From time to time, I wanted to have a way to set Policies (GPOs) on my test clients in a non-enforced way, which allows me to locally modify the settings to troubleshoot something, while still having an easy way to re-apply the settings.
While this is definitely an edge case and does not apply to many users / devices, I still think this can be a helpful solution for testing and developing. To achieve this, we are using the LGPO Utility: LGPO.exe – Local Group Policy Object Utility which is part of the Microsoft Security Compliance Toolkit
Export GPO
Let’s start with creating the set of policies, which we want to apply using the LGPO Utility. I will create a new GPO in which we will set everything that we need:
For demonstration, I will use the “Only display the private store within the Microsoft Store” Policy, as it’s very easy to showcase what it’s doing:
Once we have all set, we can export the GPO.
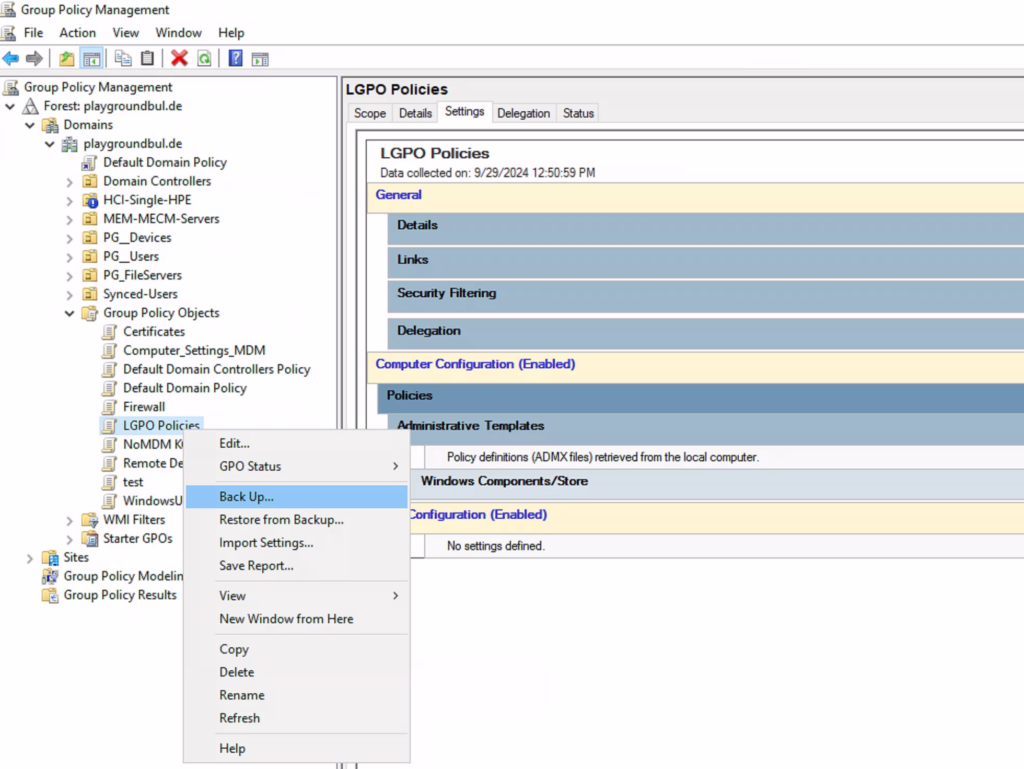
Finally, we need to copy the exported folder:
LGPO.exe
Next thing that we need, is the LGPO.exe from the Microsoft Security Compliance Toolkit: Download Microsoft Security Compliance Toolkit 1.0 from Official Microsoft Download Center
We can copy the LGPO.exe in the same directory as our GPO export.
