Based on an old Article from Oliver Kieselbach about automating Autopilot Uploads, I wanted to share you my solution to this, slightly modified and improved: Automation of gathering and importing Windows Autopilot information – Modern IT – Cloud – Workplace (oliverkieselbach.com)
In his Article he described a way, where the Hash was collected in form of .csv Files on a Azure Blob Storage that were uploaded form the clients, which works good, but requires a good working logic in the Runbook to handle multiple requests at the same time and requires the Runbook Script to run in a time based recurrence, I use a Webhook and a System Managed Identitiy to make this a lot simpler. Also i switched from the Teams based reporting to a LogAnalytics Custom Log, that is in my opinion easier to handle for Reports like in PowerBI
Lets start with the needed Azure Ressources, the first thing we need is an Azure Automation Account that will run our PowerShell based Runbook Script. To create this, we first need to have access to a Subscription, then we can simply add it from the Azure Marketplace:
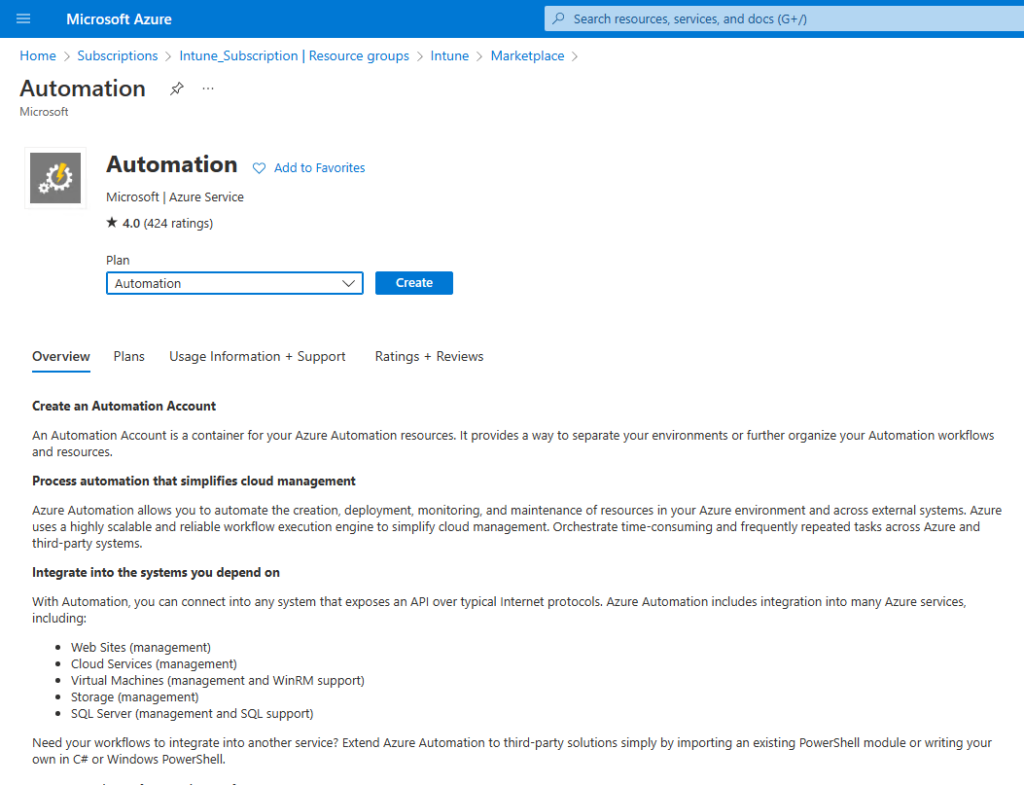
At the Basics give it a name and select the Region that you need, in my case West Europe as i’m in Germany
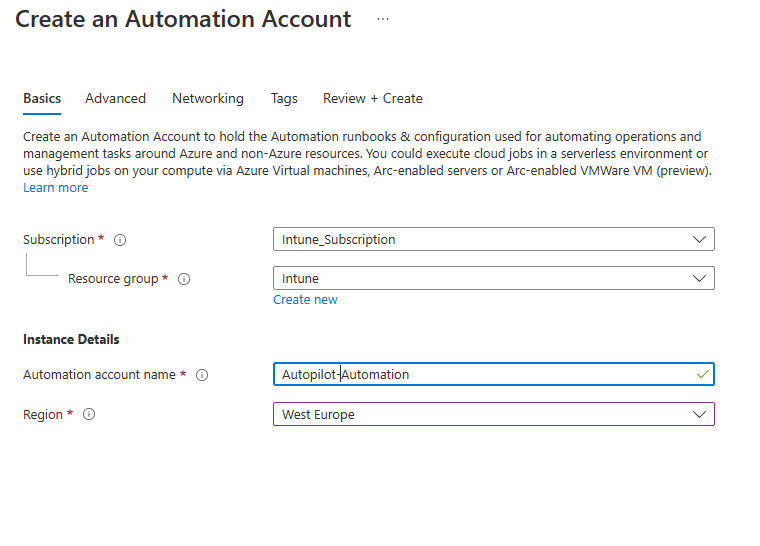
In the Advanced Tab activate the System assigned Managed Identity, as we will need it later (You can also create the Identity afterwards if you already have an Automation Account)
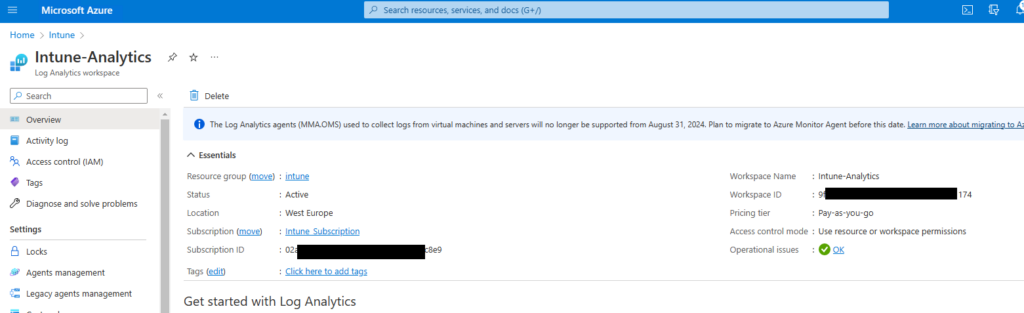
Additionally we need a Log Analytics Workspace to collect the results of the Imports for troubleshooting and reporting
The next step is to assign the Managed Identity of the Automation Account the needed permissions. Unfortunately this is currently only possible via Graph API and not yet via Azure Portal. Microsoft published a good Article for this: Grant Graph API Permission to Managed Identity Object – Microsoft Community Hub
