Today I want to give you a first look at the Intune Endpoint Privilege Management that is part of Intune Suite for one year with the March 2023 Intune release. Additionally, I want to show you the new support approved flow, which was added recently and allows for example the Helpdesk approving elevation requests for apps without specific rules.
What is a EPM solution doing?
If you haven’t worked with an EPM solution like BeyondTrust Endpoint Privilege Management, you may ask yourself, what is it doing and for what would I need it. Basically, on a high level it allows non-admin users doing defined things that normally would require admin rights. This includes allowing users to run vendor setups of applications that require admin privileges, but also running apps that require admin privileges for daily usage.
How to set it up in Intune
To start with Intune EPM, we need at least two new Configuration Profiles in the Endpoint Security blade. One to configure how EPM should behave and one or more containing the rules.
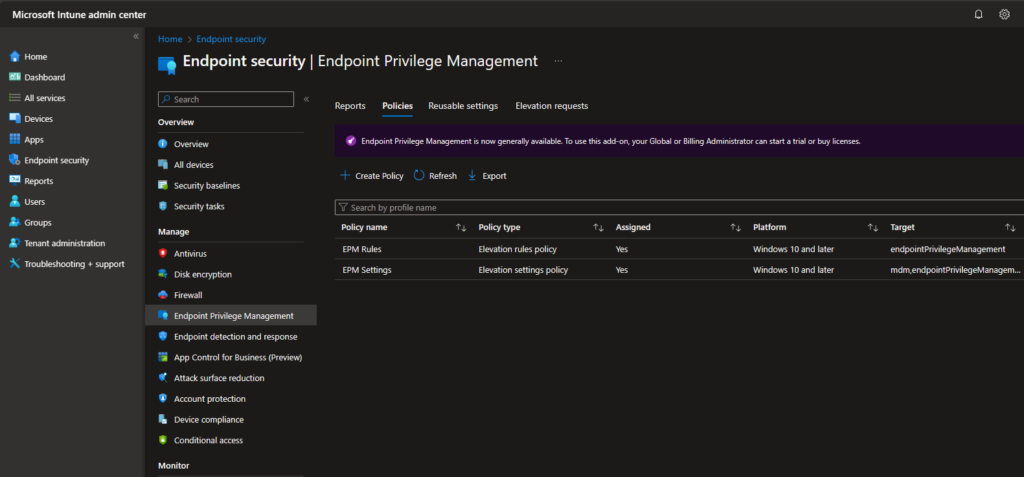
