If you enabled Entra SSO on your AVD or Windows 365 Machines, you are probably familiar with the sign in consent prompt that asks you to allow the RDP connection to your Cloud PC / AVD Host. Your response is saved for up to 15 devices and for 30 days until you have to accept it again.
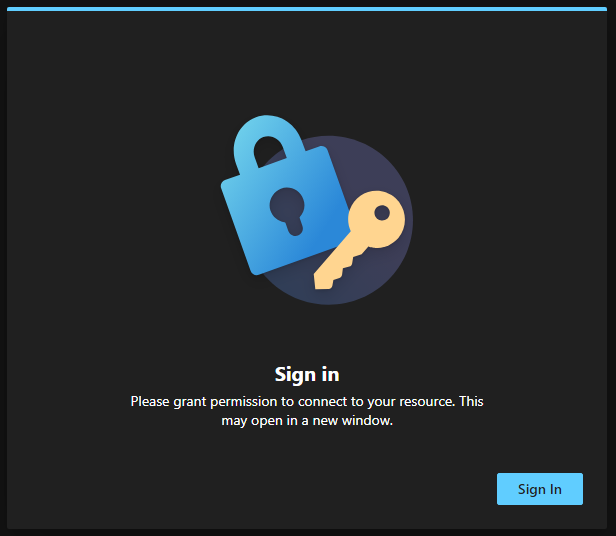
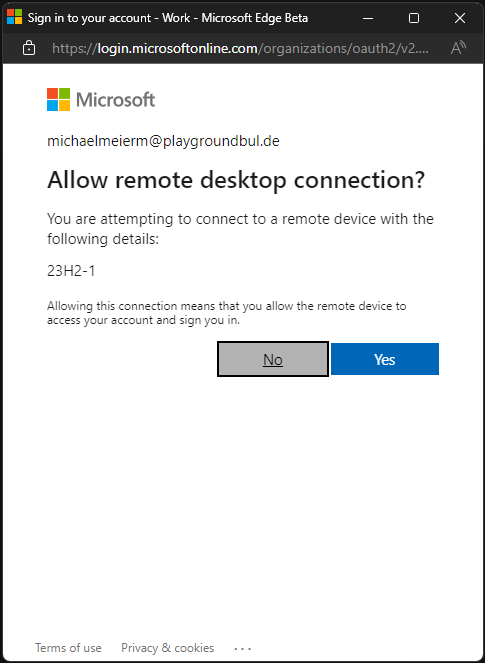
This prompts can be really annoying if you are for example working with pooled AVD Machines, or you are using Windows 365 Boot, as it interrupts the smooth sign-in flow. Fortunately, there is an easy solution (hidden) in the AVD docs that explains how you can add an Entra ID Device Group for which devices that prompt will be pre-consented automatically. All we have to do, is enable Microsoft Entra authentication for RDP and configure the target entra device group.
Entra ID Device Group
Let’s start with the Entra ID device group, that we will use to define all our Cloud PCs and AVD Host Pools that should allow SSO without the consent prompt. I would recommend a dynamic device group, to automatically add all our needed machines. Depending on your environment, you can use for example the device or enrollment profile names to add specific devices, you can also consider to use the systemLabel “CloudPC” to identify Windows 365 Machines.
