A few years ago, when we started to use Windows Autopilot to enroll our first devices, we quickly saw the need for a Companion App to handle GroupTags for our different Enrollment types like “normal” user-driven enrollments or different Pre-provisioning scenarios (formerly White Glove). So we started with the official App from Michael Niehaus: microsoft/WindowsAutopilotCompanion: Sample companion app for working with Windows Autopilot “White Glove” workflows (github.com)
We started to modify the App to our needs, switched from ADAL to MSAL, added a few small different things, but realised quickly that is is much work to keep the App up to date, especially as we needed to support Android and iOS and struggled with Conditional Access Policy’s that required compliant devices, etc. I have uploaded the last state of the App with my adjustments to my GitHub if you are curious to check it out, but keep in mind I have not updated it for around 2 years… Autopilot-Companion/Xamarin App at main · mmeierm/Autopilot-Companion (github.com)
Since we were searching for an easier solution, we came around Microsofts PowerApp Platform and thought, this would be the ideal basis for our “new” Companion App.
Power App
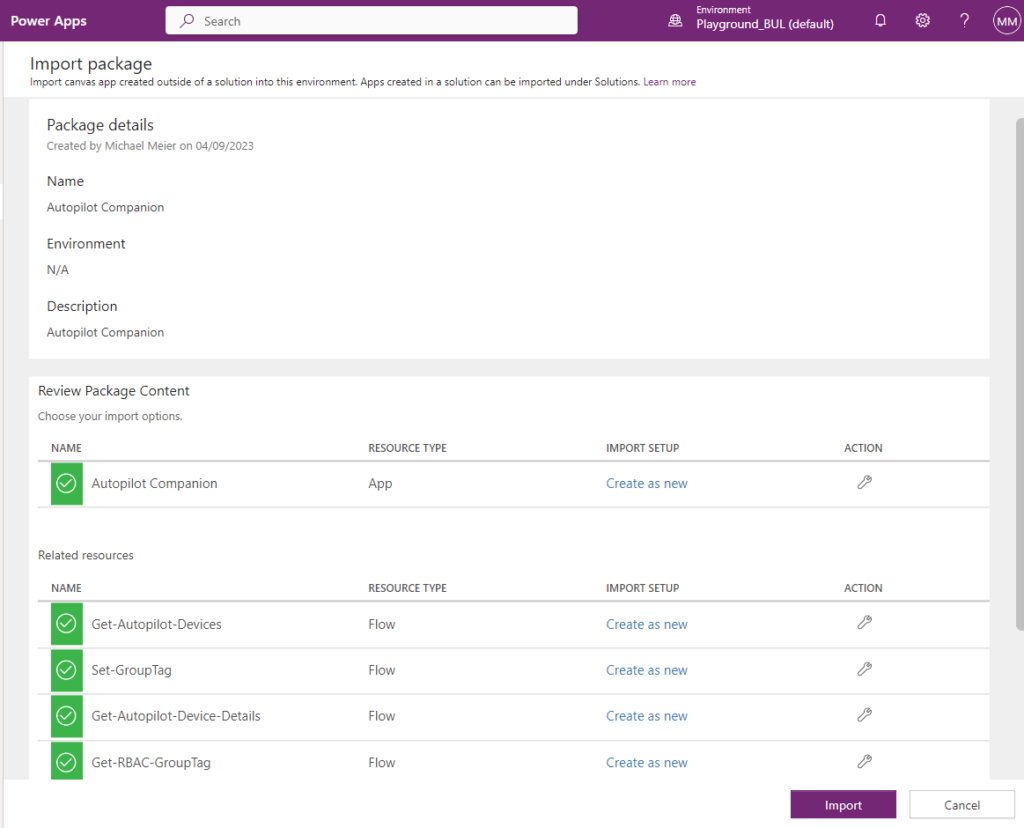
I uploaded the exported Power App that contains all needed Power Automate Flows to GitHub: Autopilot-Companion/PowerApp at main · mmeierm/Autopilot-Companion (github.com)
First step to do is to import the Power App in https://make.powerapps.com/, this will create the Power App and also the Flows:
