Who don’t know these annoying assigned device groups in Entra used for example in Intune to exclude assignments for specific policies? Once created and assigned we tend to forget to remove the devices. This can lead to issues and security risks, if for example an excluded security policy needed to install a software, stays excluded even if it is no longer needed. Would it not be even better, if the user could add his devices on his own and an automation takes care, that the devices get removed automatically? Well, look no further…
Backend
The Backend of this solution consists out of my all-time favorite, an Azure Automation Runbook and an Azure Table Storage, to keep track of all devices in the groups.
Azure Table Storage
Let’s start with creating our Azure Storage Account, which will store the Table to keep track of our devices. To create the needed Azure Storage Account, we need to go to the Azure Marketplace and search for the “Storage account”.

Give it a unique name, to keep costs low, I went with LRS Redundancy, since the data is not too critical in my opinion
Modify all other option to match your requirements and create the storage account.
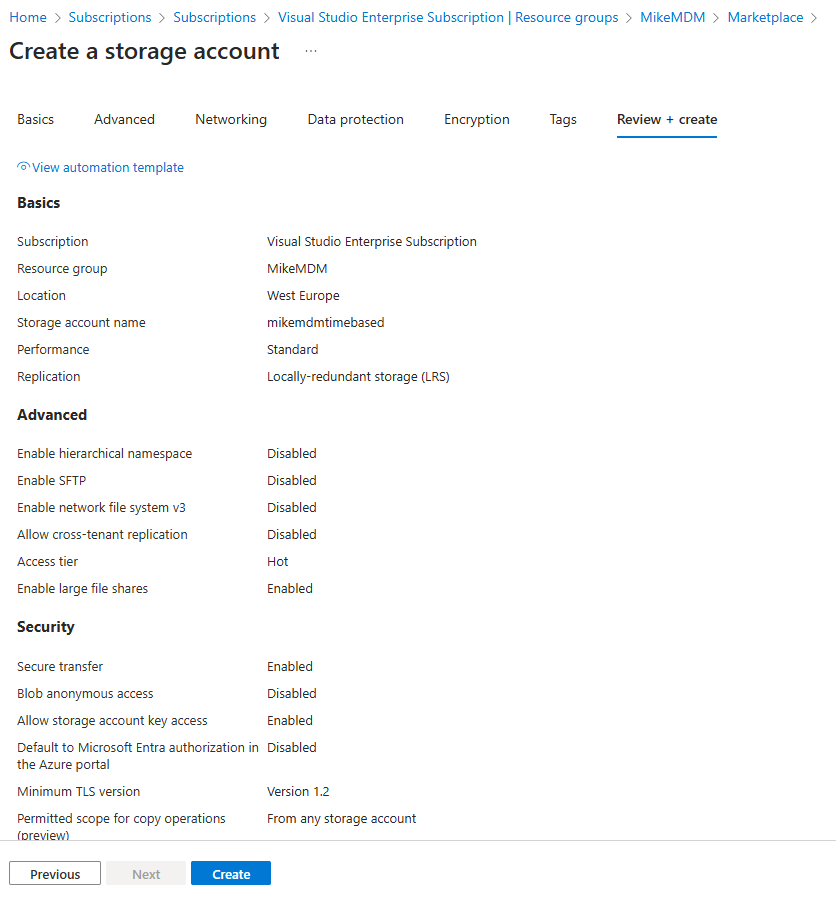
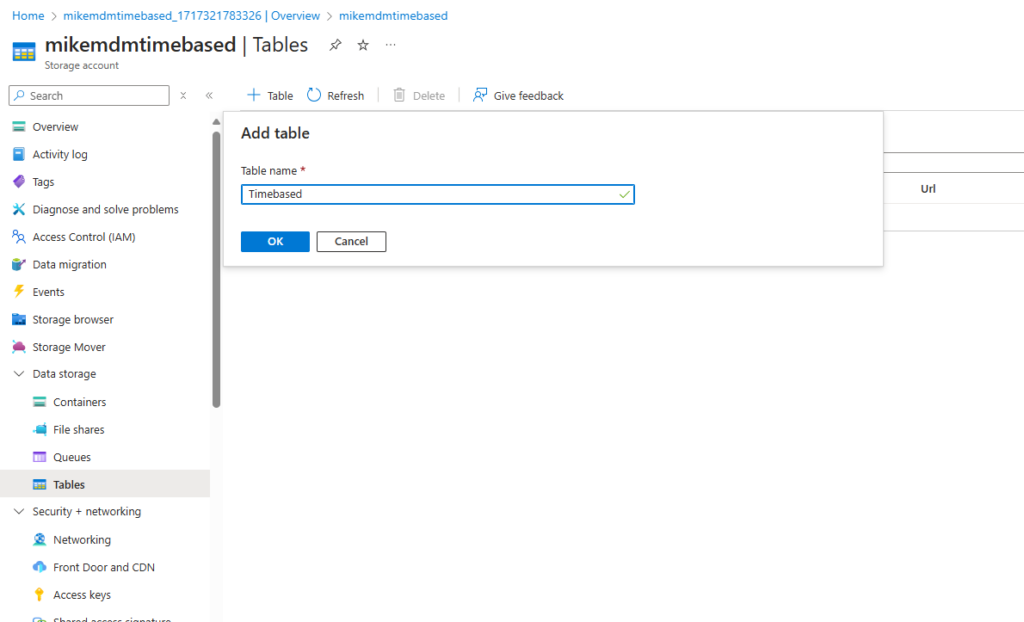
Once created, we can go to our storage account and create the needed table:
Azure Automation Account
Next, we need to create our Azure Automation Account, which will run our PowerShell script. To create it, we again need to go to the Azure Marketplace and search for the “Automation”
Give it a name and select the region:
And make sure to enable the system managed identity:
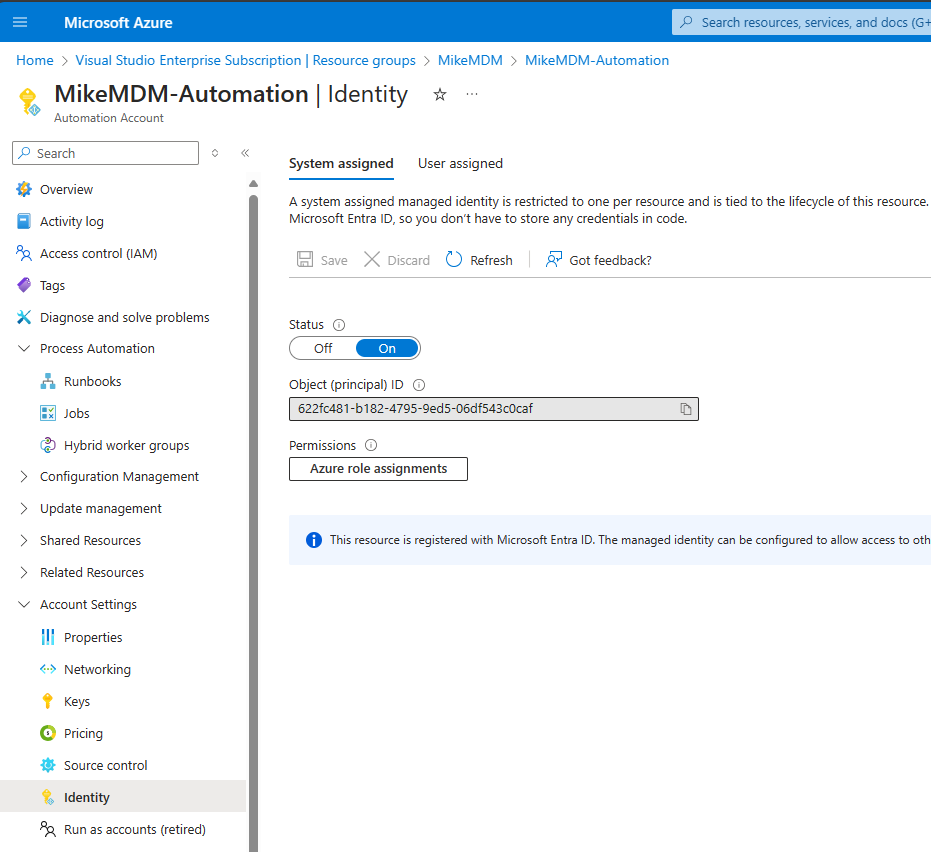
Graph API Permissions
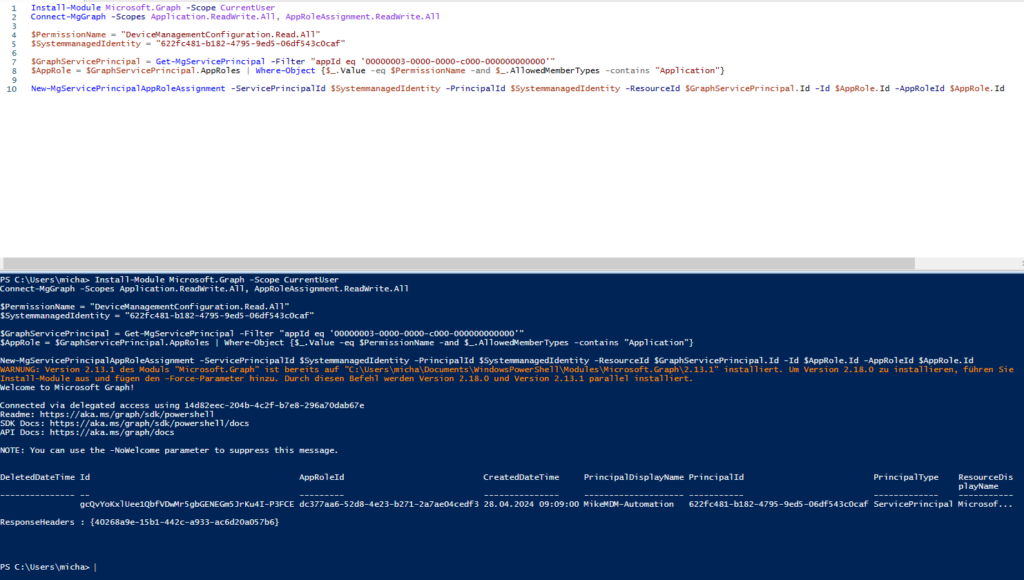
Once the Automation Account is created, we can assign the needed Permissions to the System Managed Identity. Just replace the ID from the Identity Tab of the Automation Account in the Script.
