If you ever tried to deploy a W-Fi Profile that is secured by WPA3 Enterprise to Windows Clients in Intune, you probably noticed, that this is not possible using the built-in Wi-Fi Template. Don’t worry, the solution is really simple, you can configure the Wi-Fi Profile on a Client, export it and then deploy it via Custom OMA-URI Policy.
Built-in Wi-Fi Template
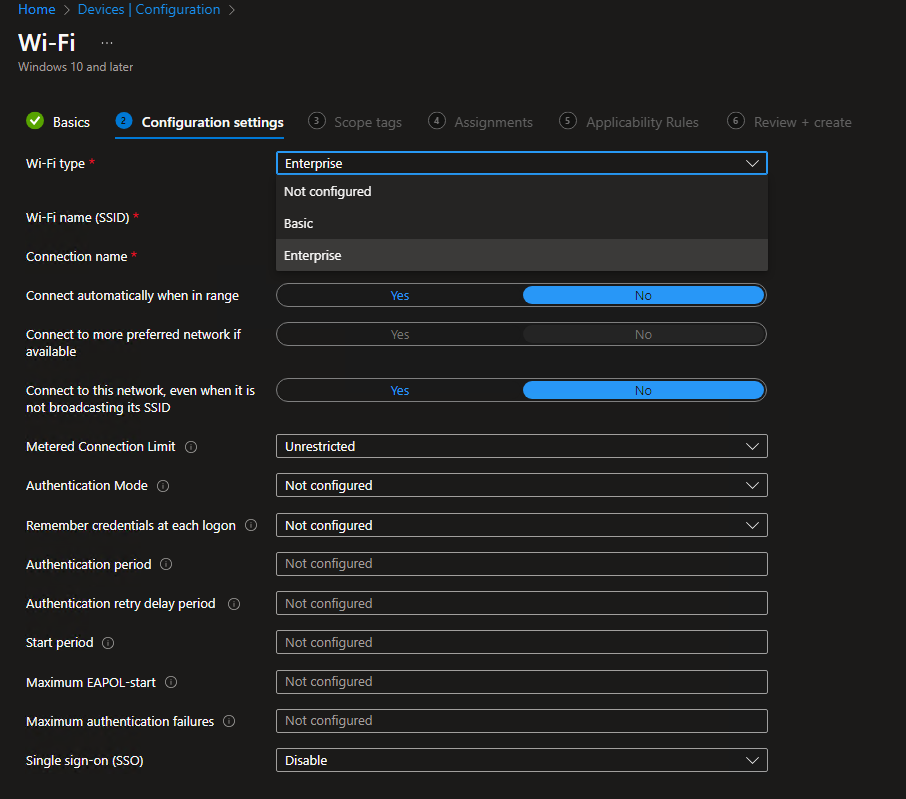
If you ever configured a Wi-Fi Profile in Intune, you most likely saw, that you can’t select WPA2 vs. WPA3. The only option is Basic vs. Enterprise:
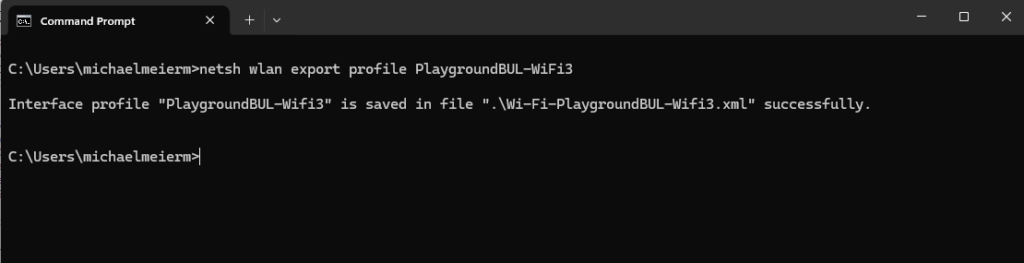