App Registration
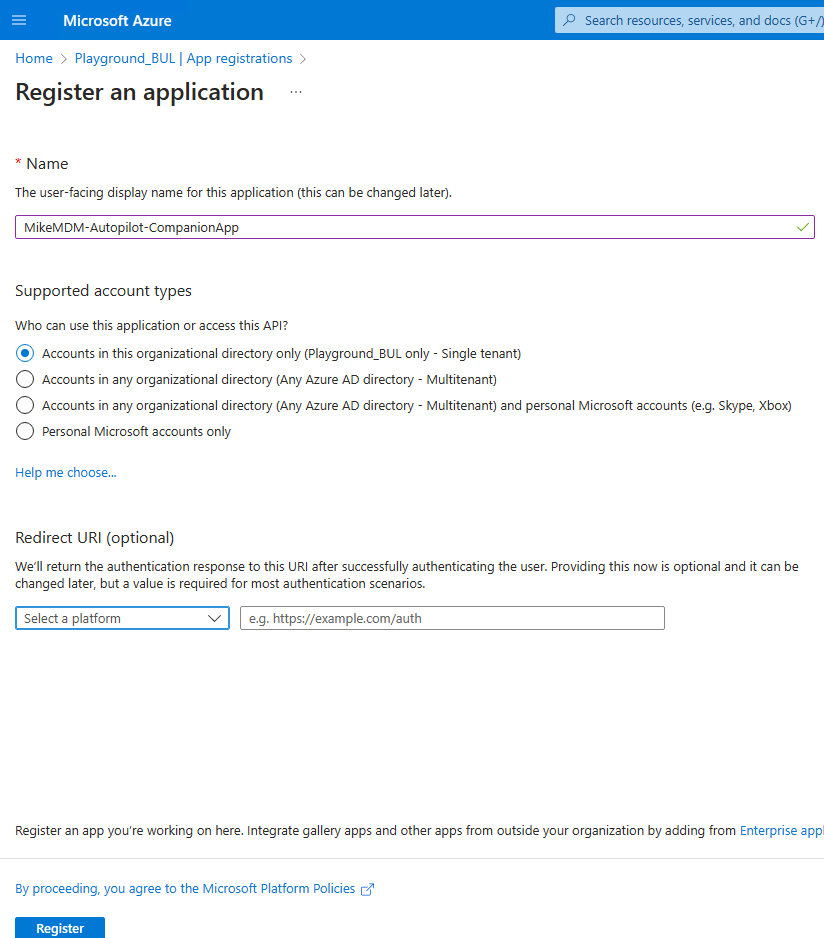
In the next step, we need to create an Azure App Registration to allow our App access Autopilot via Graph API. We can simply create a new App Registration, give it a name and go to the API Permissions
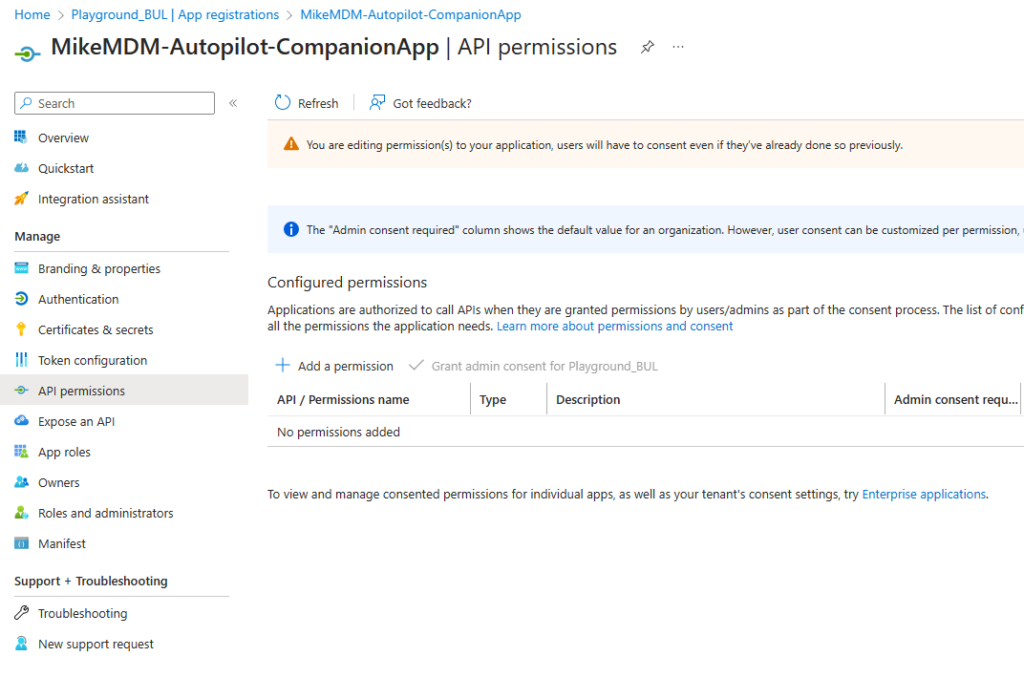
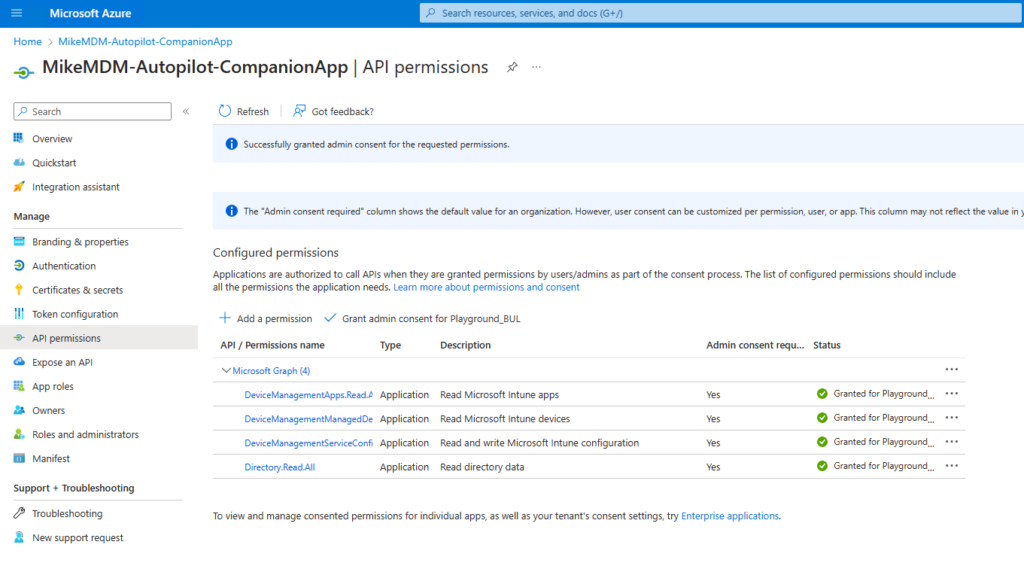
We need the following permissions as type Application assigned:
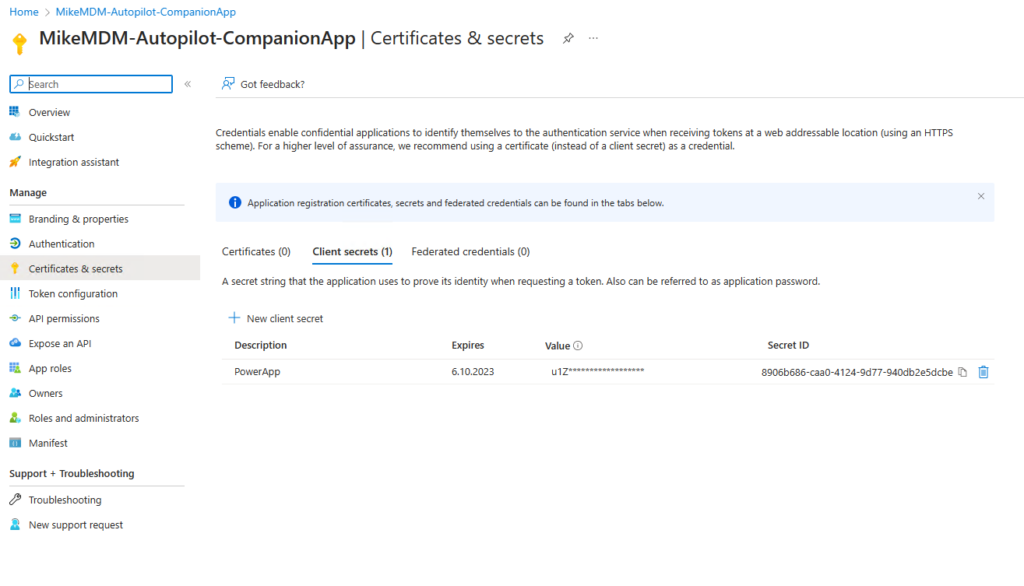
Last we can now create the Client Secret, that we use in the Power Automate Flows, you can also create a Certificate based solution, but for this Blog to keep it easy i will show it with a Client Secret. Make sure you copy the Secret after creation, as we will need it later and you can view it after saving.