You can find the needed Script to assign the Permissions here: https://github.com/mmeierm/Scripts/blob/main/Time-based-Groupmembership/Add-Permission.ps1
The Script will add the following read permissions:
- GroupMember.ReadWrite.All
- Device.Read.All
Azure Automation Runbook
Now that we have all prerequisites, we can create the actual Runbook in our Automation Account:
Give it a name and select PowerShell as Runbook type:

In the actual Runbook, copy the code from: https://github.com/mmeierm/Scripts/blob/main/Time-based-Groupmembership/Runbook.ps1
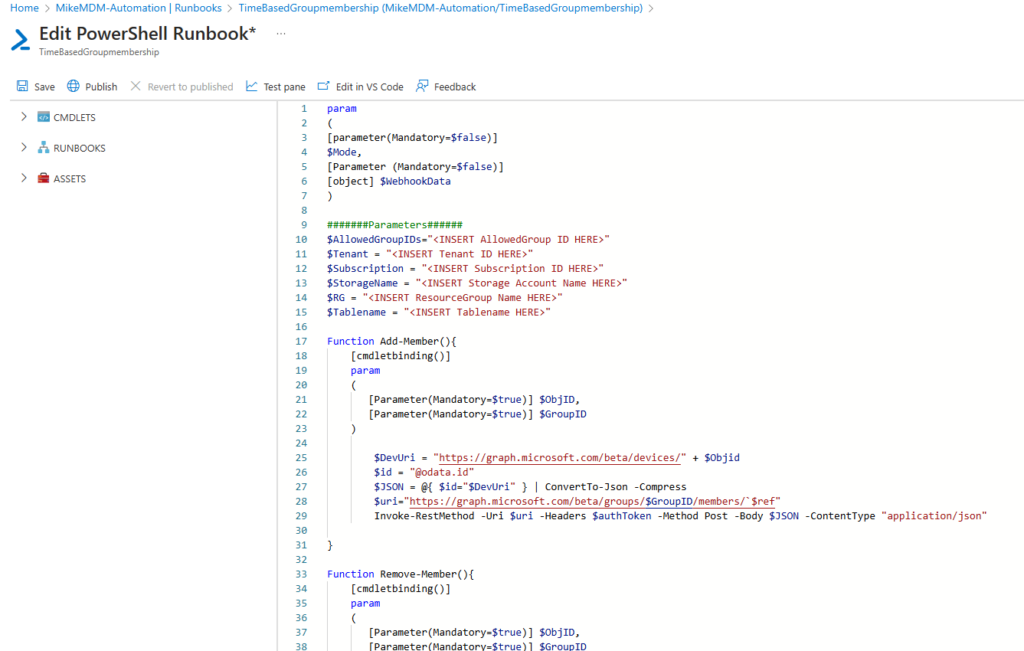
And modify the parameters in like 10 – 15 to match your environment

The variable “$AllowedGroupIDs” will contain a list of Entra Group IDs that are allowed to be used, since the GroupID will be transferred from the client, I want to make sure, you can only add yourself to groups that you approve.
