Today I want to show you, how you can deploy a basic WDAC (Windows Defender Application Control) Policy that uses the Intune Management Extension (IME) as managed Installer to allow only Apps that are deployed via Intune.
WDAC Policy
At first we start creating a basic WDAC Policy, using the officia WDAC Wizard from: https://webapp-wdac-wizard.azurewebsites.net
We will start creating a Base Policy and i selected the “Allow Microsoft Mode”, since in this case I don’t intent to use the Intelligent Security Graph (ISG), as I want a “real” App Whitelisting

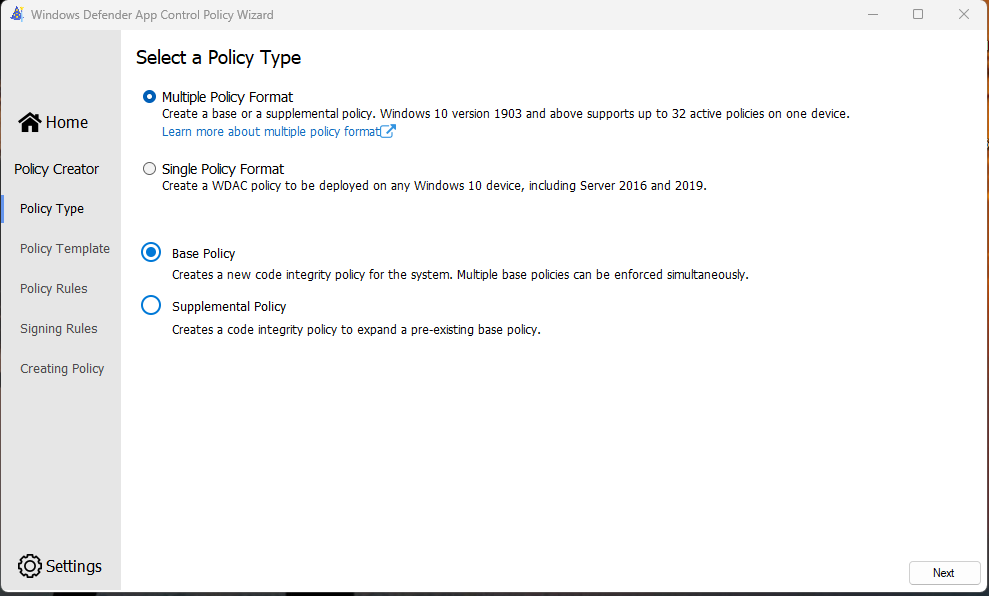

In the next section we can modify some additional Settings, like enabling the managed Installer option. For my testcase I went with these Settings:
In the next Section, you can add some additonal Rules, which I will not go into detail for this basic example. Once all modifications are done, we can create the actual policy. We will need the *.cip file in the next section to apply it via Intune

Intune Configuration Profile
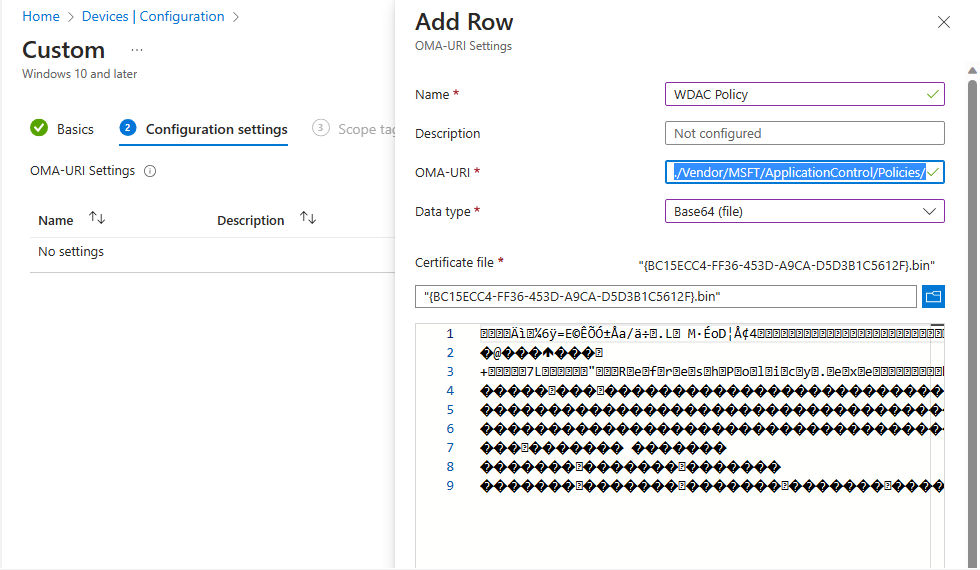
In Intune we will start with creating a Custom OMA-URI Configuration Porfile to deploy the actual WDAC Policy