Power Automate
With the previously created App credentials we can now finally adjust the Flows to use our freshly created App Registration. We have to modify every flow, as it currently contains placeholders for the Credentials and also they are imported in a disabled state. First we locate the imported Flows in https://make.powerautomate.com/
We should find 7 imported Flows:
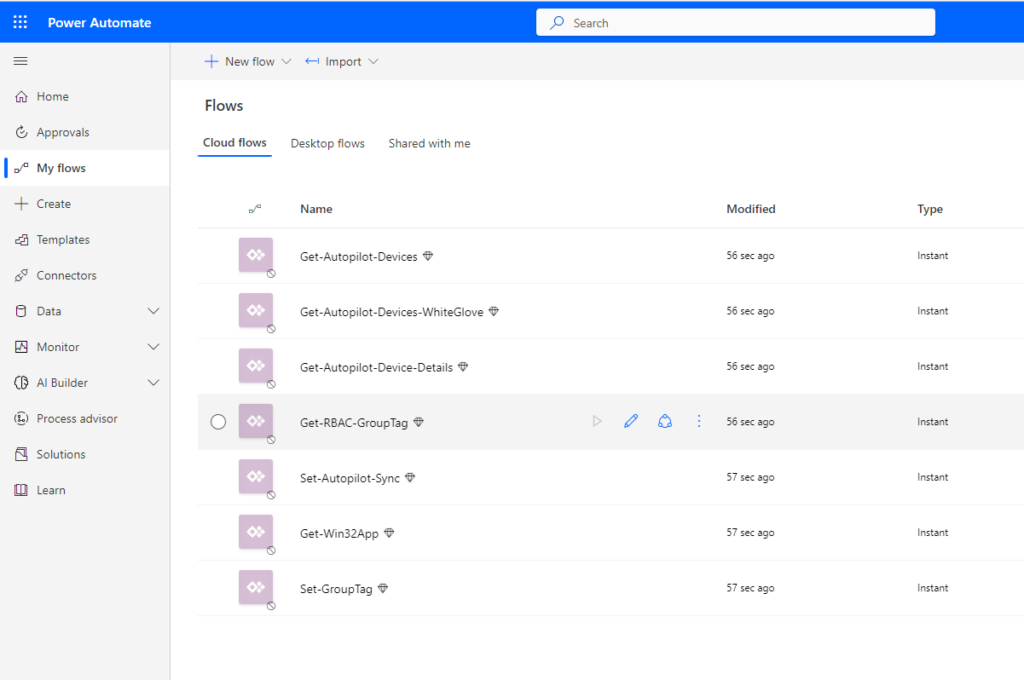
To modify the Credentials we need to have a look at every “HTTP” step in every Flow and change the Placeholders (Tenant ID, Client ID and Secret) with the appropriate values.