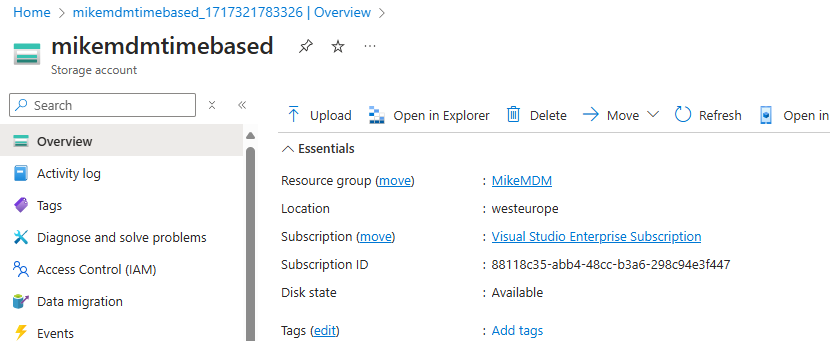
SubscriptionID, Storagename and Resource group name ($RG) can be found in the overview page of the Storage Account, and the Tablename is the name of the previously created Table (in the example “Timebased”):
Azure Permissions
One last thing, that we need to do before we can Publish our Runbook, is, we need to grant permissions of the Runbook Identity to the ResourceGroup and Storage Account. We need Read permissions on the Resource group level for the Automation account to be able to find the storage account:


Additionally, we need Storage account Contributor permissions on the Storage Account itself, in order to add and delete entries in the Table.

Azure Automation Runbook
Back to our Runbook, now that we actually have everything that we need to run our script, we can publish the Runbook and create our Webhook, that will be used to call if from our clients.
First let’s create the webhook, it will allow our client side script to add the users device into the group:

Give it a name, select the duration and make sure to copy the URL, since you can’t view it later, and we will need it on the client:
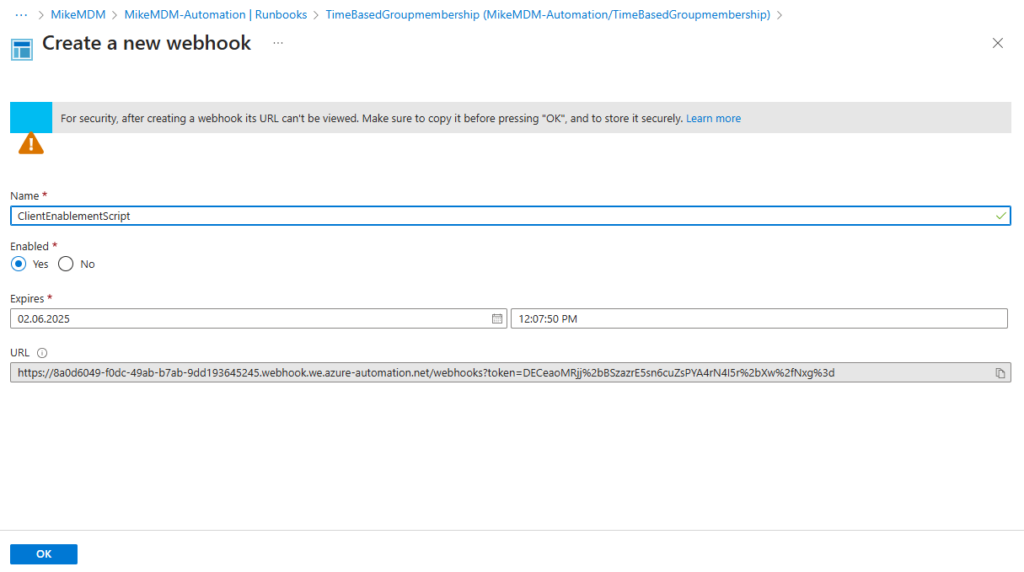
No need to modify any parameters, the Webhook data will be filled automatically, and the Mode will be needed later for the scheduled cleanup.