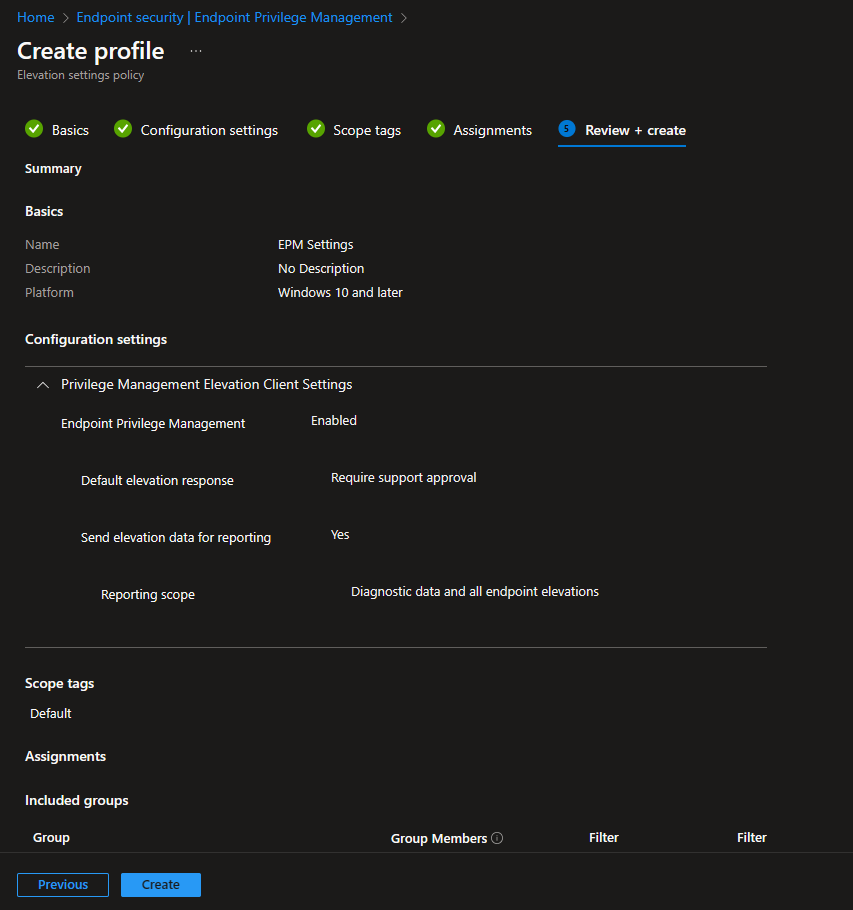
Settings Policy
Let’s start with the settings policy, give it a name:
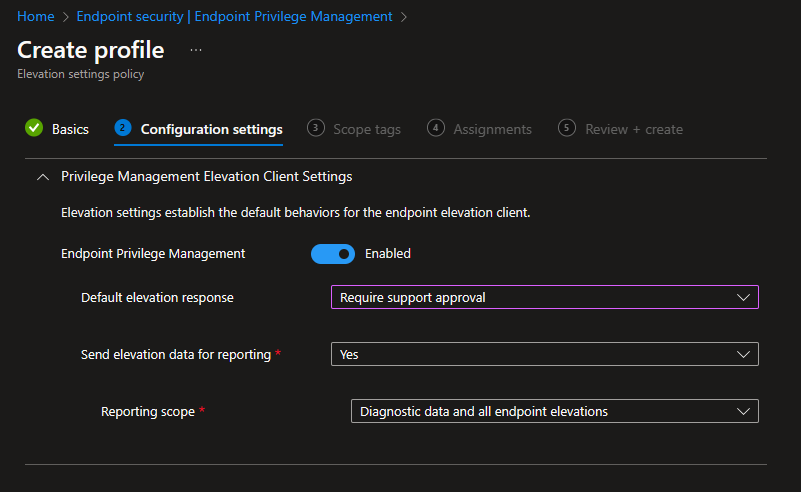
In the Configuration settings you can modify the settings to your needs. The first setting “Endpoint Privilege Management” is set to Enabled, to actually enroll the devices to EPM. This will actually trigger the dual enrollment of the devices into the new WinDC management service of Intune.
The “Default elevation response” is maybe the next most important setting here, as it controls how EPM behaves when there is no specific rule found for the requested executable. You can find the more information about this in the Microsoft Docs. I will use the new “Require support approval” setting which I will explain later. The last two settings control the reporting capabilities of EPM.
After the settings, do the usual stuff like Scope tags and Assignments:
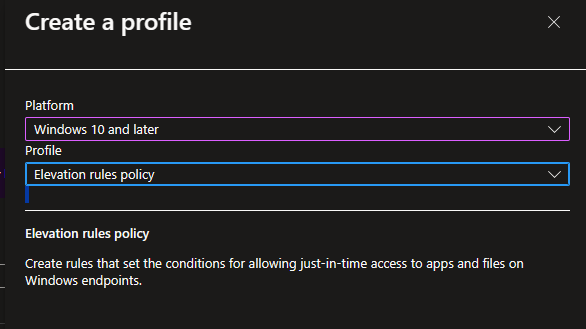
Rules Policy
Next, we should create a Policy that contains the actual rules, which controls which executables should be handled by EPM.
