Have you ever wondered if you can harvest the Windows Autopilot Hardware 4k Hash from WinPE like used in MDT/SCCM or similar Deployment Systems? Yes, it is absolutely possible, when you keep an eye on a few details that i will describe here.
First thing that you may notice, you can’t use the official Microsoft Script to gather the Hardware Hash, as it uses a WMI Class (MDM_DevDetail_Ext01)that is not present in WinPE and i also was not able to get it to work in WinPE.
So what now to do? We can use the OA3 Tool from the Windows ADK. Michael Niehaus has a very good article about the hardware hash published a while ago, so i will not go into details here, what it is and what the OA3 Tool is. You can check out his findings here:
Connect the dots: Reverse-engineering an Autopilot hash – Out of Office Hours (oofhours.com)
To get the Hardware Hash using the OA3 Tool, we can simply use the following parameters:
oa3tool.exe /Report /ConfigFile=.\OA3.cfg /NoKeyCheck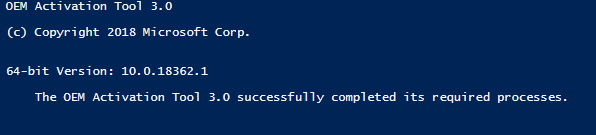
I uploaded the needed Config Files and an example Powershell Script to create a csv File, to GitHub for you:
Scripts/Autopilot at main · mmeierm/Scripts (github.com)
One thing that you have to consider if you want to use self deploying Autopilot Profiles is, as you are creating the Hash (which is basically just a Hardware Inventory) only contains Hardware that is found at the moment of the Hash creation. This means, if you will run this script in WinPE without modifications, you will end up with 4k Hash without TPM Info, and therefore you will get an error in Autopilot if you try to assign a Autopilot Profile that requires a TPM 2.0
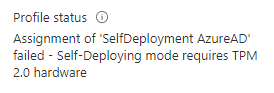
So what now? After searching around about how Windows implemented the TPM Module, i found an Article from German BSI (Work Package 5: TPM And “UEFI Secure Boot” Analysis (bund.de)). With this document, i was able to see, that we are missing one critical file in WinPE in order to get TPM to work.
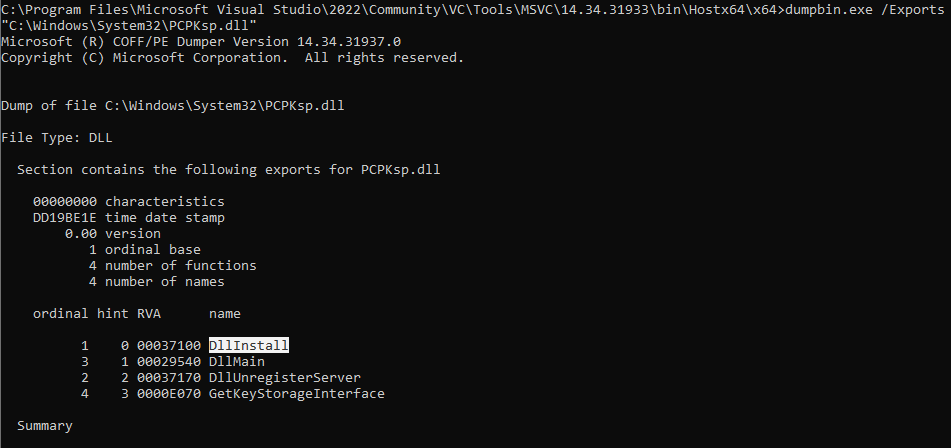
The PCPKsp.dll, which is part of the Key Management System.
But simply copying this file from a Windows 10/11 Client to the RAMDisk of WinPE (X:\Windows\System32\PCPKsp.dll) is unfortunately not enough. After digging around with dumpbin from Visual Studio (DUMPBIN Command Line | Microsoft Learn) i eventually found the needed function to get it to work, we need to call it via rundll32 from within WinPE:
So by adding this part to your script, we are able to get a Hash that contains the needed TPM Infos, so that we are able to assign a self deploying Autopilot Profile (I would recommend to use the PCPKsp.dll from a Windows Installation with a similar OS Build as your WinPE)
#Check if File exists and we are in a booted WinPE Session
If((Test-Path X:\Windows\System32\wpeutil.exe) -and (Test-Path $PSScriptRoot\PCPKsp.dll))
{
#Copy File to WinPE
Copy-Item "$PSScriptRoot\PCPKsp.dll" "X:\Windows\System32\PCPKsp.dll"
#Register the File to be able to be used by the OA3 Tool
rundll32 X:\Windows\System32\PCPKsp.dll,DllInstall
}
Leave a Reply