Next, we can create a schedule, when the script should verify which clients should be removed from the group(s). Select the schedule to match your needs, like hourly or daily and make sure in the parameters to set the Mode to “CleanUP”

Every time, the script runs in cleanup mode, it will check the table storage for all devices in the groups and will start the removal of devices that are overdue:

Client script
For the client side, I created a small PowerShell script, which will allow the user to add their device for either 1, 3 or 7 days to the group:
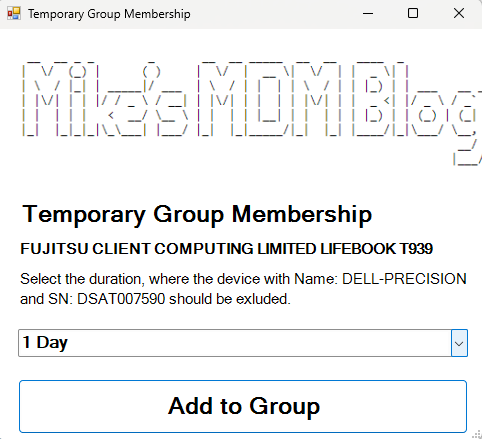
You can find the script here: https://github.com/mmeierm/Scripts/blob/main/Time-based-Groupmembership/ClientScript.ps1
You just have to add the Webhook URL from above and add the Group ID of an assigned Entra ID Gorup, where you want the client to be a member for the duration.

You’ll get the Group ID (Object ID) from the overview page of your group in Entra:

If you want, you can deploy this script as an available App in Intune Company Portal, as I described here: https://mikemdm.de/2023/03/08/install-win32-apps-visible-via-intune/ and here: https://mikemdm.de/2023/07/16/run-applications-in-intune-company-portal-on-demand/
Result
Add Devices
Every User that gets access to the client script can select the duration of the group membership:
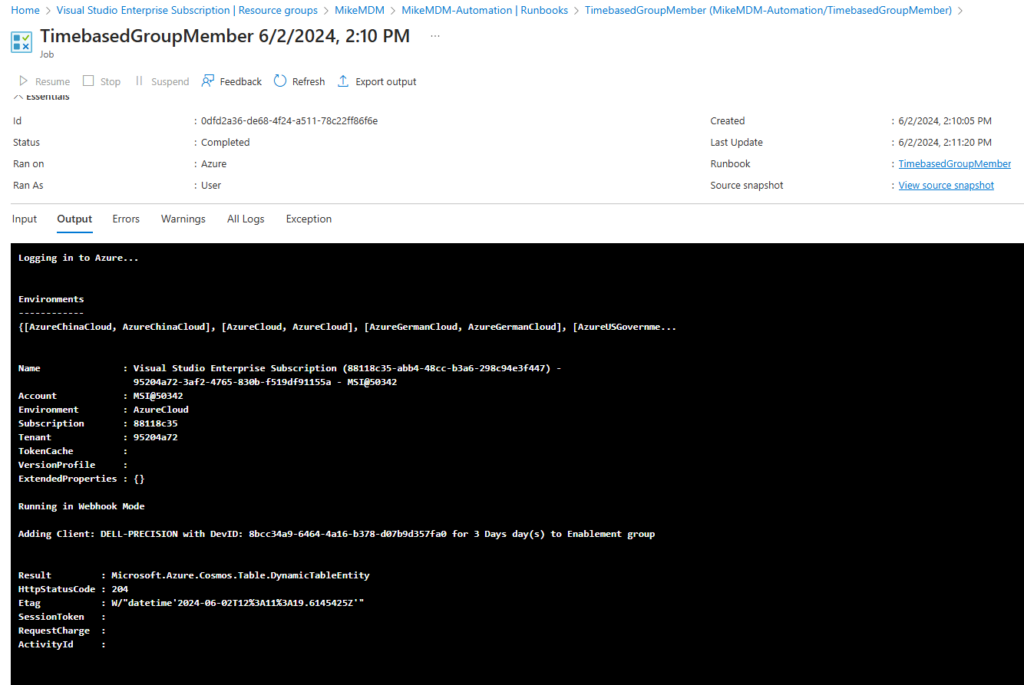
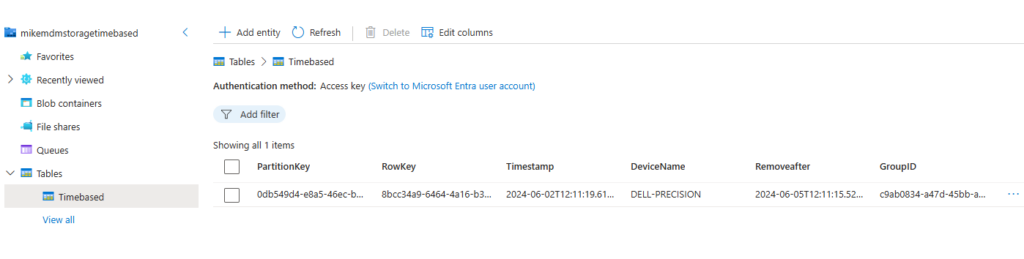
Once the Runbook was triggered, the client has been added to the Group and a new entry has been added to the table.
Cleanup