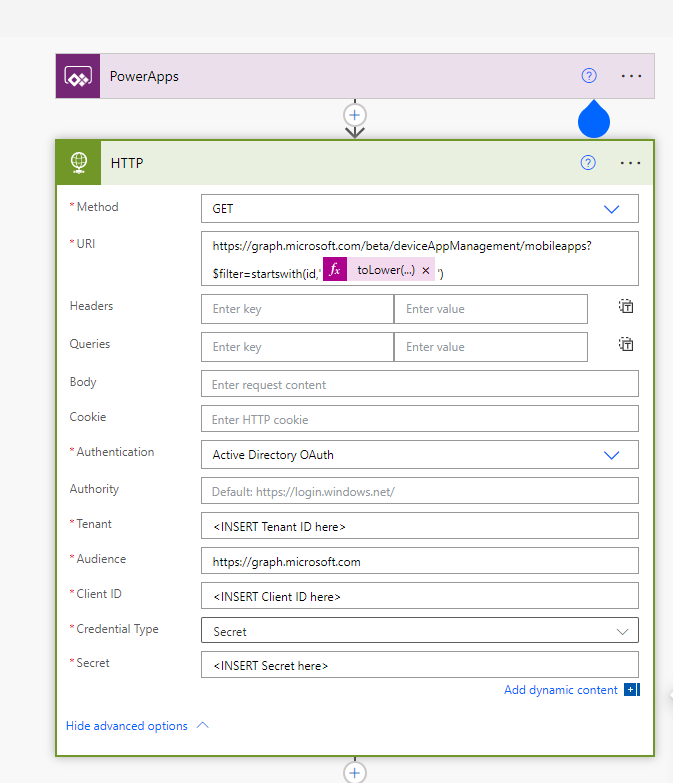
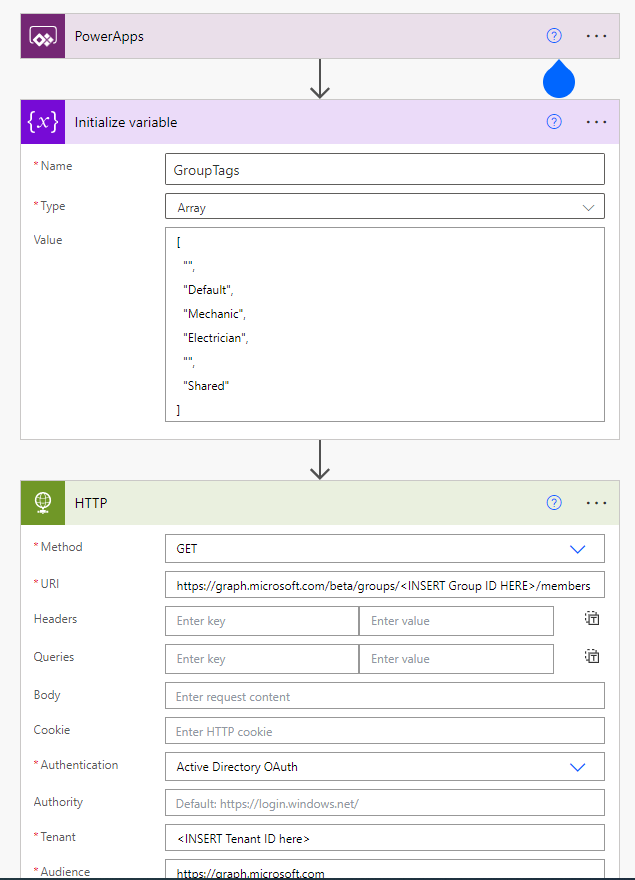
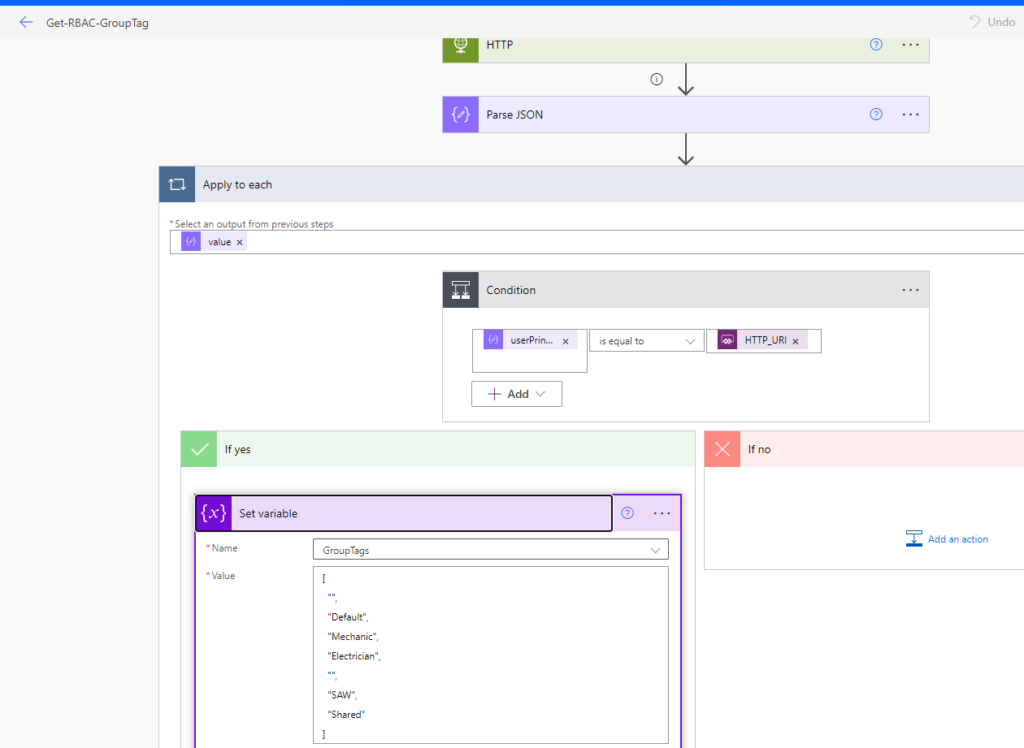
One special Flow is the “Get-RBAC-GroupTag”, in this we can change two additional Values, the first thing is the list of visible GroupTags for all Users in the “Initialize Variable” Step and also the AzureAD Group ID of a Group of Users that should see a different set of GroupTags in the “Set variable” step.
Power App
At the first start of the App, you will be asked to allow access to “Office 365 User”, which is used to show the Profile Picture in the top left corner