Here a Script Sample that just needs the Object ID from the System Managed Identity in the last command to assign it the Role “DeviceManagementServiceConfig.ReadWrite.All” which is needed to add Autopilot Devices
Install-Module AzureAD -Scope CurrentUser
Install-Module Microsoft.Graph -Scope CurrentUser
Connect-MgGraph
Connect-AzureAD
$PermissionName = "DeviceManagementServiceConfig.ReadWrite.All"
$GraphServicePrincipal = Get-AzureADServicePrincipal -Filter "appId eq '00000003-0000-0000-c000-000000000000'"
$AppRole = $GraphServicePrincipal.AppRoles | Where-Object {$_.Value -eq $PermissionName -and $_.AllowedMemberTypes -contains "Application"}
New-AzureAdServiceAppRoleAssignment -ObjectId <InsertManageIdentiyID> -PrincipalId <InsertManageIdentiyID> -ResourceId $GraphServicePrincipal.ObjectId -Id $AppRole.IdOnce this is done, we can add the Autopilot Runbook with the Script that I uploaded to GitHub: Scripts/Runbook.ps1 at main · mmeierm/Scripts (github.com) This Script handles the Upload to Autopilot and the Reporting to the LogAnalytics Workspace
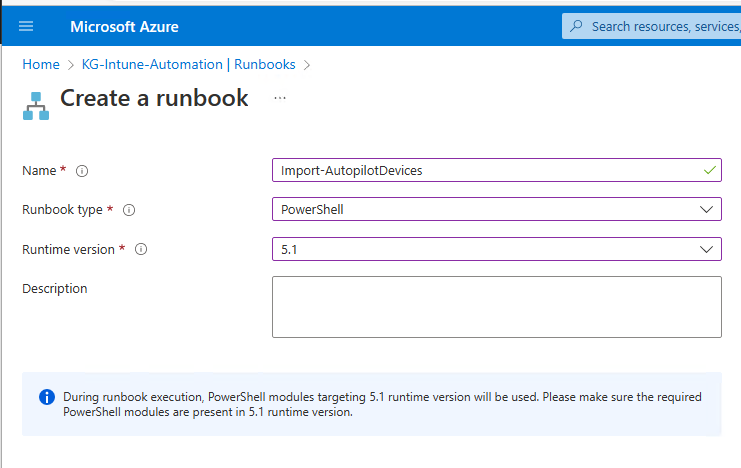