Now that we have a few devices in the table, we can watch the cleanup script removing the first device that should be removed:
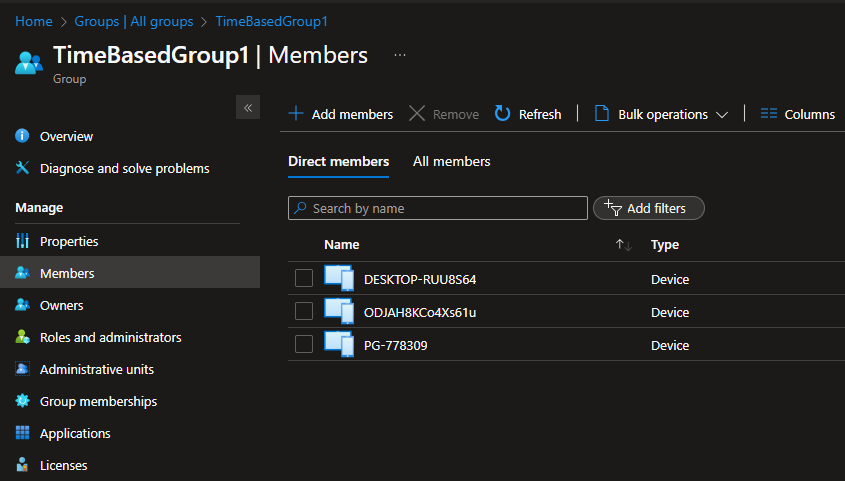
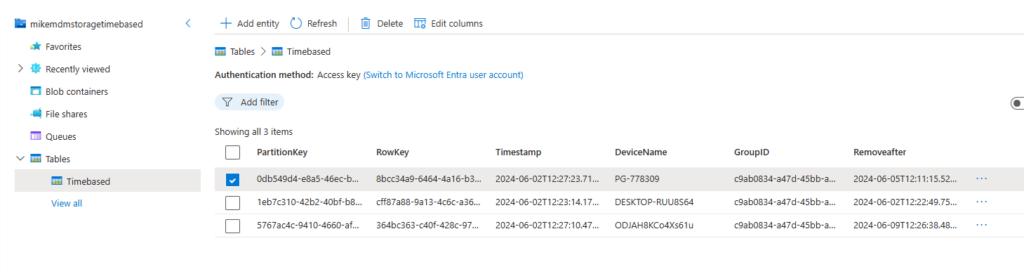
Let’s watch the next scheduled cleanup run:
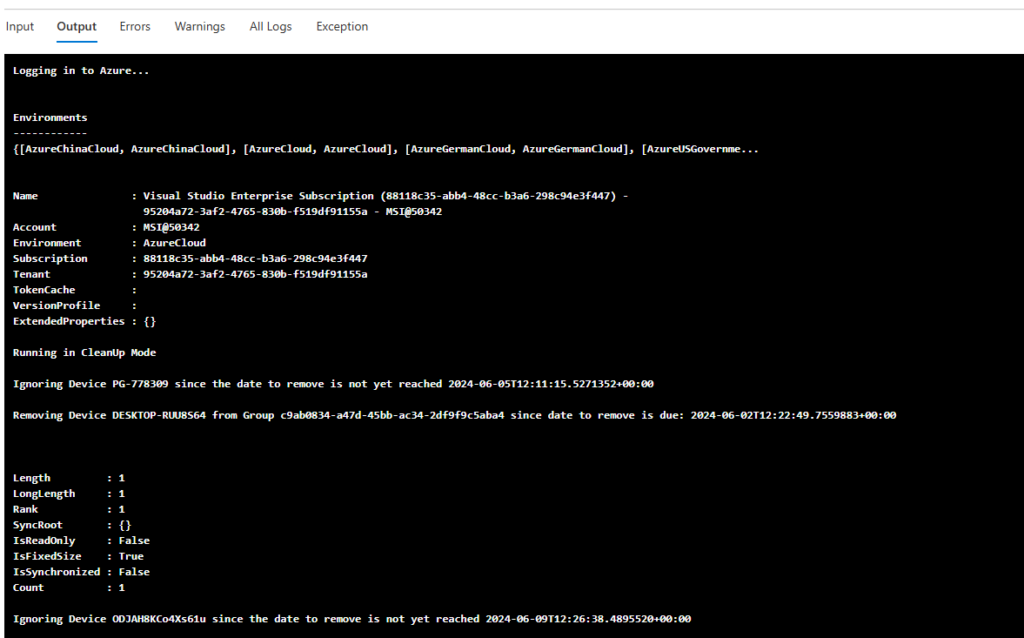
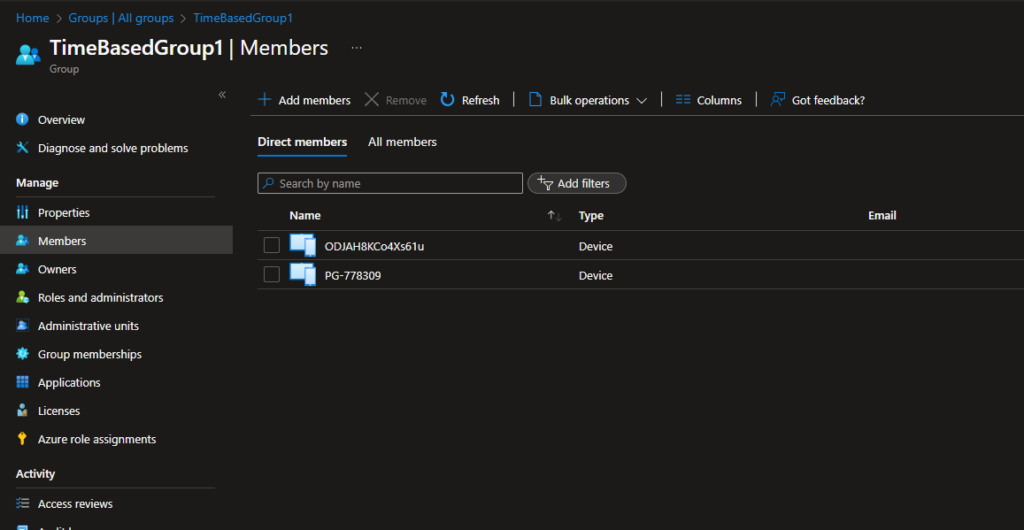
We can see, it correctly identified the one device that should be removed, and it ignored the other two that are still allowed to stay:

Conclusion
In my opinion, this little tool can help you to make sure that the users devices are just for a limited time in an exclusion group. In the next part, I will show you an additional part for admins, which will allow you to add a user’s device on behalf, without needed the user, while still leveraging the cleanup logic.
Leave a Reply