PowerShell LGPO Tool
Last but not least, we will need the PowerShell based LGPO Tool that I wrote to make the applying of the GPOs easier. You can get the script from my GitHub here:
Scripts/LGPOTool.ps1 at main · mmeierm/Scripts (github.com)
First thing that we have to modify in the script, is the path to the GPO Export in line 1:
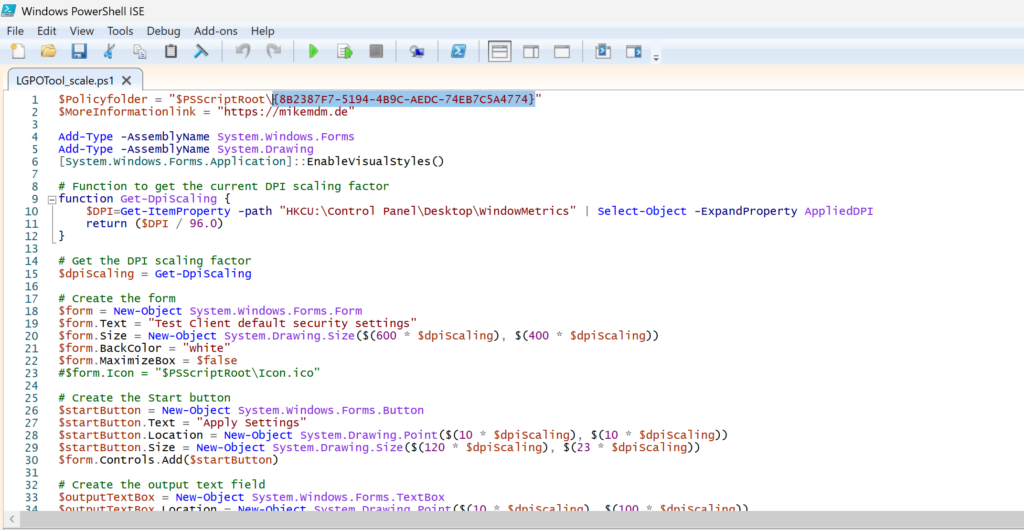
You can also modify the “More information” link, which should link to a page, explaining what the tool does. (For example, a html export of the GPO itself)