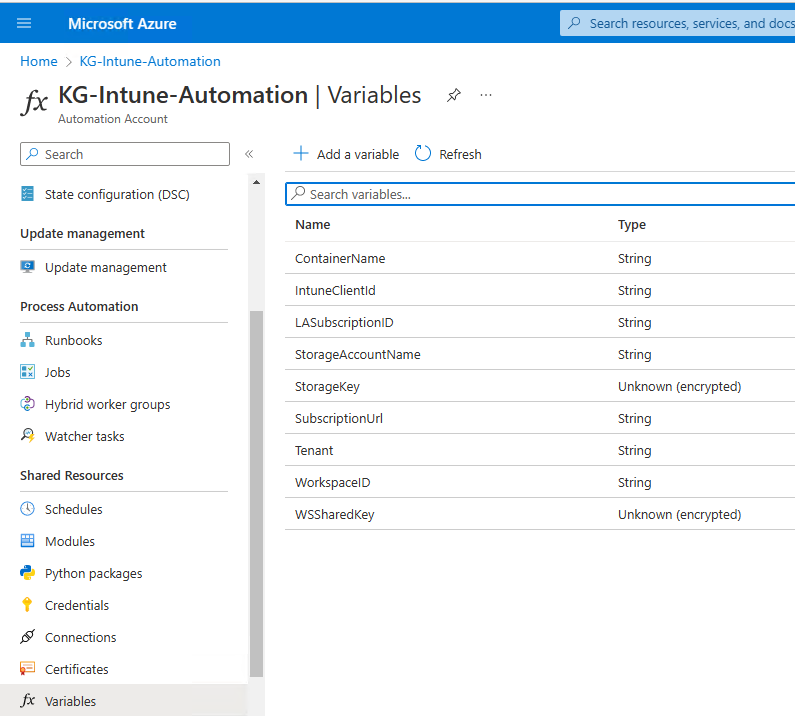
Then we have to add the Runbook Variables for the LogAnalytics Workpace, we need the following three Variables: WorkspaceID, WSSharedKey, LASubscriptionID, we get all from the Log Analytics Workspace itself
Finally we can create the Webhook itself that we use to start the Runbook and transfer the Hash from the Client to Azure. Important, once you create the Webhook you will only see the URL that you will need in the last part for the Client Side Script
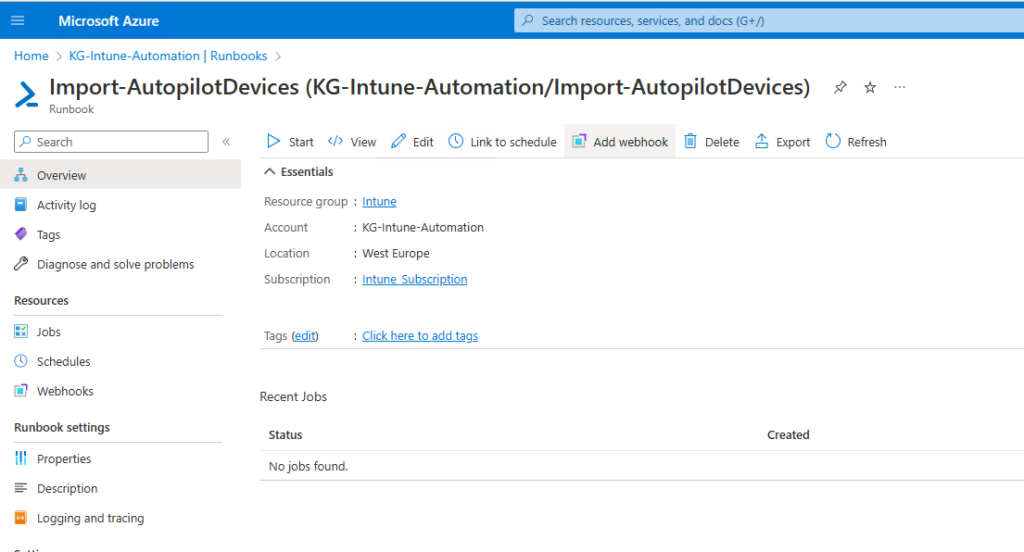
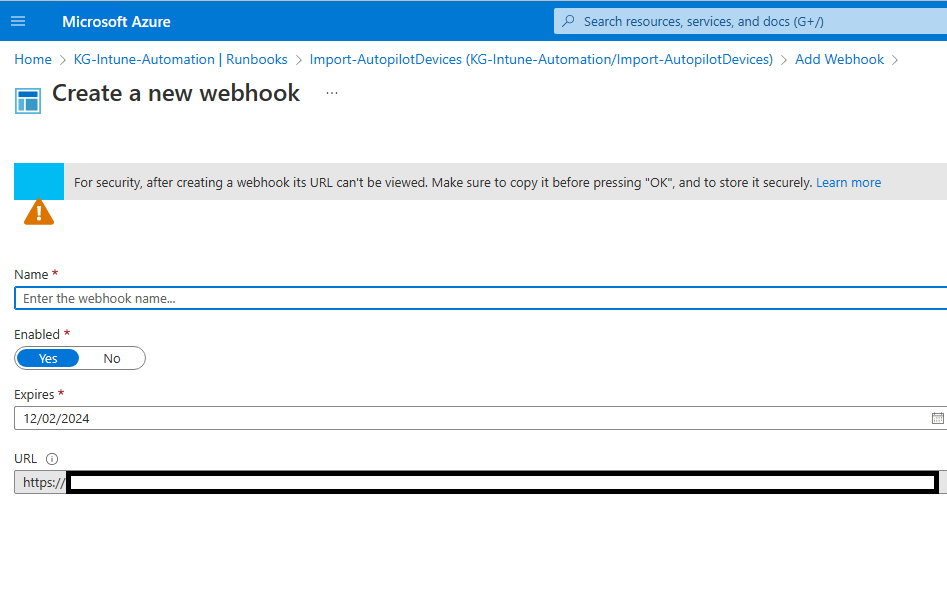
The last thing we have to do is he Client Side, as described in my last Autopilot Blog (Can you create a Autopilot Hash from WinPE? Yes! – Mike’s MDM Blog (mikemdm.de)), we can again use the OA3Tool and even use it in WinPE if we so desire. I created a sample Script on my Github, where you only need to replace the URL with the one that is visible when creating the Webhook: Scripts/CollectHashandUpload.ps1 at main · mmeierm/Scripts (github.com)
Leave a Reply