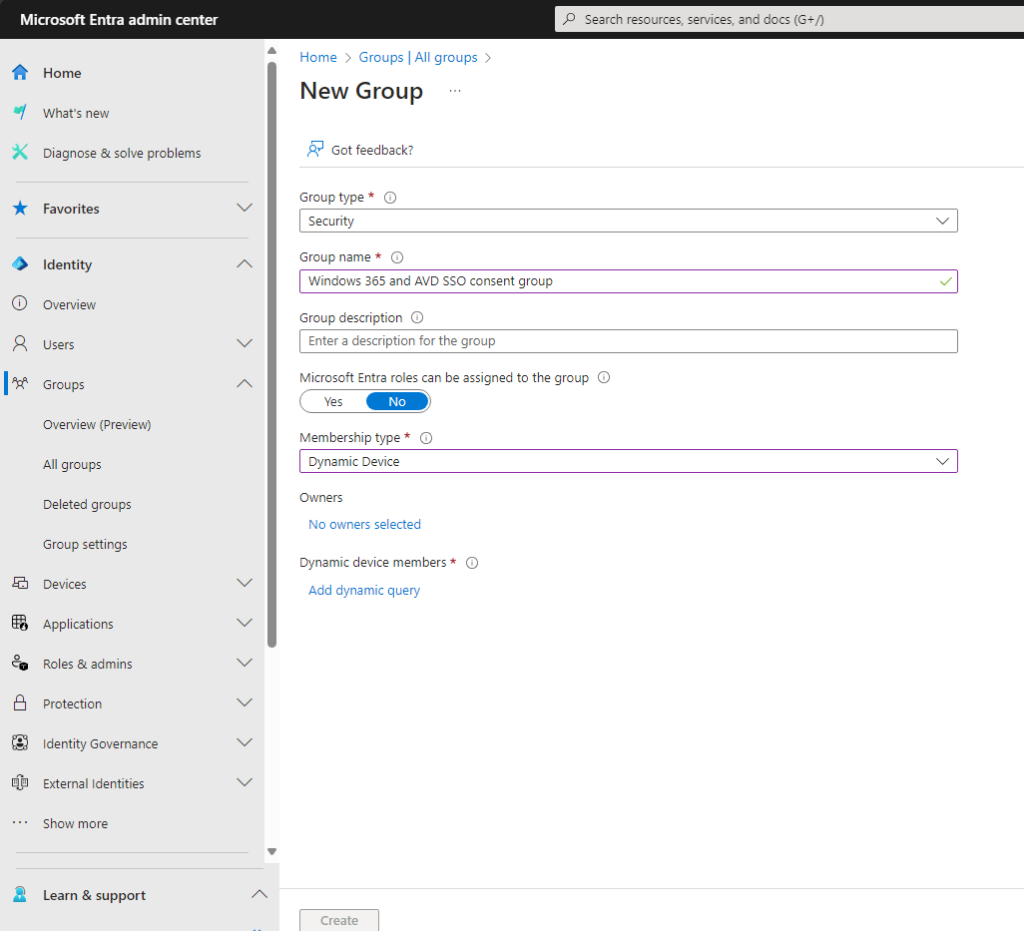
In my Lab environment this would look something like this, containing, my Windows 365 Machines, my AVD Host pool on Azure and my Azure Stack HCI AVD Pool, while my physical Autopilot devices are not part of it:
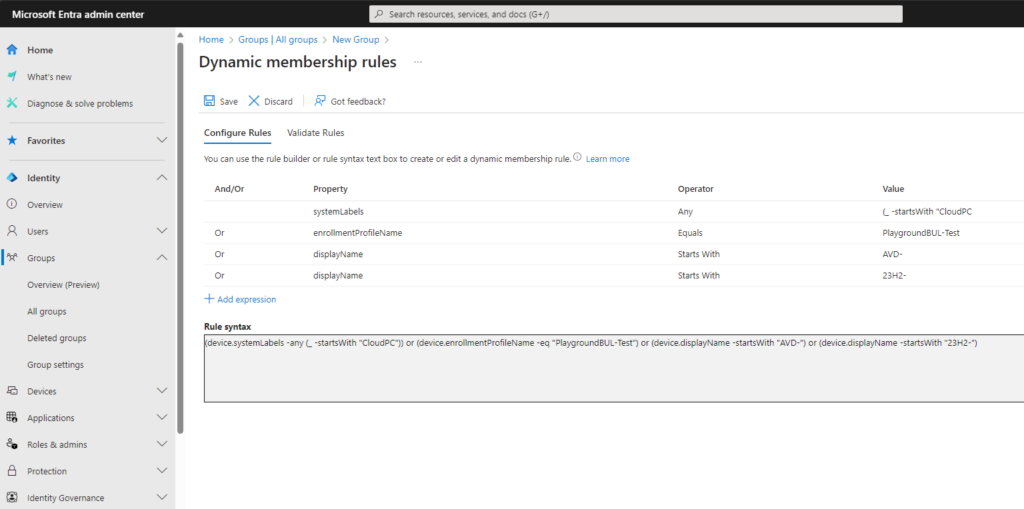
You can always check your rule to see if it matches your expectations:
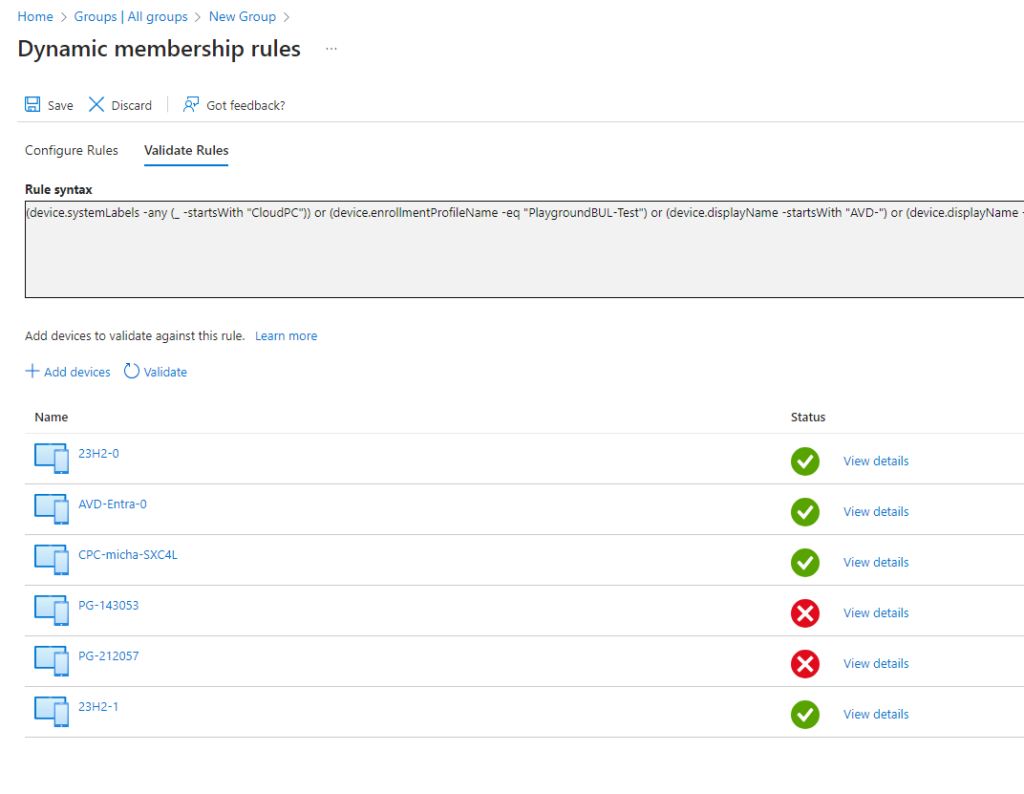
Enable Microsoft Entra authentication for RDP