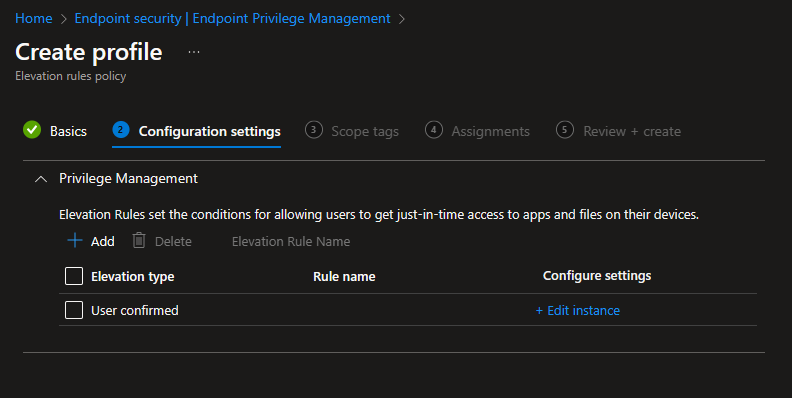
For each executable you need to specify what EPM should do with it (silently elevate, ask the user, or again go with the support approval flow), and define how to identify the executable (via File Hash or for signed executable via the used certificate.) Again check out the official docs for more information: https://learn.microsoft.com/en-us/mem/intune/protect/epm-guidance-for-creating-rules?WT.mc_id=317638
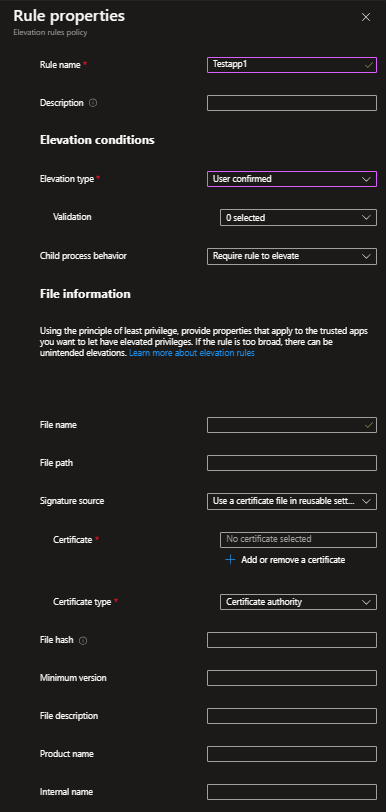
For this demo, I created three rules, one to silently elevate and two that the user has to confirm.
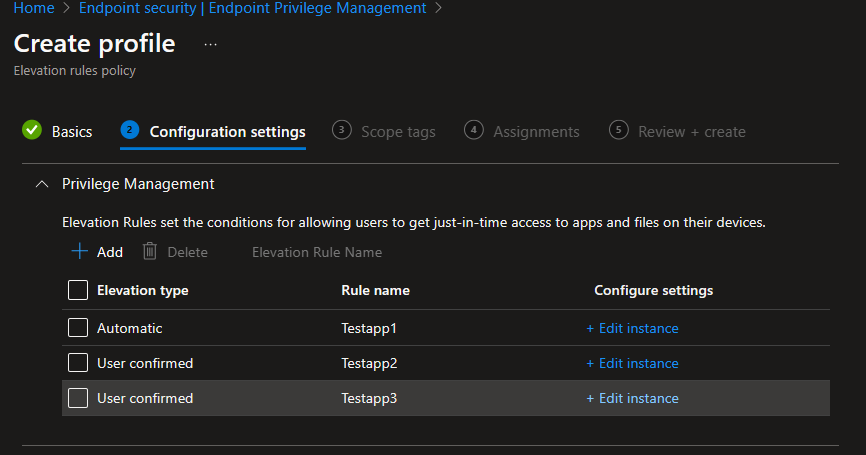
User experience
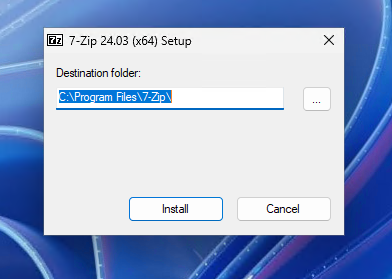
To showcase the different types of elevations, I added four test apps to my desktop that match the three created rules and a last one matching none of the rules. I used my all-time favorite 7-zip setup as a demo app, but you can imagine it replaced with every other executable.