In order to create the Policy, we have to change the file extension of our policy from .cip to .bin in order to upload it to Intune. We will give the policy a name, add the OMA-URI: ./Vendor/MSFT/ApplicationControl/Policies/_Policy GUID_/Policy
where we will need to replace “_Policy GUID_” with our GUID. We will select “Base64 (File)” as our Data Type and upload our Policy.
More Information on how to upload the Policy can be found in the MS learn article: https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/deployment/deploy-windows-defender-application-control-policies-using-intune#deploy-custom-wdac-policies-on-windows-10-1903
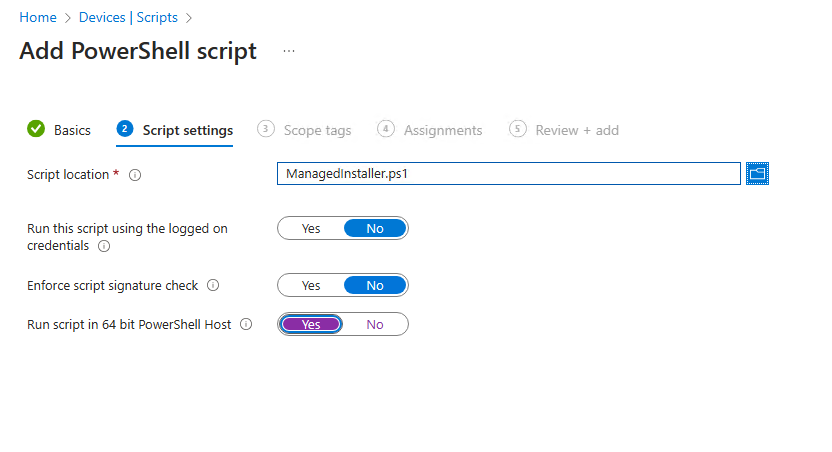
Intune Script
In order to get the managed installer part of the Policy to work, we have to deploy a AppLocker Policy for the same clients. Unfortunately as far as I know, it is currently not possible to do this via Configuration Policys as the CSP seems not to support the managed installer part of AppLocker. To mitigate this, I created a small PowerShell Script that will apply the needed Applocker Policy to set the IME as managed Installer. We can deploy it with the Scripts functionality in Intune

I uploaded a small PowerShell Script to GitHub, that will create the Applocker Policy XML and apply it to the client https://github.com/mmeierm/Scripts/blob/main/WDAC/ManagedInstaller.ps1
The script was created based on the Infos from: https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/configure-authorized-apps-deployed-with-a-managed-installer#create-and-deploy-an-applocker-policy-that-defines-your-managed-installer-rules-and-enables-services-enforcement-for-executables-and-dlls
WDAC working
Once we have assigned both, the Configuration Profile and the Script to our test machine, we can see the managed installer working, with the setup of 7-zip as an example. If we try to launch the setup via the MSI from for example your Downloads Folder, we will get the expected “not allowed” messsage:
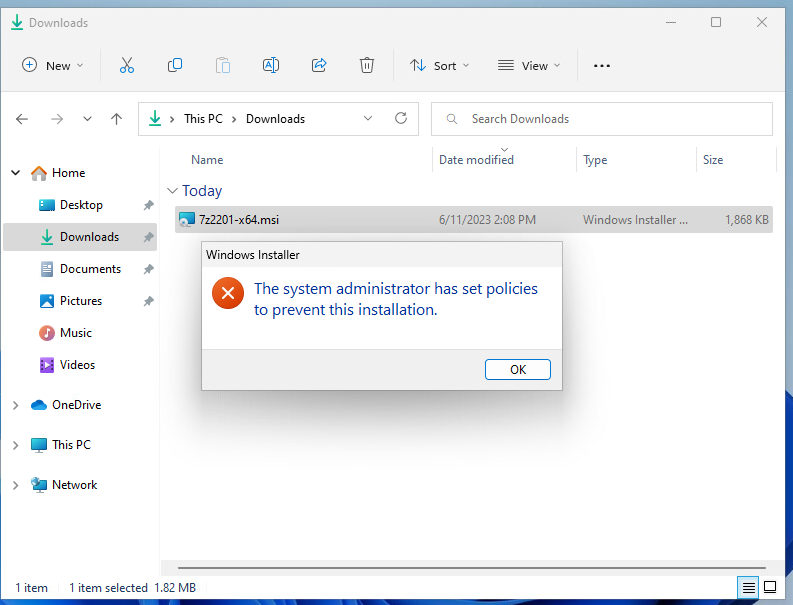
But if we start basically the same setup, that was uploaded to a Win32 Application in Intune, we will see that the setup works just fine and we have a working 7-zip installation:



Leave a Reply