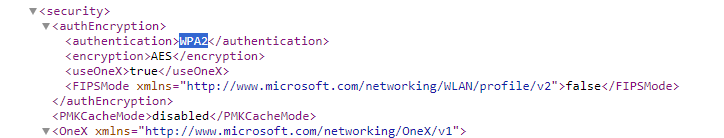
If you export the resulting profile from an endpoint, you will see it automatically creates it for WPA2:
Create a WPA3 Enterprise Profile
To create a WPA3 Enterprise Wi-Fi Profile, we can simply create it manually from within Windows:
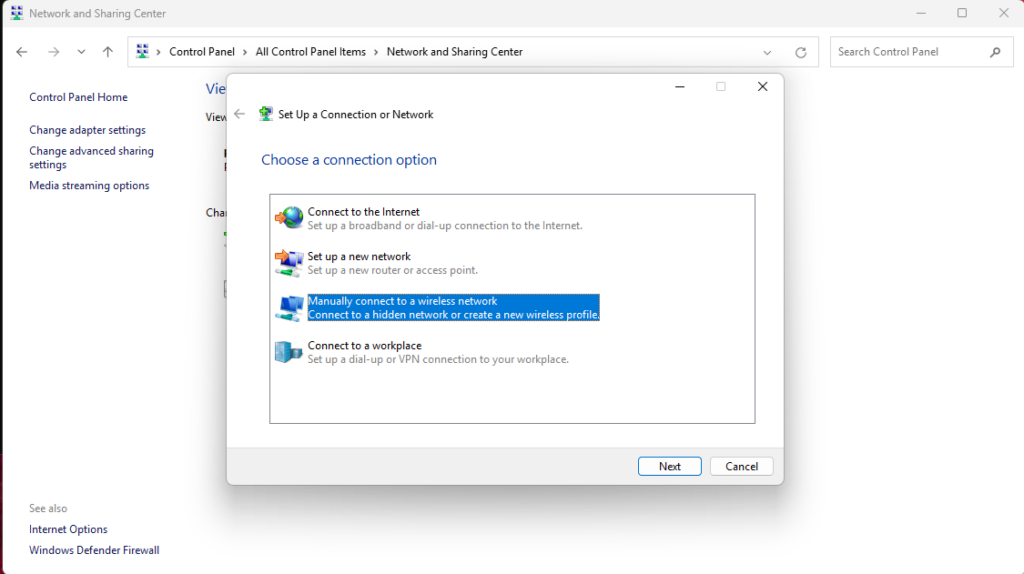
Enter the SSID and select WPA3 Enterprise:
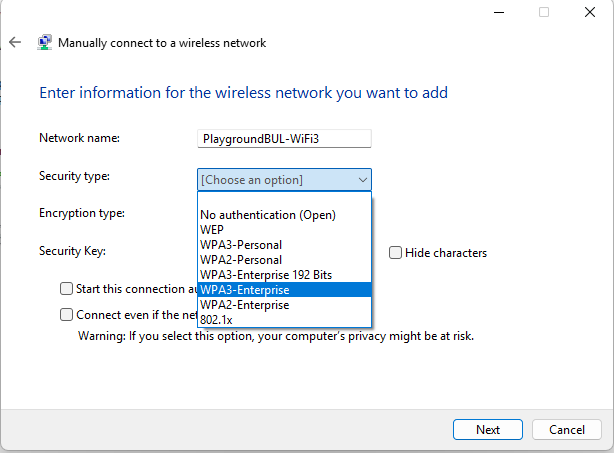
At the last screen of the wizard, you have to modify the freshly created profile to match your configuration needs, like switch to EAP-TLS and modify the certificate selection properties.
