Today I will show you, how you can create or set Registry Keys using Intune (Proactive) Remediations. For (Hybrid) Domain joined Clients we used Group Policy Preferences to set these RegKeys, but as there is no such thing for Azure AD joined Clients, we will use a small remediation script for this.
As an example, today we will use the Folder Option “Hide extensions for known file types”, which could be set directly via Group Policy Preferences or via RegKey.
I uploaded the example script to GitHub: https://github.com/mmeierm/Scripts/tree/main/Remediations
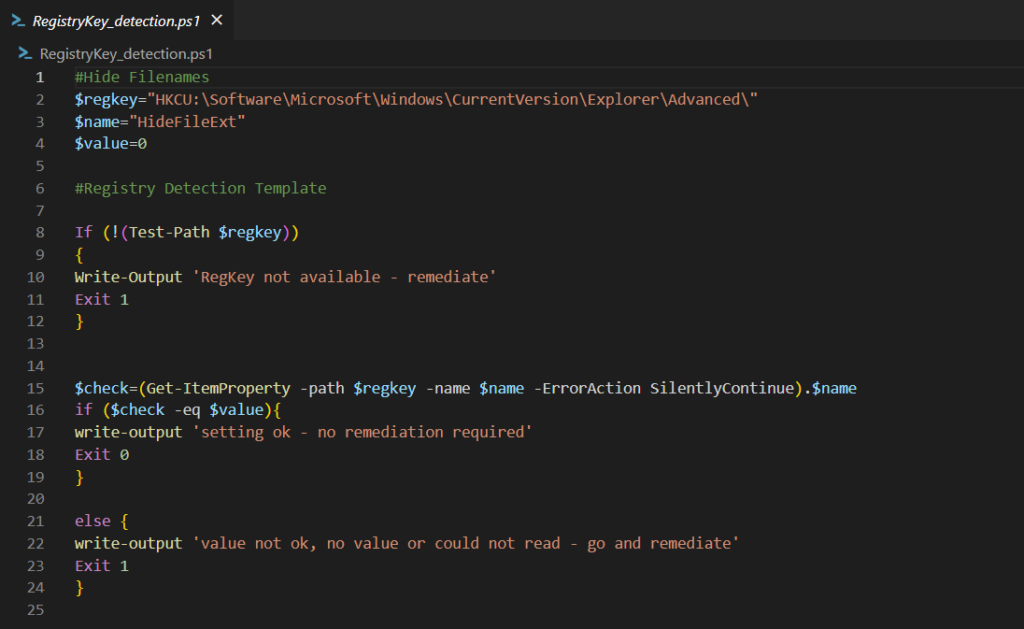
Detection
In the detection script we will have to modify line 2-4 to match our needs for the Path, the KeyName and the value.
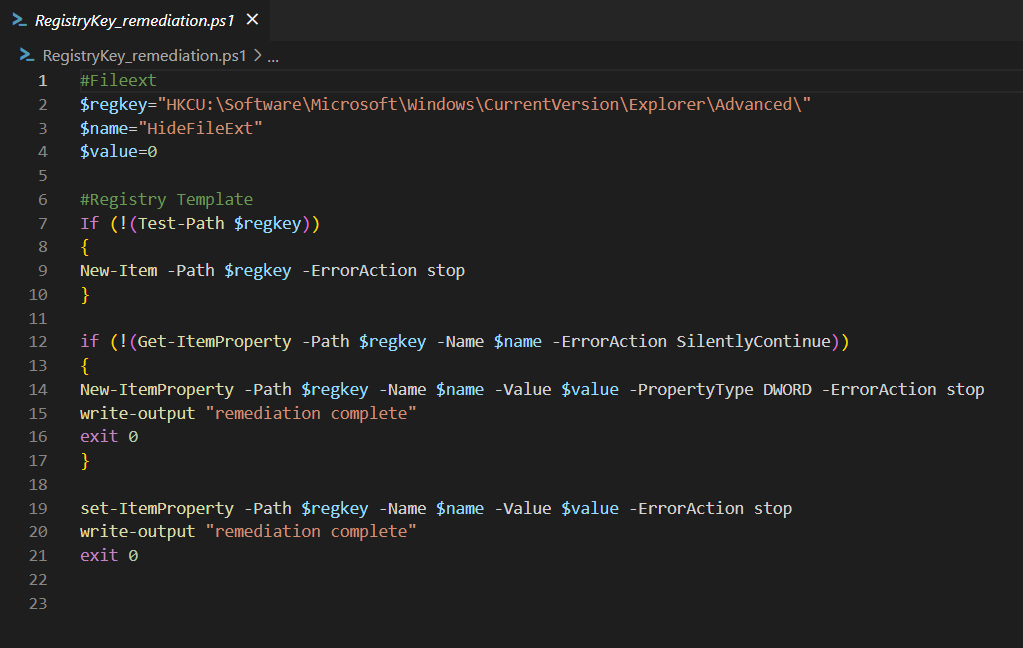
Remediation
In the remediation script, you again will need to modify line 2-4. If you are not using a “DWORD” Key you additionally need to modify the PropertyTye in line 14
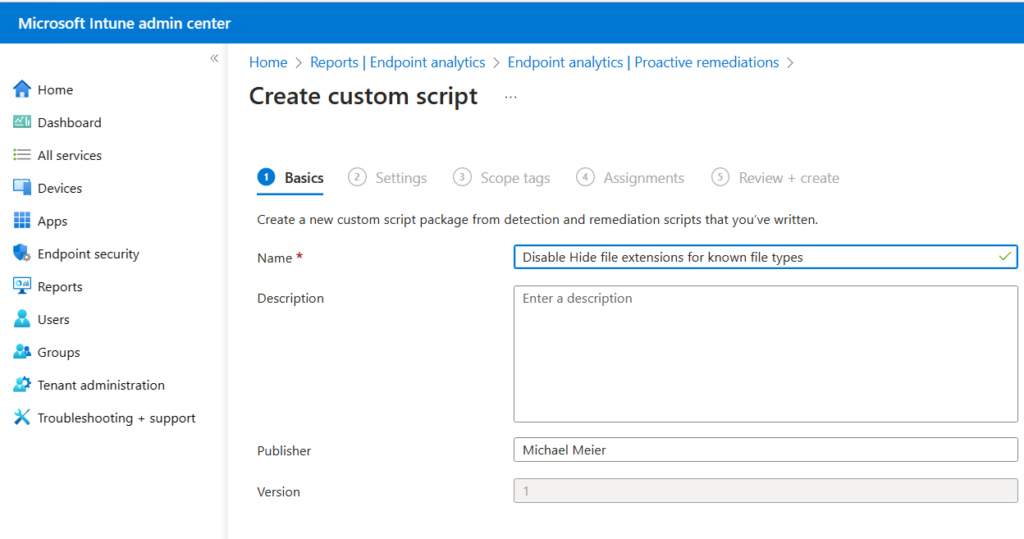
Intune
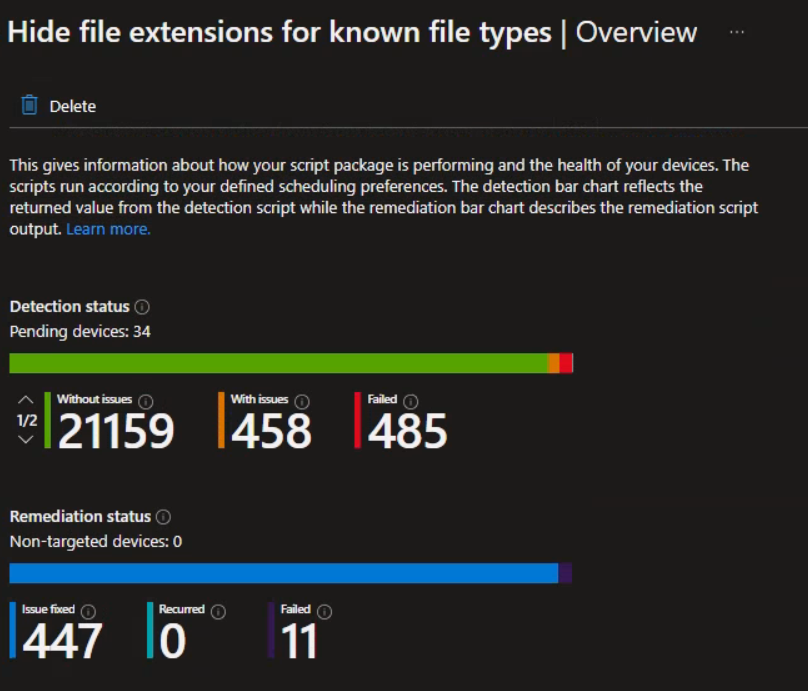
As soon as we have our scripts ready, we can create the (Proactive) Remediation in Intune.