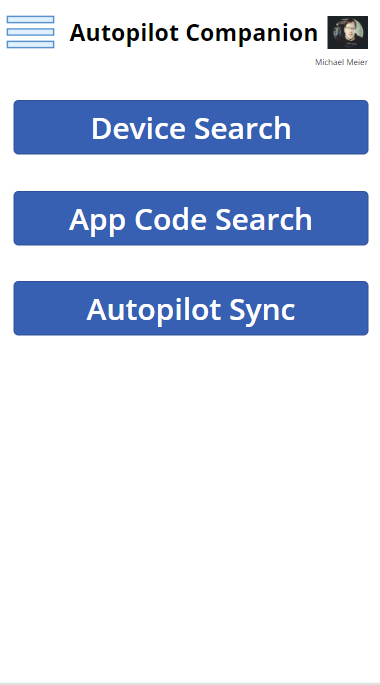
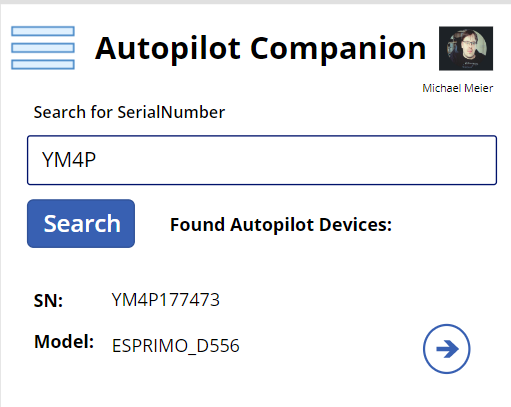
What can we now do with the App? The App always starts with the Device Search Page, where you can directly type in a Serial Number to search for a Autopilot Device (Search uses a startswith filter). You can also use of of the two Scan Buttons, the Scan Barcode Button will allow you to scan a SerialNumber in form of a Barcode from for example the Box of a new Laptop, the Scan WhiteGlove Button will use the QR Code shown during the Pre-Provisioning Process to search for the device