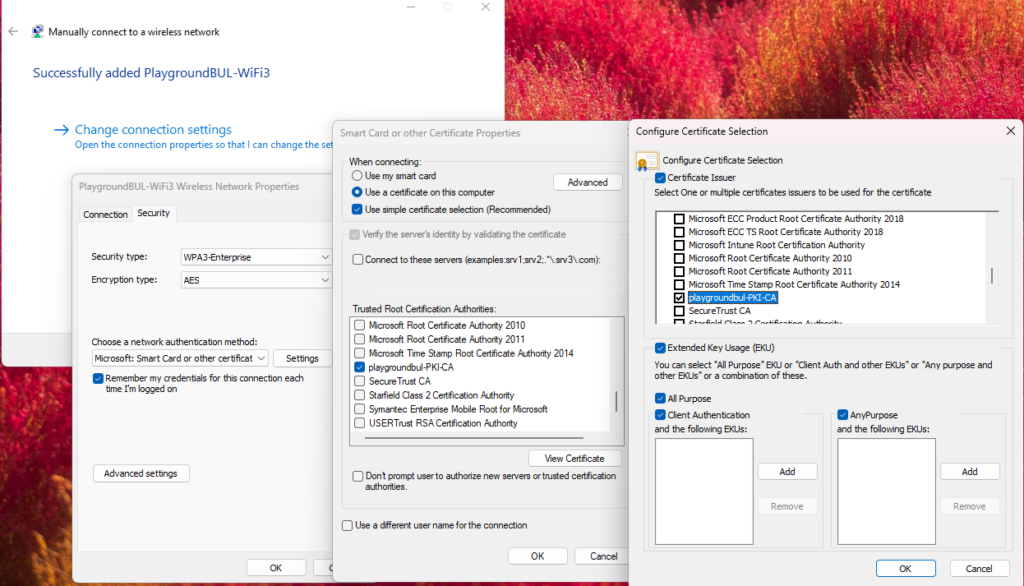
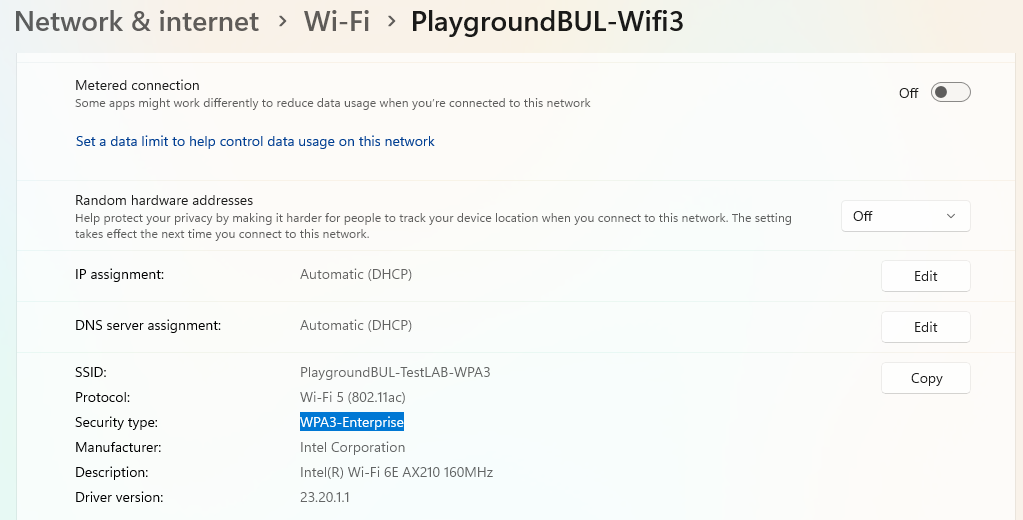
Once the Profile is created and working, we just have to export it with the following command: (Replace the Profile Name with your selected SSID)
netsh wlan export profile <ProfileName>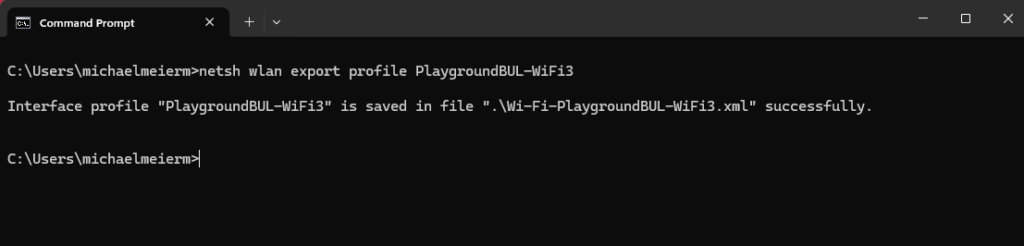
Intune Configuration Profile
Lastly, we just have to create a Custom OMA-URI Configuration Profile