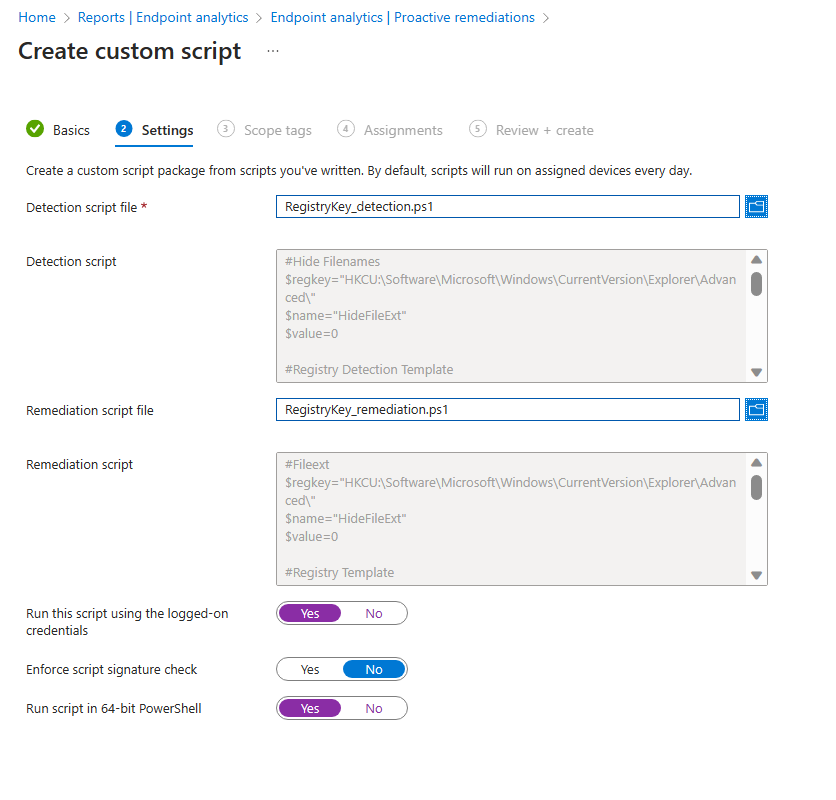
Since we want to modify a RegKey in the HKEY_Current_User section that is accessable by a “normal” non-admin account, we want to run the script in the current user context, if we want to modify a key in HKEY_Local_Machine we want to run it in system context.
In a future Blog, I will show you how you can modify a key in HKEY_Current_User section that i not accessable by a non-admin account like in the policys hive.
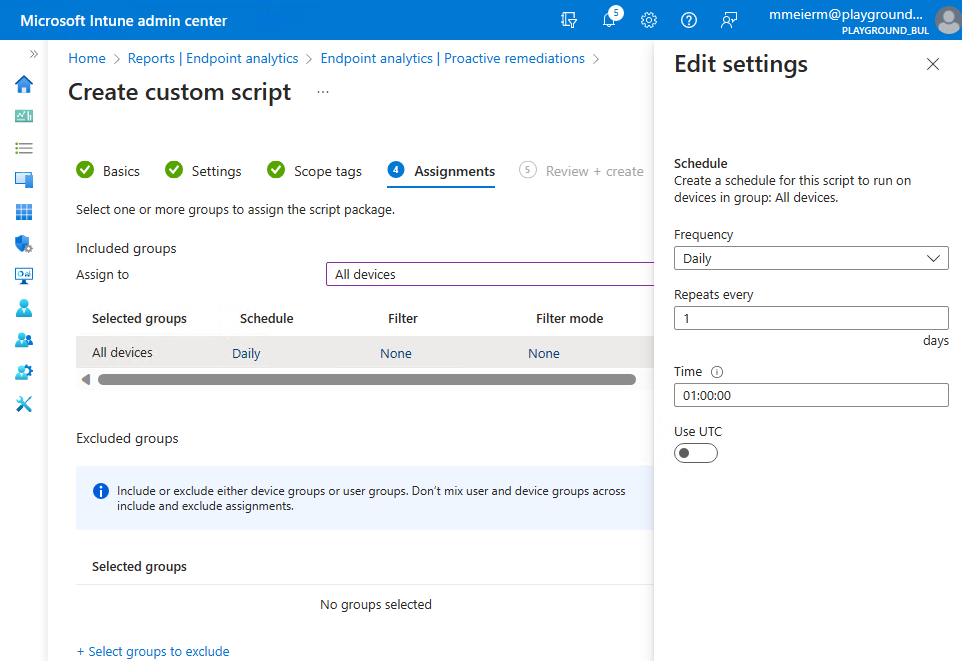
Once we have uploaded the script(s) we can assign it and set the schedule:
Leave a Reply