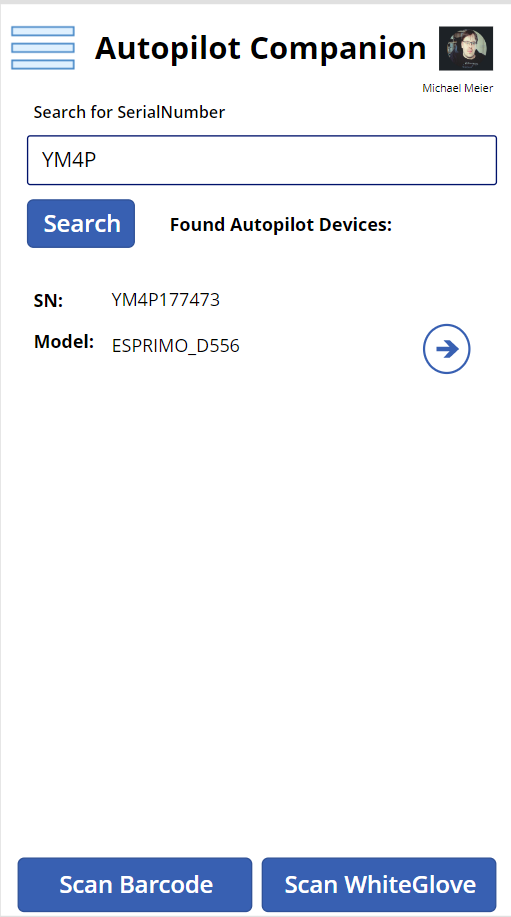
Once you found a device, you can select it and change the GroupTag or show additional device details
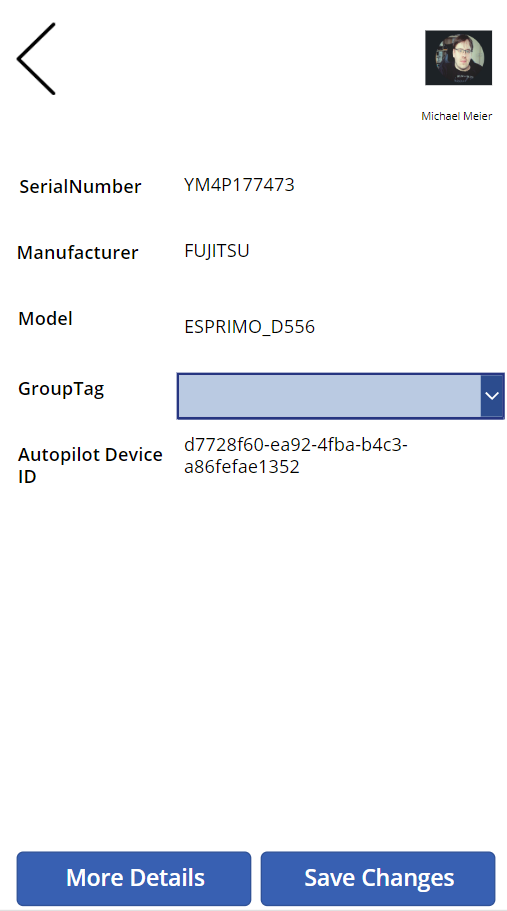
Once you saved the changes you will get back to the device search. Here you can also open the menu and select one of the other options
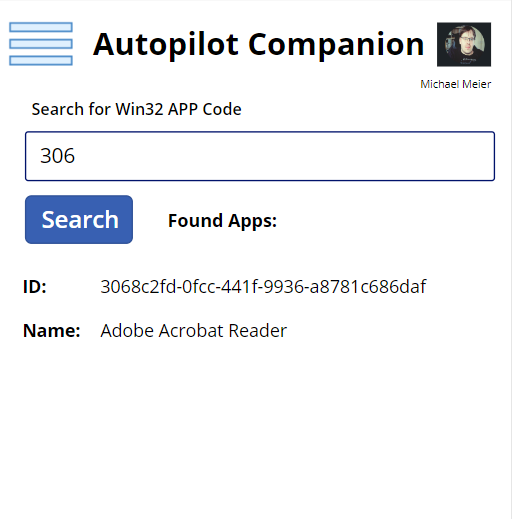
In the App Code Search, you can do one really cool thing, you can search for a Win32 App in Intune by the ID, which means, you can use it to troubleshoot which app failed to install during ESP Phase in Autopilot
Leave a Reply