in Intune. Use the following OMA-URI and change <SSID> with your SSID:
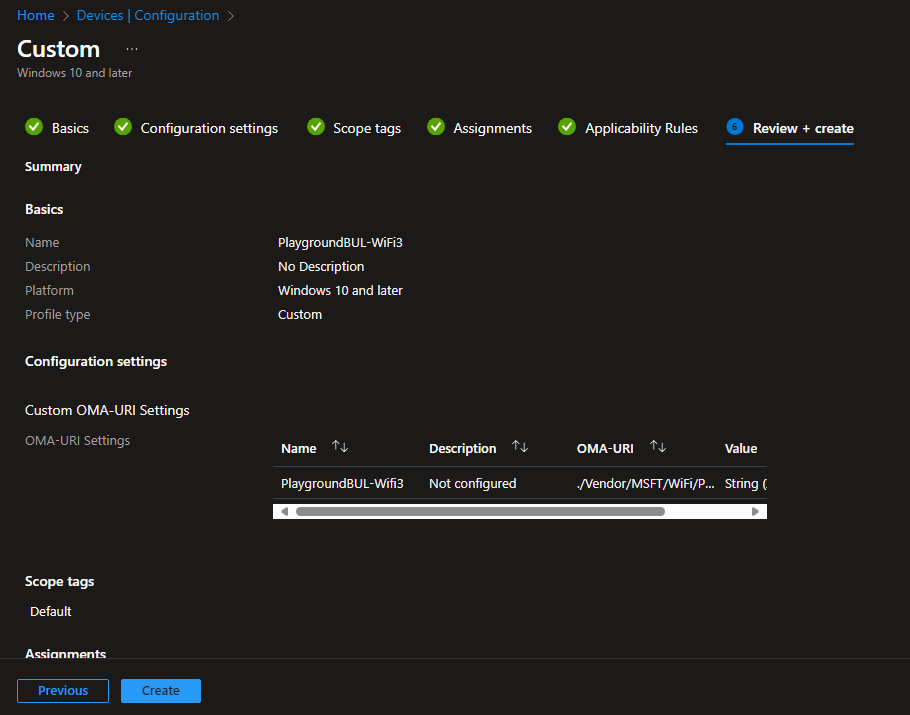
./Vendor/MSFT/WiFi/Profile/<SSID>/WlanXmlLet’s start with a new blank Custom profile:
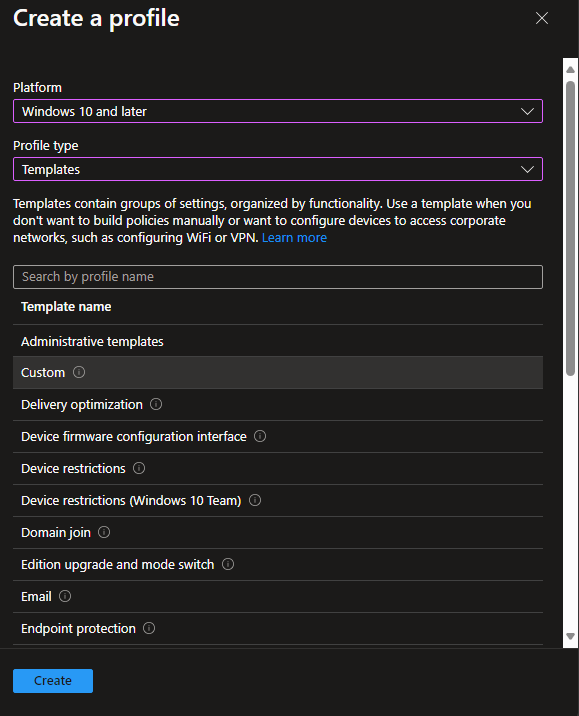
Give it a Name:
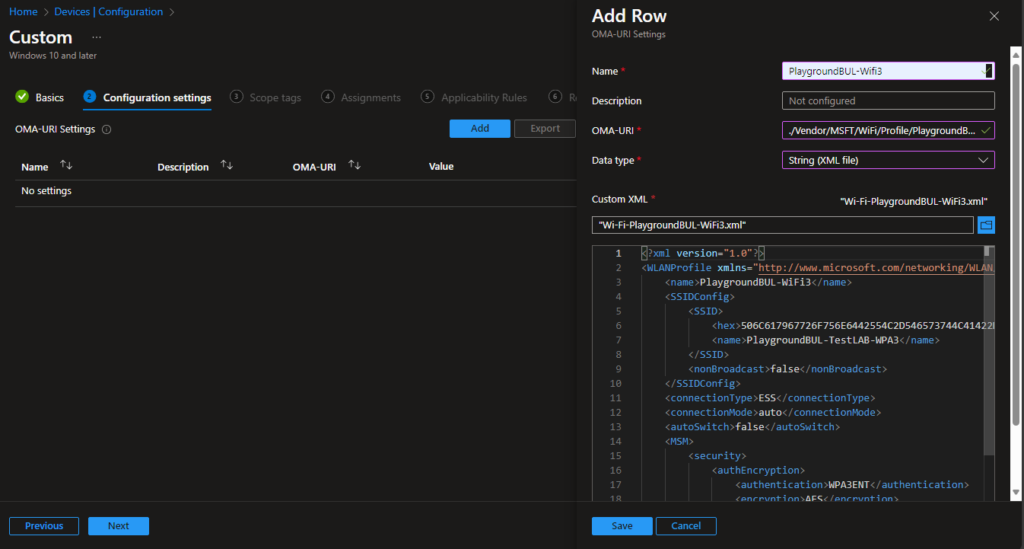
Add a new Row with the OMA-URI from above and the Data type of “String (XML file) and upload the exported profile from the client:
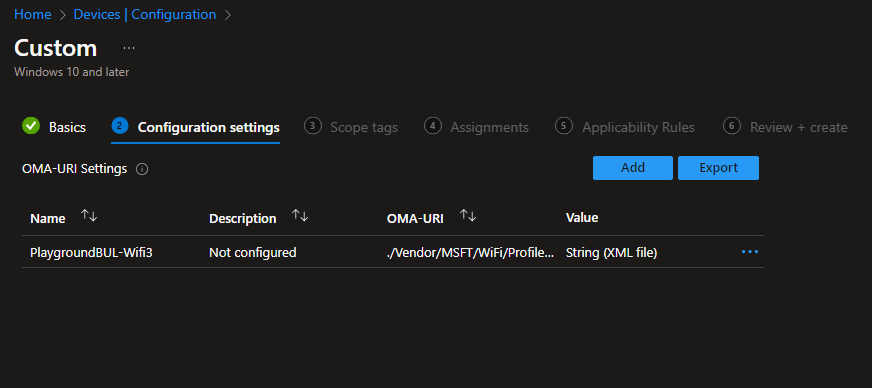
After the usual stuff, like add Scope Tags and Assignment, we can review our settings and create the Profile.
Conclusion
While it is unfortunately not yet possible to create a WPA3 Enterprise encrypted Wi-Fi Profile in Intune directly, you fortunately create and deploy it pretty easily with the Custom OMA-URI Profile type in Intune.
Leave a Reply