to worst case use an iPhone Hotspot to reprovision a client if needed.
While OSDCloud provides and integration for Autopilot, it is based on the .json file injection, makeing it unsuitable for Self-Deploying or Pre-Provisioning Scenarios. To mitigate this limitation and to further simplify the GUI to the point, where the admin does not have to choose the OS Version, we decided to build a small PowerShell Forms based GUI, that can be used to launch OSDCloud with a few parameters, Upload the device to Autopilot and set the Tenant Lockdown UEFI Variable. You can find the PowerShell Scripts for the launcher on my GitHub, so you can customize it to your needs: https://github.com/mmeierm/Scripts/tree/main/OSDCloud
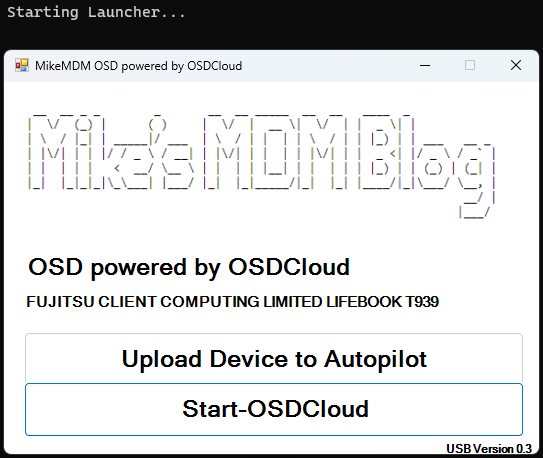
The first Page of the Launcher will present you two options, the Autopilot Upload Button will unzip a password encrypted archive, containing the Autopilot Upload Script, described here, also i uploaded the script to extract the files to GitHub.
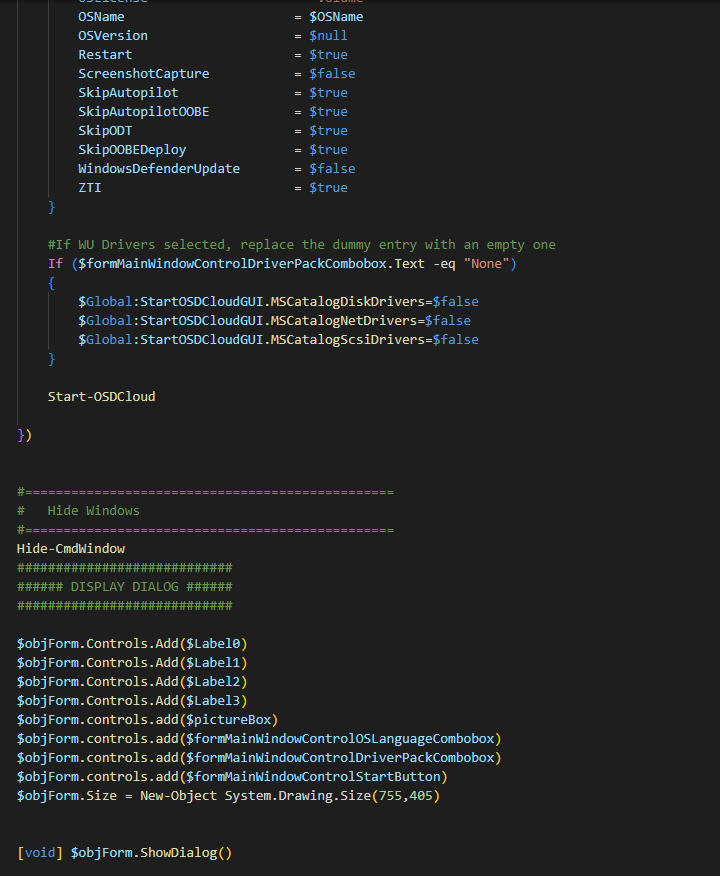
The Start-OSDCloud Button will show a new Page that allows you to select a driverpack and the OS Language.