Test it out
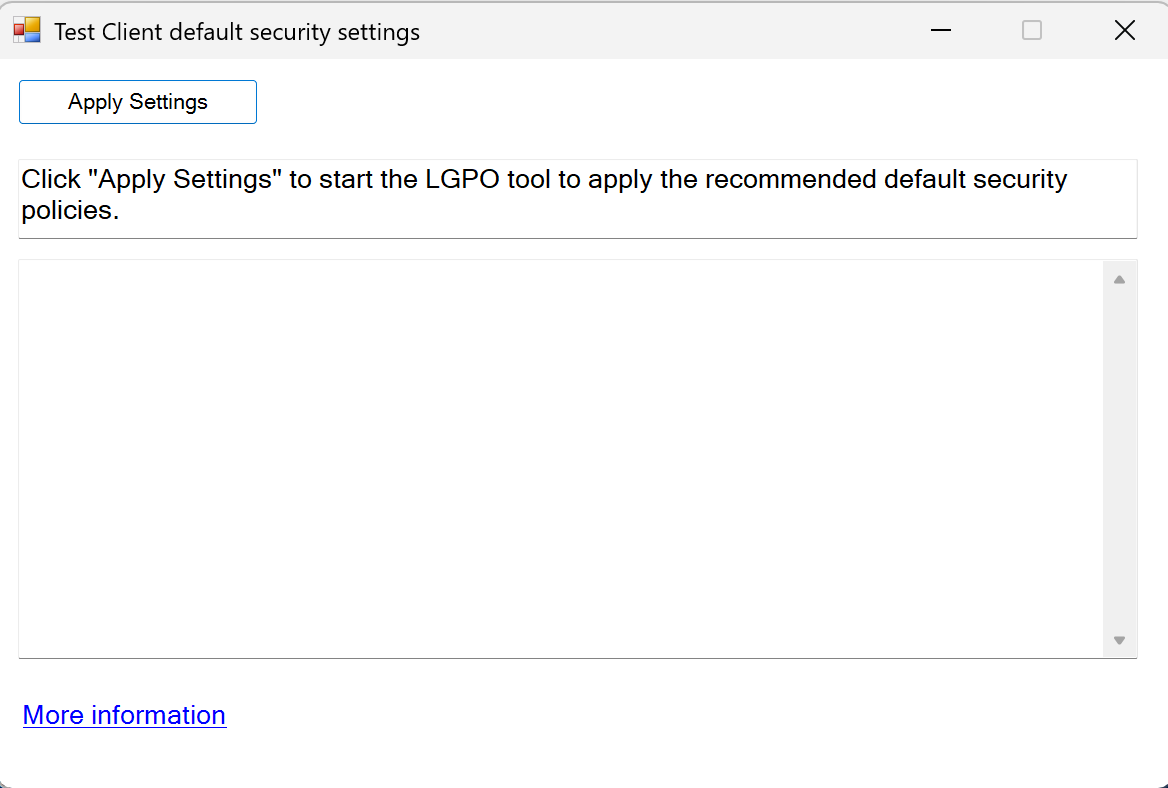
Now that we have all prerequisites ready, we can simply test it from an administrative PowerShell session:
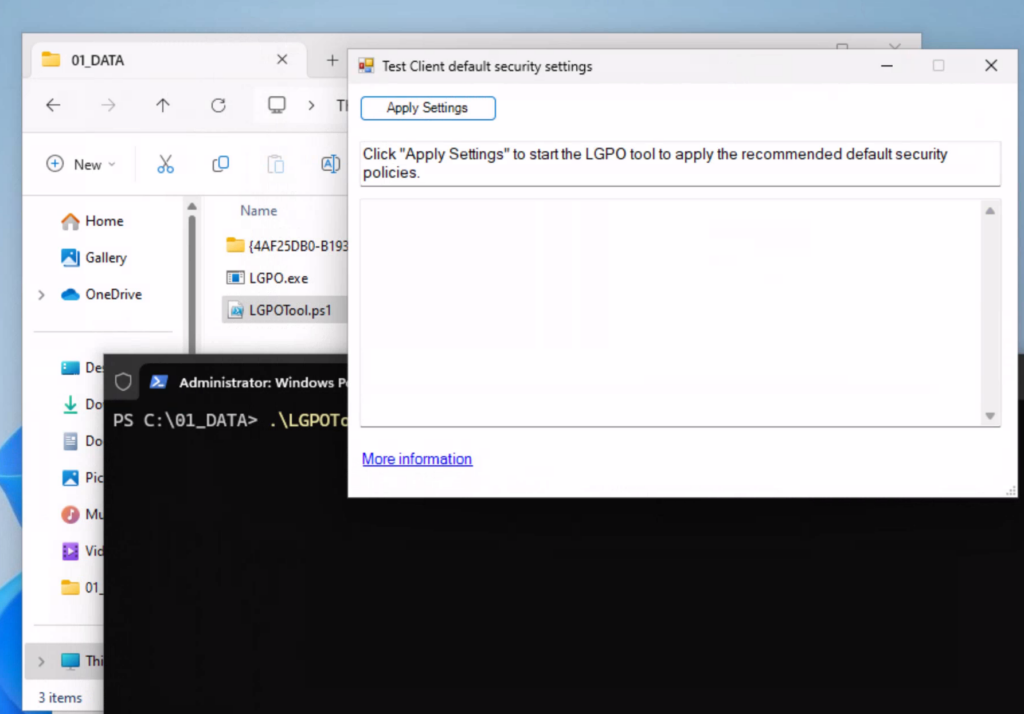
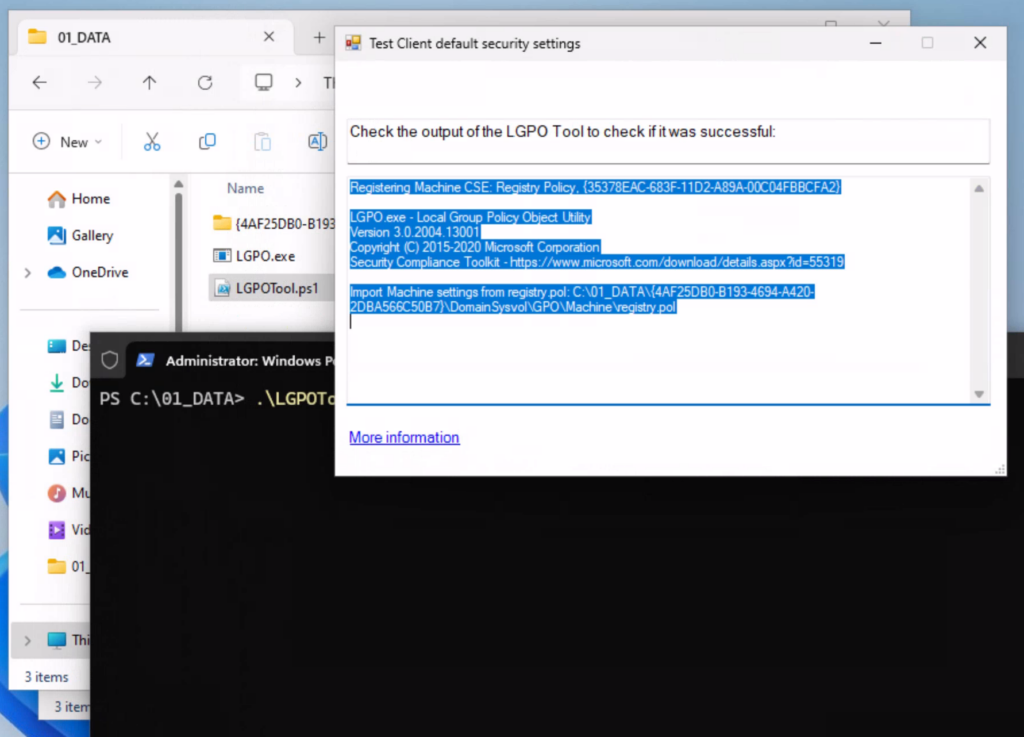
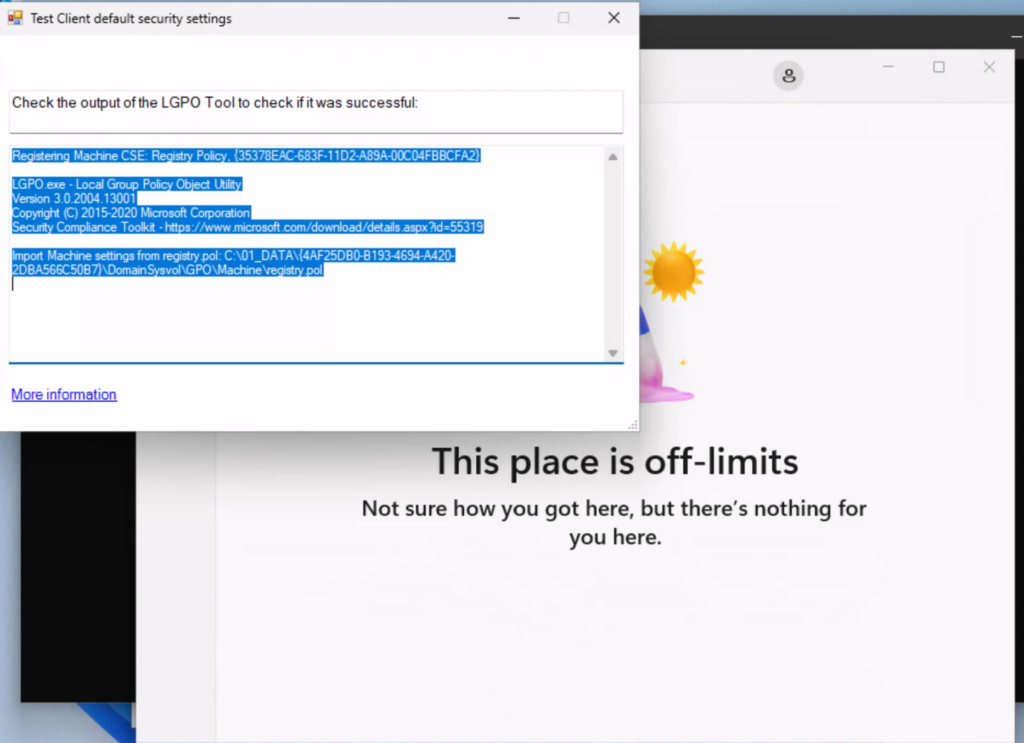
As you can see, the policy was successfully applied and the access to the store is blocked:
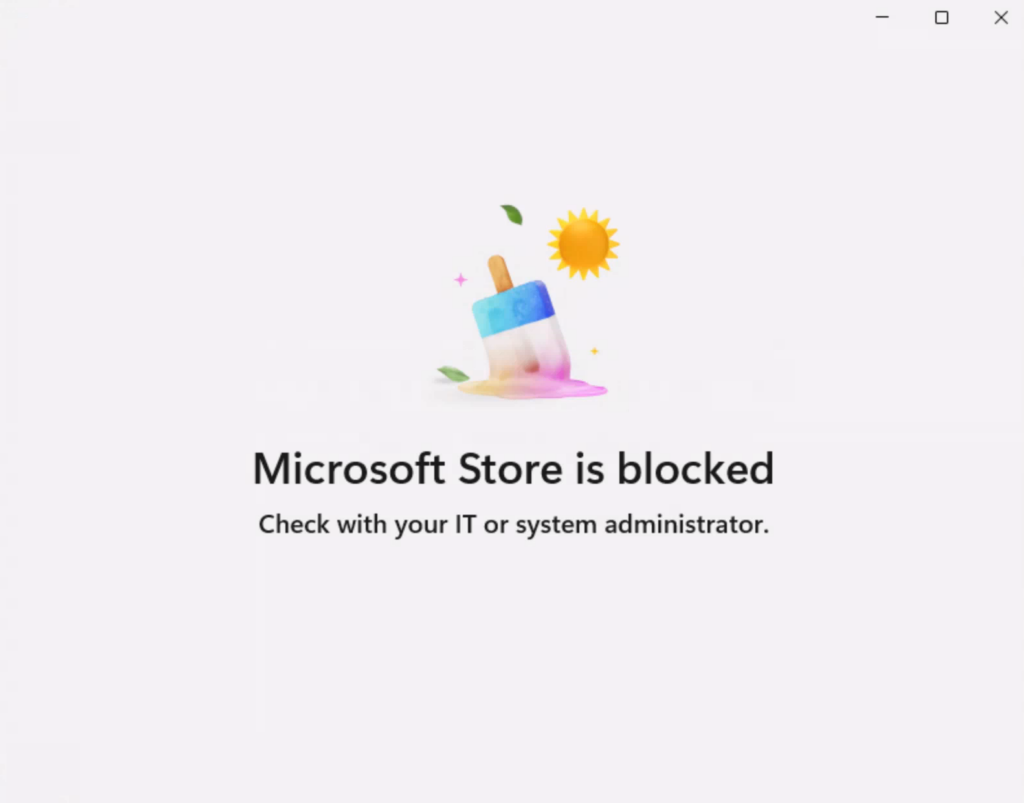
The nice thing is now, I can modify these settings in gpedit.msc, do my test / troubleshooting:
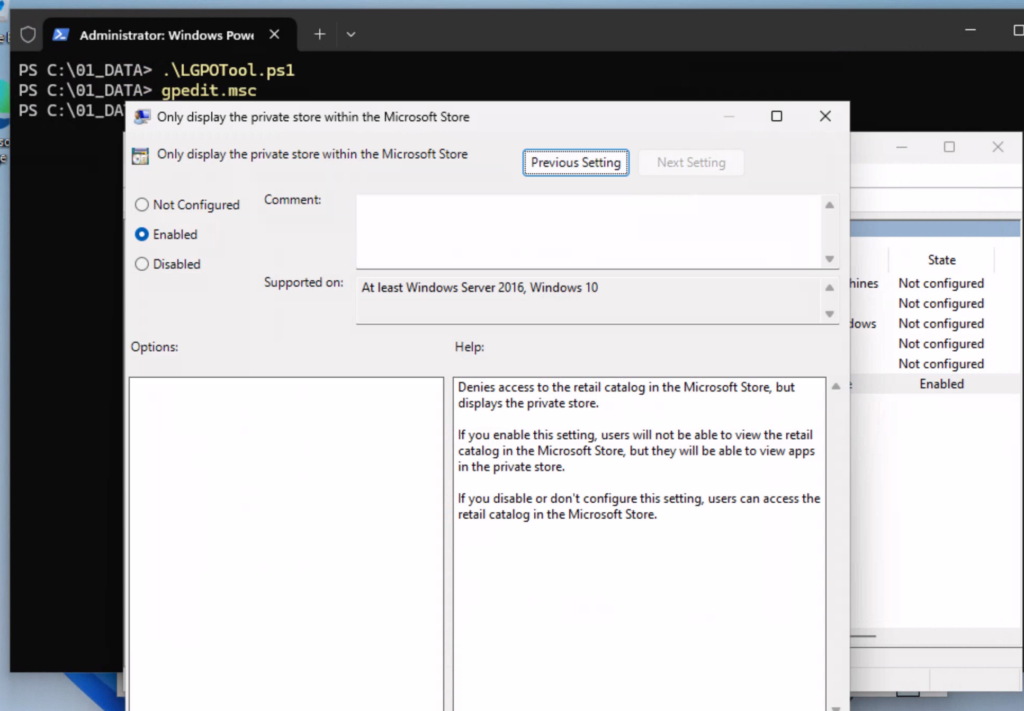
For example, allow access to the store again:
And when I want to go back to my default state, I just have to run the Tool again and apply all my default settings and see the store is blocked again:
Intune
If you want, you can deploy this tool, as an OnDemand available app in Intune using serviceui and a detection based on a regkey as described here: Install Win32 Apps visible via Intune – Mike’s MDM Blog (mikemdm.de) and here: Run Applications in Intune Company Portal on Demand – Mike’s MDM Blog (mikemdm.de)
Conclusion
While this solution is certainly not targeted to end-users and while I would always recommend applying such policies directly via Intune Policies, in my opinion there is a valid use case to have such a solution available for development / troubleshooting, where you have to change these policies frequently and can’t or don’t want to change it in Intune natively. This way you have the flexibility to change whatever you need, while still having an option to apply the defaults in an easy way.
Leave a Reply