Automatic scenario (Testapp1.exe)
The first scenario with the Testapp1.exe is the automatic elevation, which will simply automatically elevate the setup, so without any UAC message the app will run by double clicking it:
User approval scenario with Business justification (Testapp2.exe)
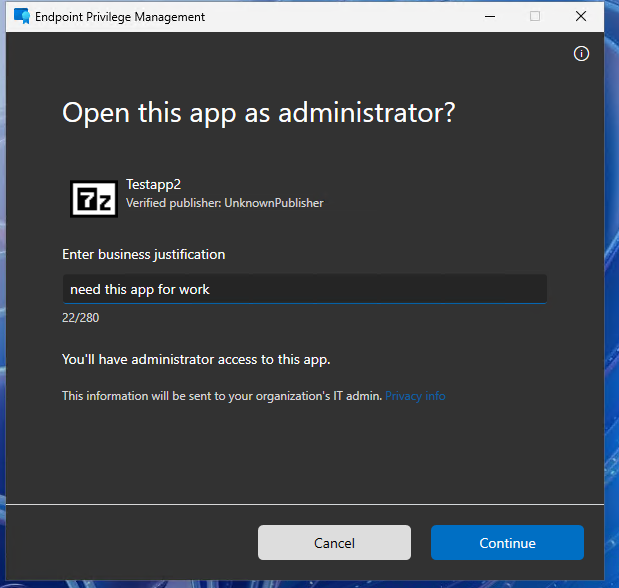
The second scenario with Testapp2, shows the User confirmed elevation with Business justification. The user starts the app with the “Run with elevated access” button in the right click menu, then he is asked for a reason and can immediately run the app.
User approval scenario with additional authentication (Testapp3.exe)