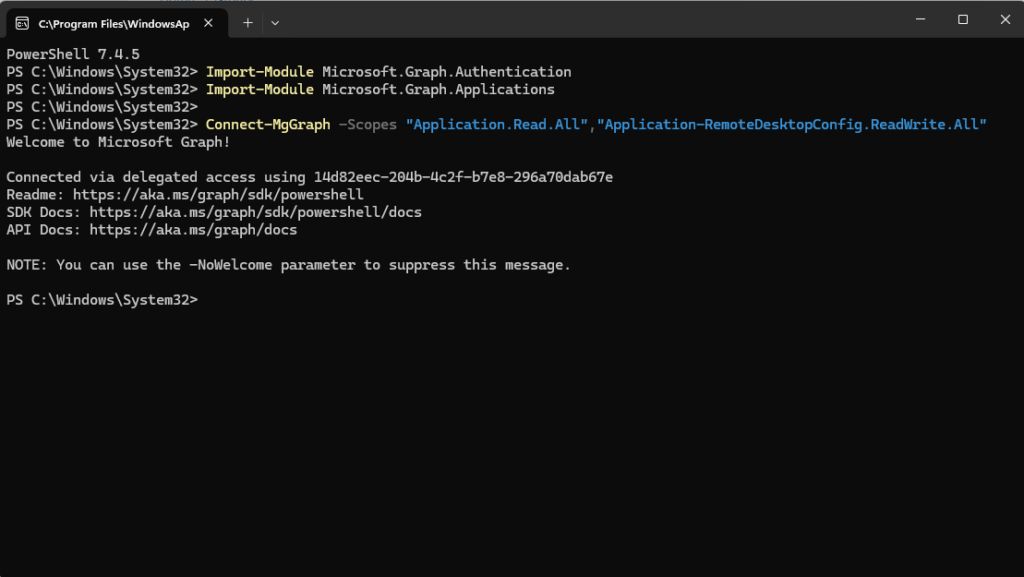
Next step that we have to do, is to enable Microsoft Entra authentication for RDP as described in the official docs: enable-microsoft-entra-authentication-for-rdp
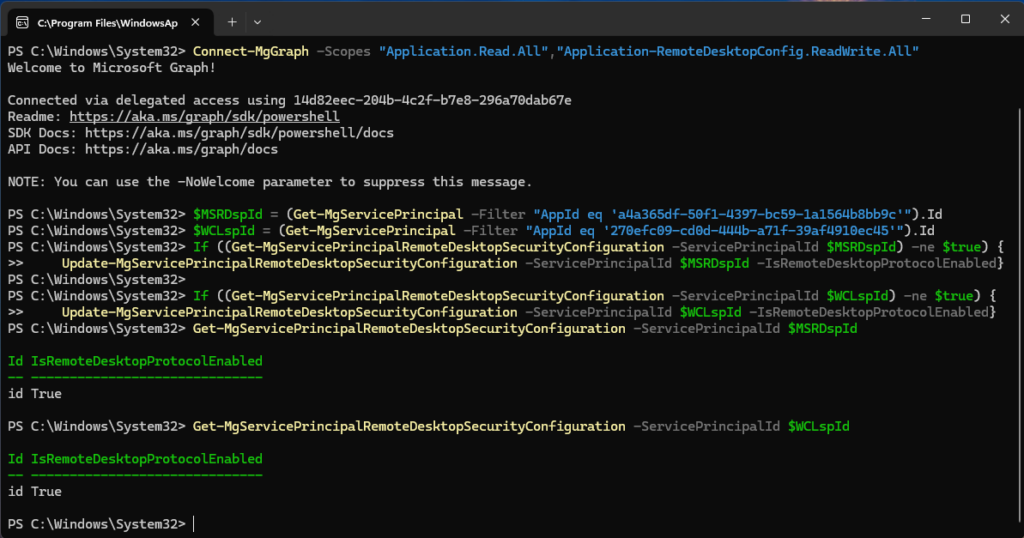
We will start with the authentication against Microsoft Graph:
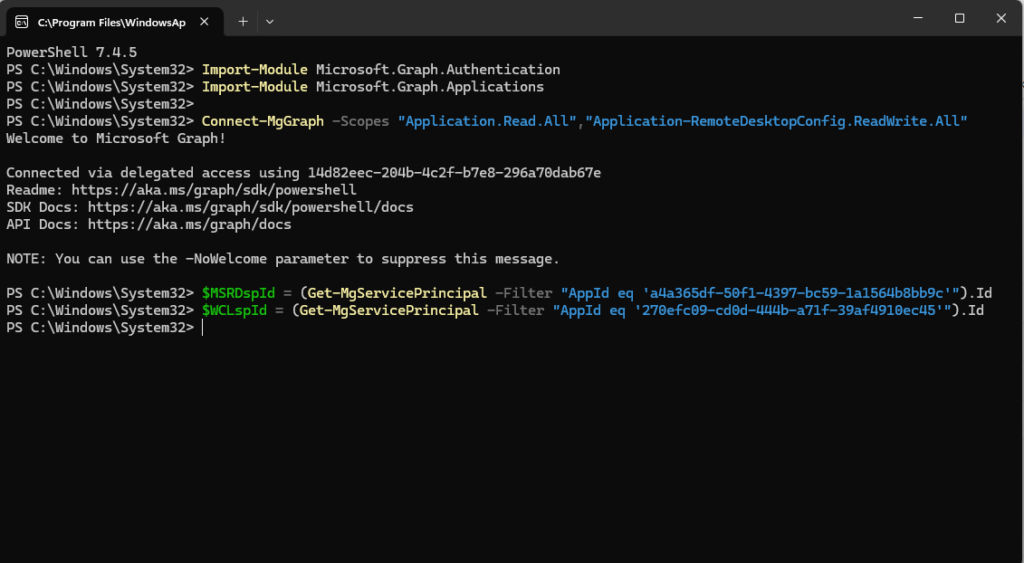
Next, we will fill our variables with the Object ids of our two affected service principals:
Update the configuration to enable RDP if not already enabled:
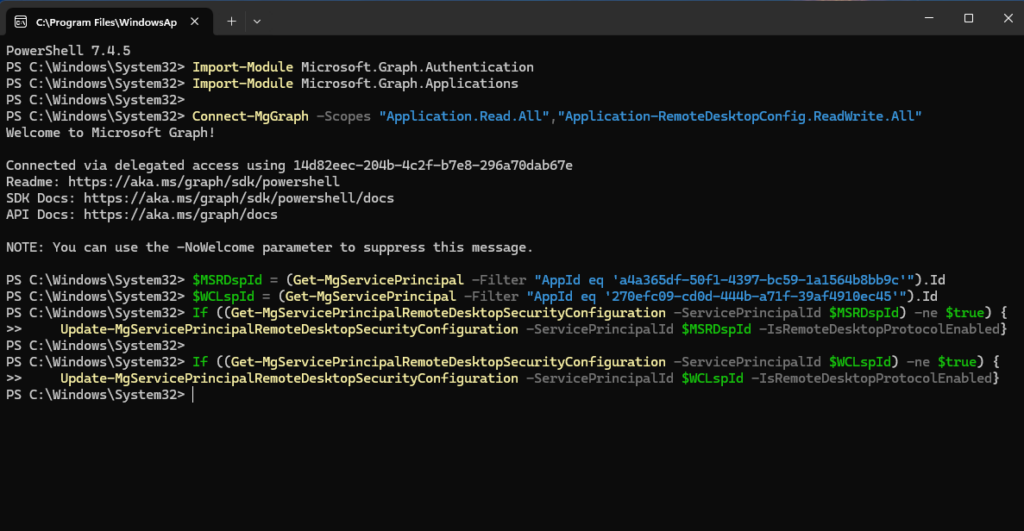
And finally check if it worked and RDP is now enabled on both service principals:
Configure the target device groups
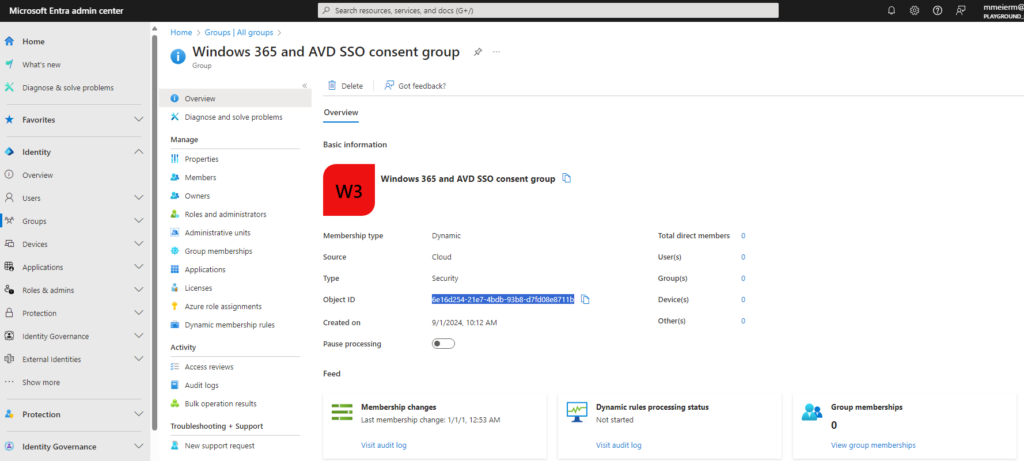
Now we can finally link our previously created Entra ID group to these service principals. We will use the same PowerShell instance, so we don’t have to prepare