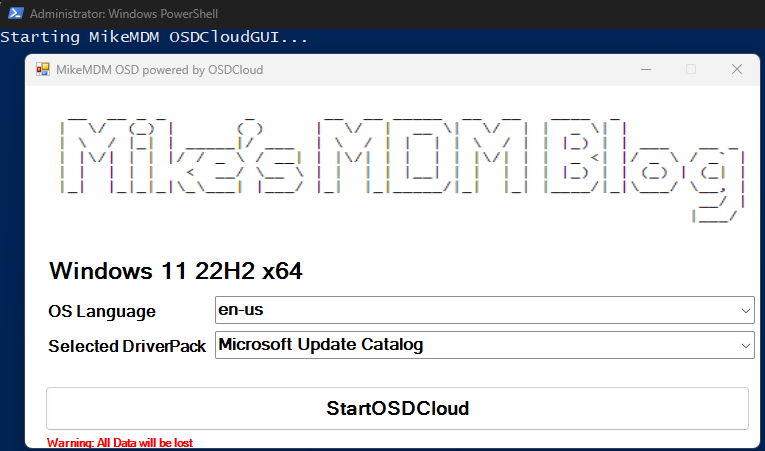
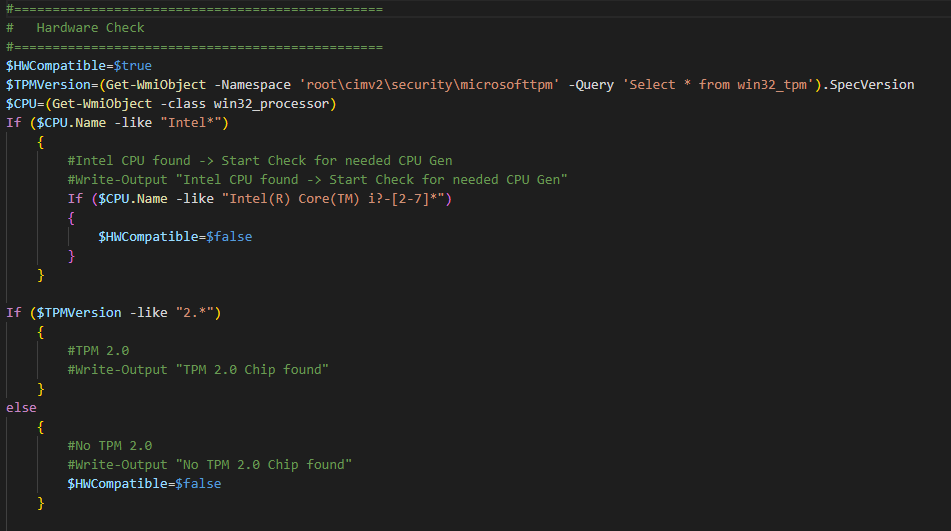
The Windows Version (Win 10 vs. Win 11) will be automatically selected, based on Hardware support. Since the only devices, that we still want to be able to install Windows 10 have Intel Core CPUs form Generation 2 – 7, i only check for this and an enabled TPM 2.0 Security Chip here.
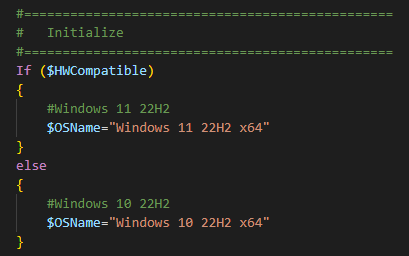
Once the Launcher checked the HW Compatibility, it fills a global Variable “StartOSDCloudGUI” and hand over the job to OSDCloud with an set ZTD Option, so it won’t ask for permission to wipe the SSD, so be careful during testing.
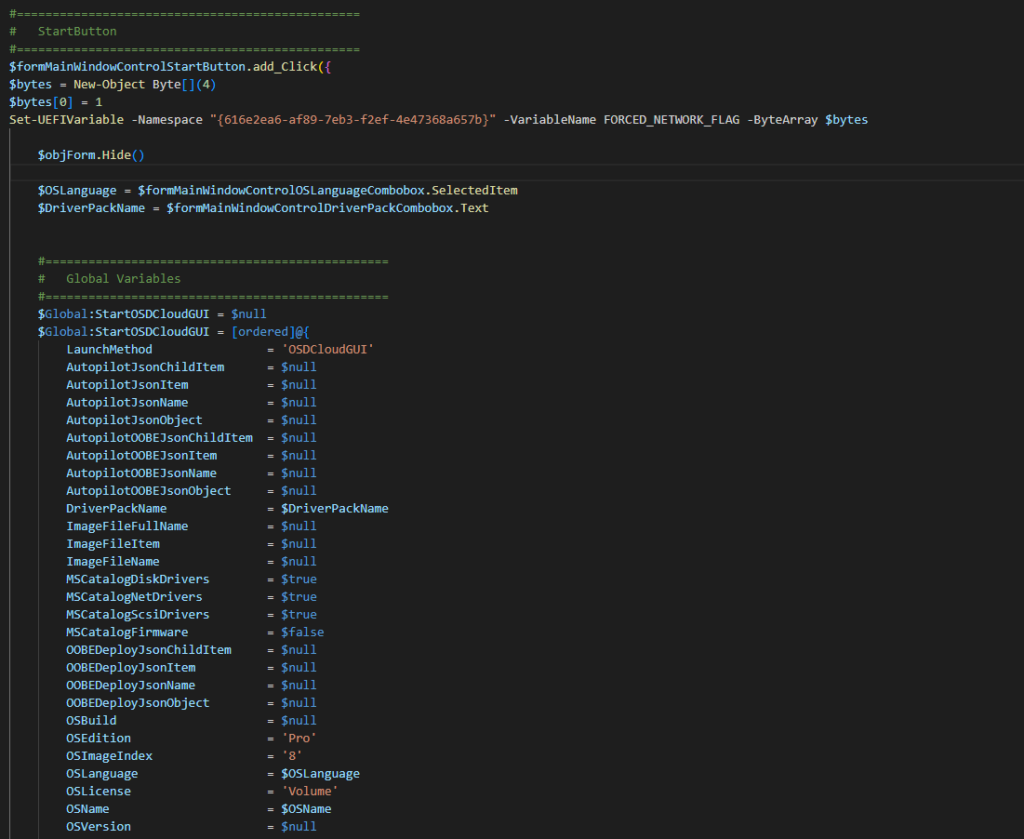
If you want to know more about this, let me know in the Comments and I will be happy to show you more details if wanted.
Leave a Reply