The third scenario again shows a user approved scenario, but this time without Business justification, but with an additional authentication, where the user has to enter his credentials one more time to make sure, it’s actually him / her.
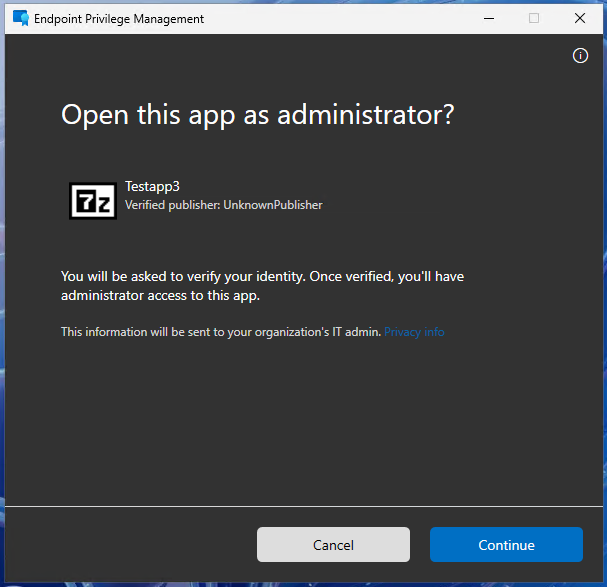
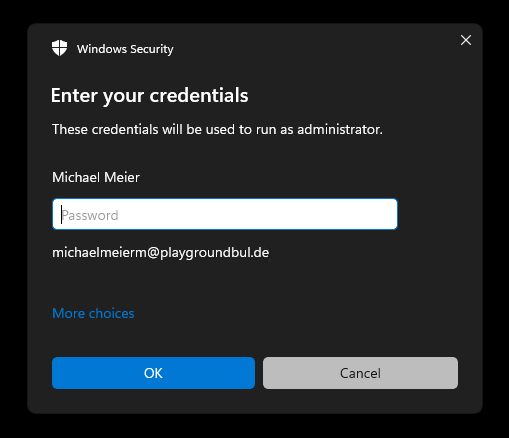
After successful authentication, the app again is elevated:
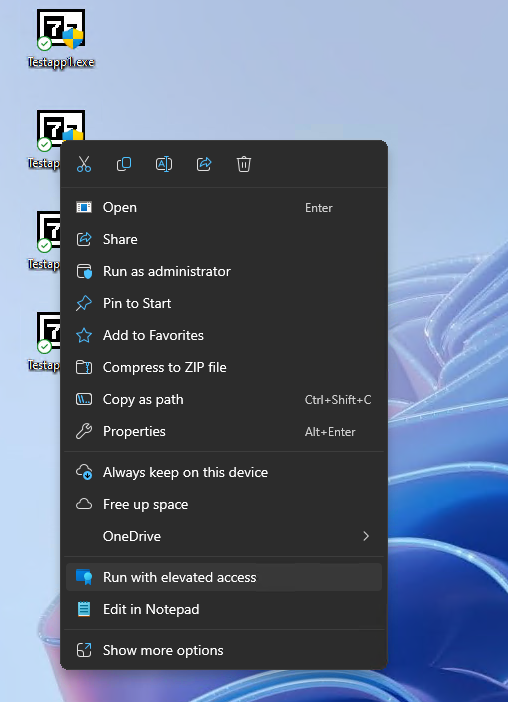
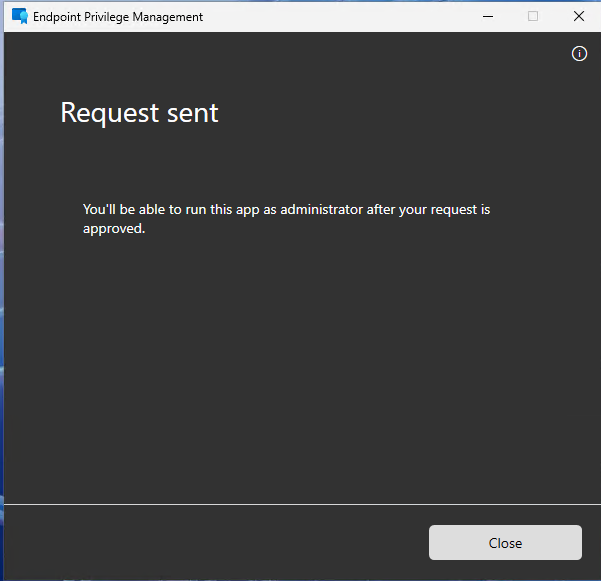
Support approved flow (Testapp4.exe)
The last scenario, that I want to show you today, is maybe the coolest option, that in my case fits all apps that are not covered by any specific