the session again. We will firstly need to create a new object, containing our group name and id. We will get both on the overview page of our group:
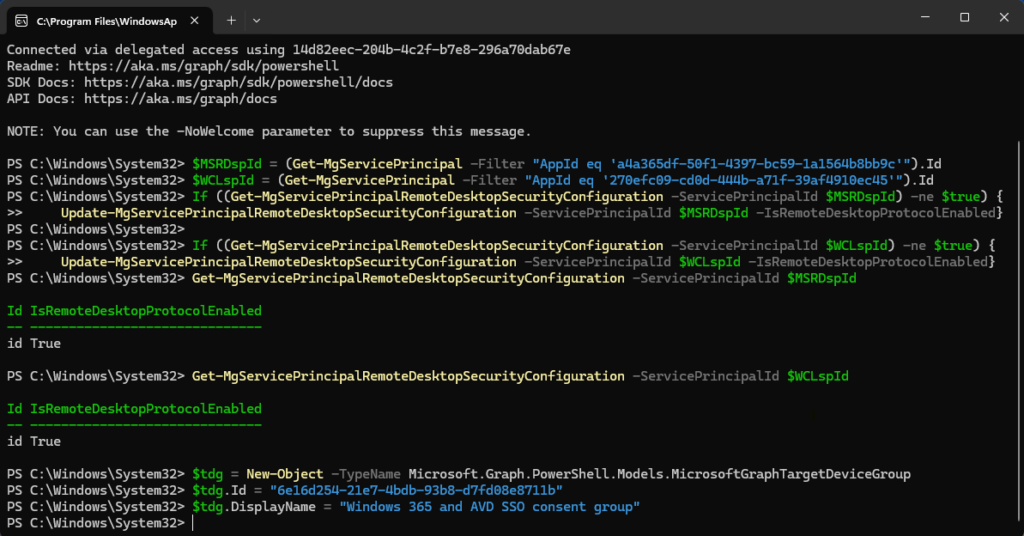
Then again as stated in the docs, create the object in our PowerShell instance:
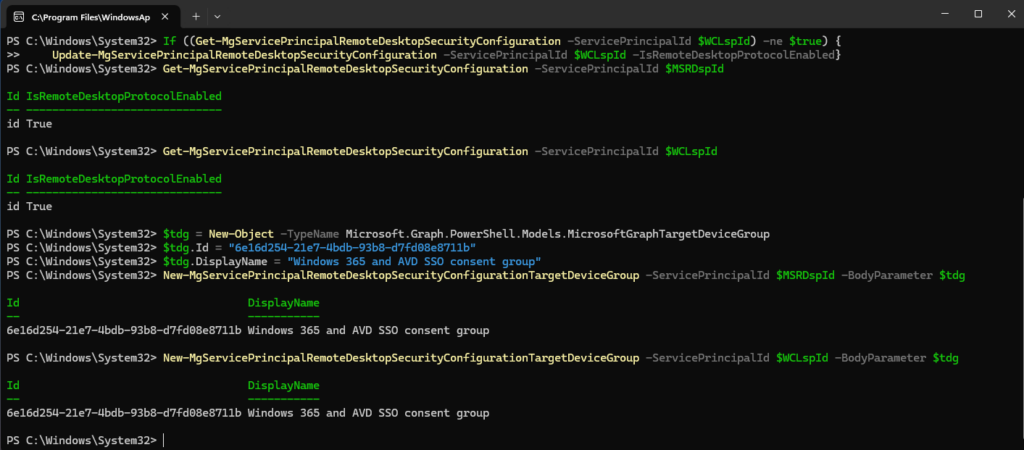
And update our service principals with this object:
Try it
Now that we finished all our configuration, let’s try it on a fresh AVD Machine:
And we are automatically signed in without the consent message:
Conclusion
I personally wish I would have known this feature way earlier, since this improves the user experience of Entra SSO in AVD and Windows 365 so much, especially when working with pooled sessions or on special devices like the Windows 365 Boot devices, where the consent prompt looks just wrong, since it interrupts the seamless flow.
Leave a Reply