Today I want to show you how you can check if the BitLocker Key Backup to Entra ID (AzureAD) was successfully done. We have configured BitLocker encryption in Intune to silently encrypt the system drive and automatically upload the recovery key.


Usually these Settings should ensure, that the device is only encrypted if the Recovery key could be uploaded to Entra ID (aka. AzureAD). Unfortunately, this is only true for the automatic silent encryption or during the client-driven key rotation, but not for manual encryption using manage-bde or the PowerShell equivalent Enable-BitLocker. A quick check using Graph-API to list all uploaded recovery keys showed, that we are missing keys of 5-10% of our devices, as we have devices that were already encrypted using MBAM before we switched to Intune and also some devices were manually decrypted and encrypted during troubleshooting.
To solve this issue, we decided to create a small (proactive) Remediation script in Intune, which checks the local EventLog for the EventID 845 that represents the successful upload to Entra ID:

I uploaded the Remediation script to my GitHub for you to check out: Detection, Remediation
To create the Remediation, simply create it in the Scripts section, give it a name:

Upload the scripts from GitHub and make sure it runs as 64-bit process:
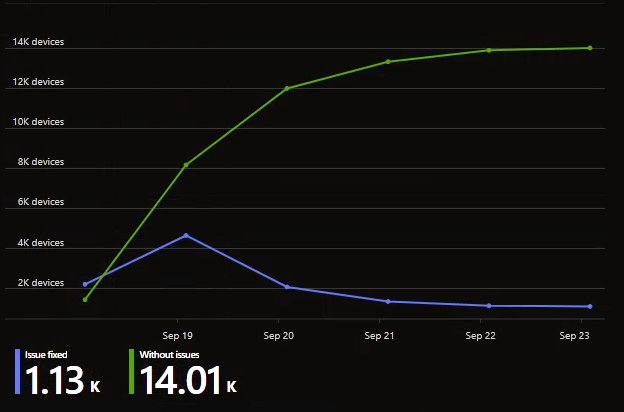
Once the remediation is deployed to a group of devices of your choice, the script will check on a regular basis if the key was uploaded successfully.

I hope this small remediation helps you, to make sure you have the recovery keys for all of your devices stored in Entra ID, so you have it handy once you need it.
Leave a Reply