rule. Since I selected support approved as the default or fallback option for all executables, I can request admin rights using the “Run with elevated access” button from the right click menu, to ask my Helpdesk to approve my request.
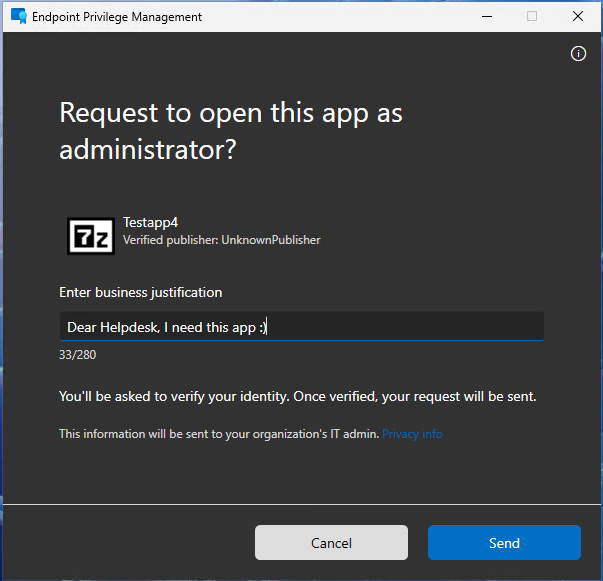
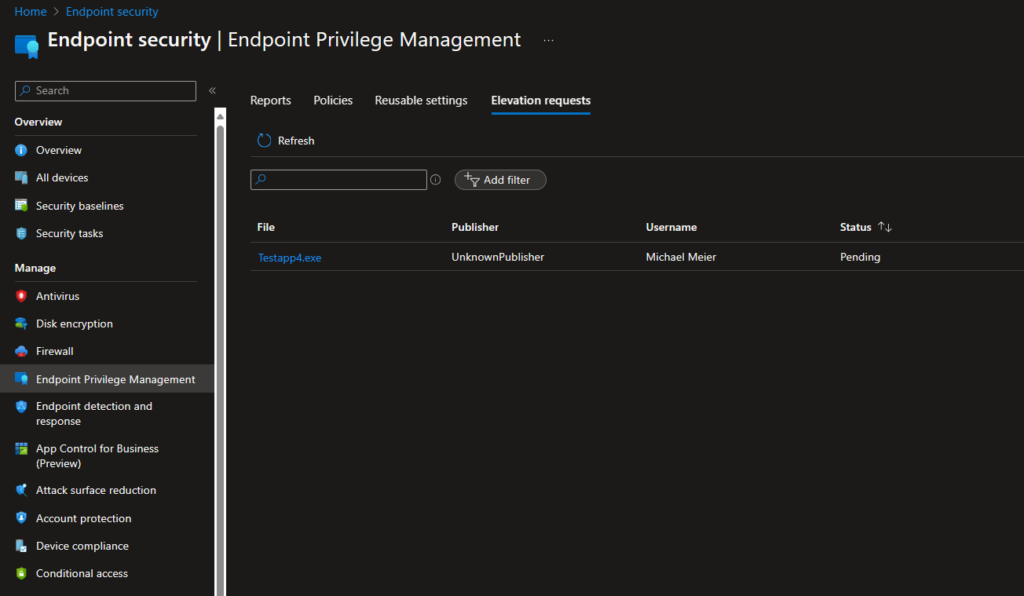
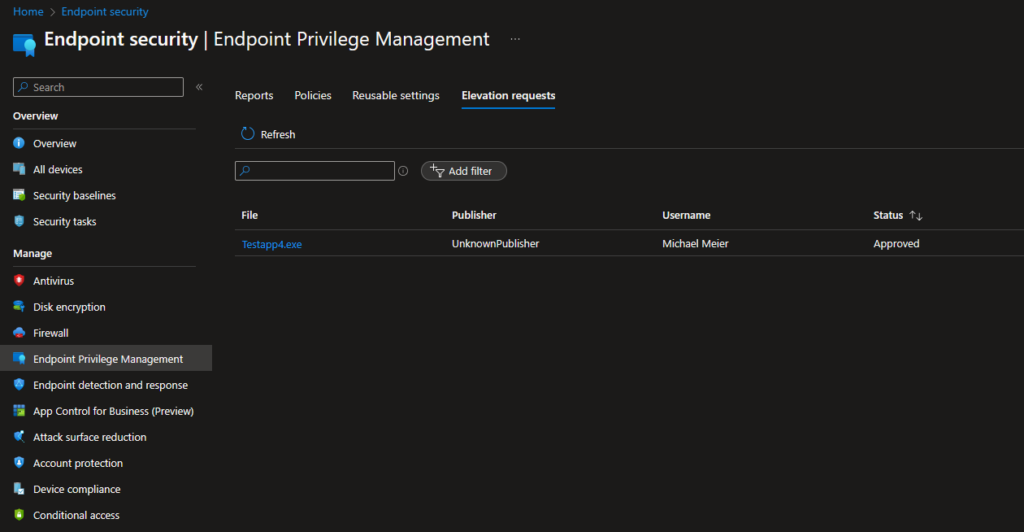
Once the user requested the elevation and called the Helpdesk, they can see the request in Intune:
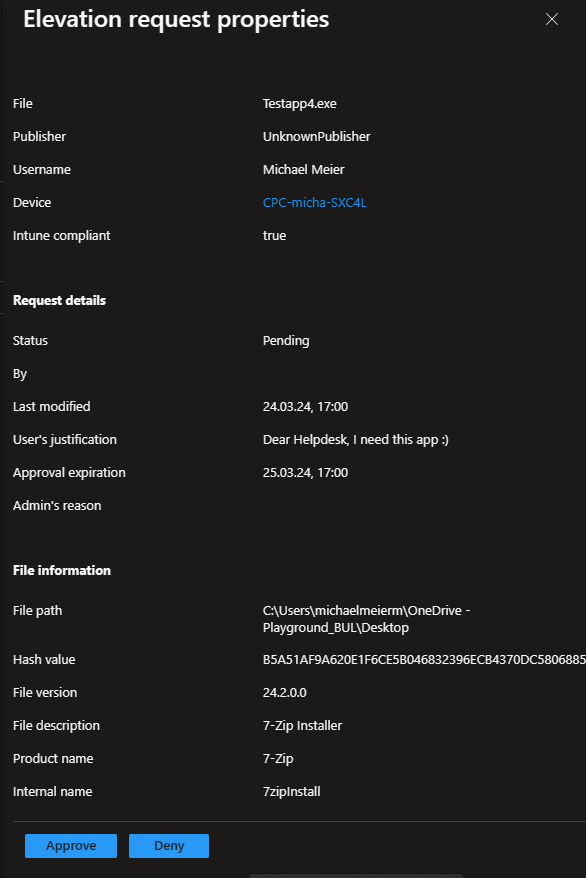
They can see all the details they need to check if the request is valid:
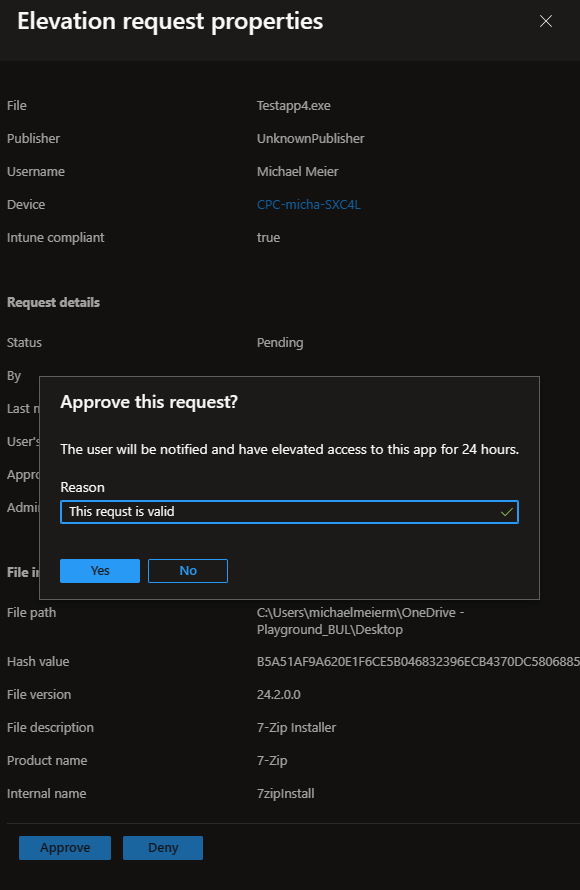
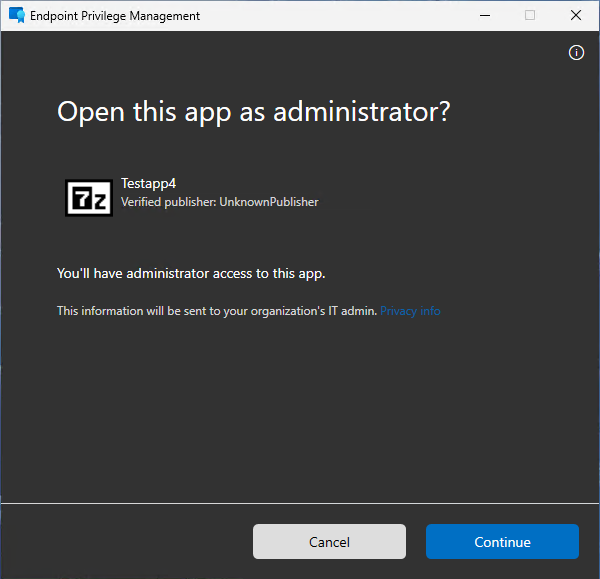
After the Helpdesk agent approved the request, the user can start the application again using the “Run with elevated access” button from the right click menu, but this time the app will be started with elevated access.

Conclusion
While the Intune EPM Solution still has some limitations compared with more mature solutions like from BeyondTrust, I think now is the right time to have a look at it and try it out. Especially with the new support approval flow, Intune EPM got a really cool feature, which makes removing permanent admin rights for all users including your admins so much easier and make your environment so more secure.
Leave a Reply