A while ago I wrote a blog post, about how you can automatically assign Intune Scope Tags based on Entra ID User information: Set Intune Device ScopeTags based on User Locations – Mike’s MDM Blog (mikemdm.de) This script directly assigned the Scope Tag to the Intune object. While this script worked flawlessly for us for multiple years, it has one downside. In order to check if there is something to update, we have to query each device individually to get the current Scope Tag of the device. This creates load against the Graph API and does not scale too well for bigger environments.
Today I want to show you my new version of the script, that now uses Entra ID group memberships to assign the Scope Tags to the devices. We still use the location from the “usageLocation” field in Entra ID of the assigned user, but instead of directly assigning a Scope Tag, we will now assign the Entra device object to an Entra ID Group, and let Intune handle the individual assignment. This way we can request a list of all devices via Graph API and compare it to the Group membership of our Entra ID Groups, so all the logic checks happen within the script, which allows it to scale much better.
Prerequisites
Entra ID Groups
Before we can start with the automation, we need to create the Entra ID Groups and Scope Tags in Intune. Let’s start with the groups, all Groups has to follow a specific naming convention, that we can define later in the PowerShell script. In my example, I used “Intune – ScopeTags – Scope_” as prefix, so the script just has to assign the country code from Entra ID

We need a group for each country code used in Entra ID + one for Scope_OTHER, that is used, when the script is not able to determine a location, for example if a device is missing an assigned user.
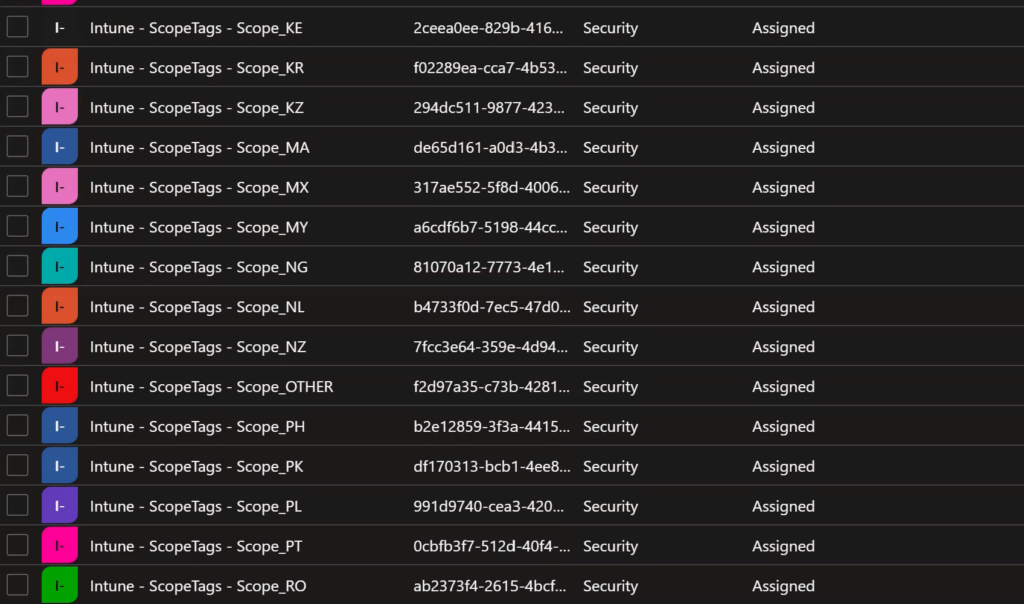
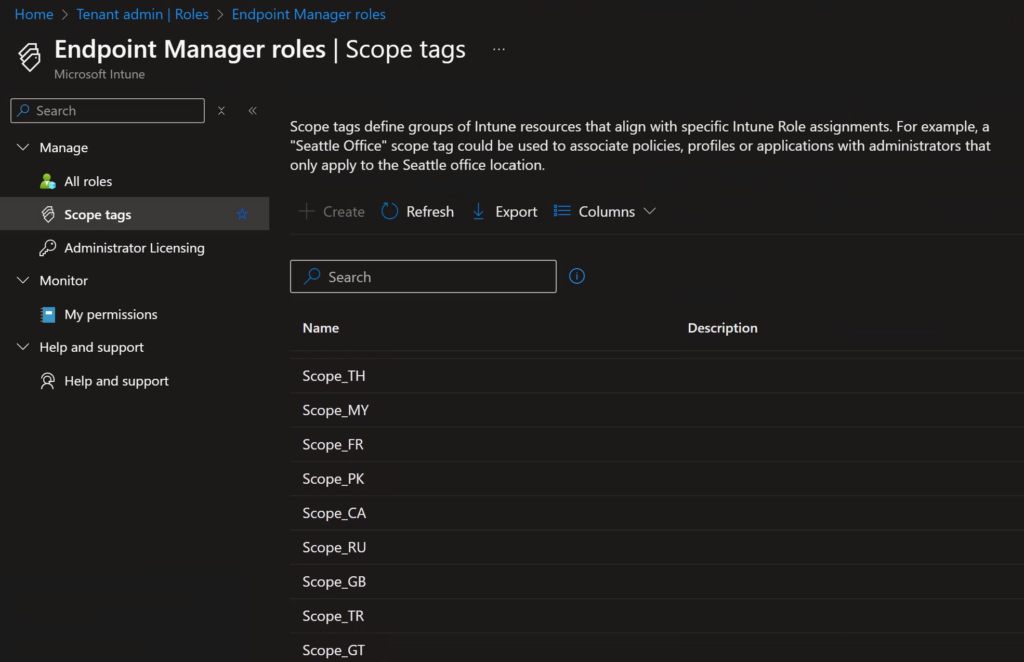
Intune Scope Tags
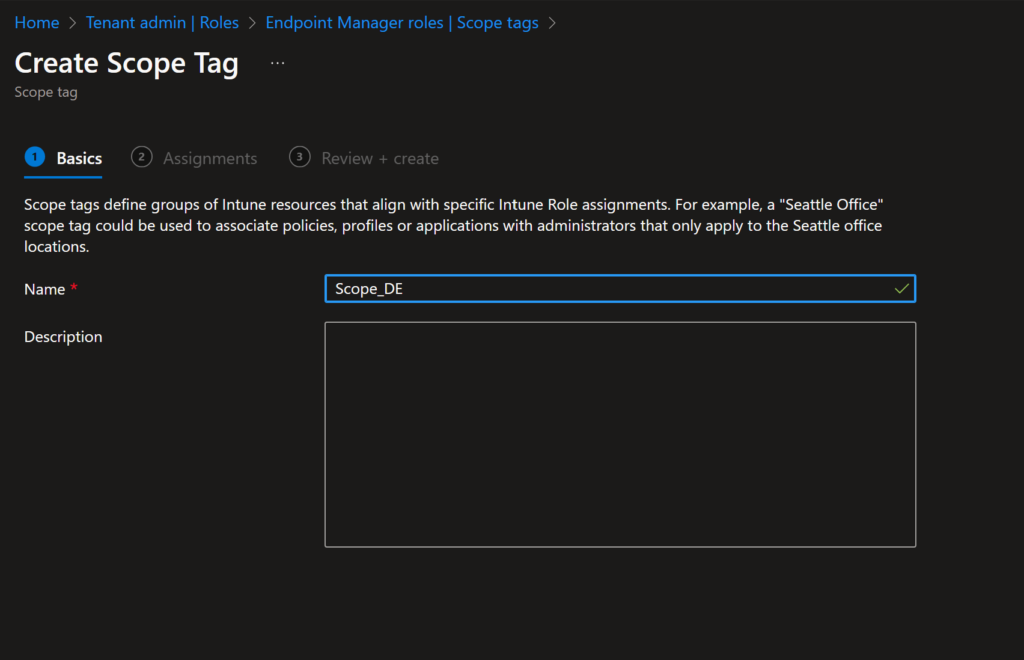
Next, we can create our Scope Tags in Intune, once again one per location used.
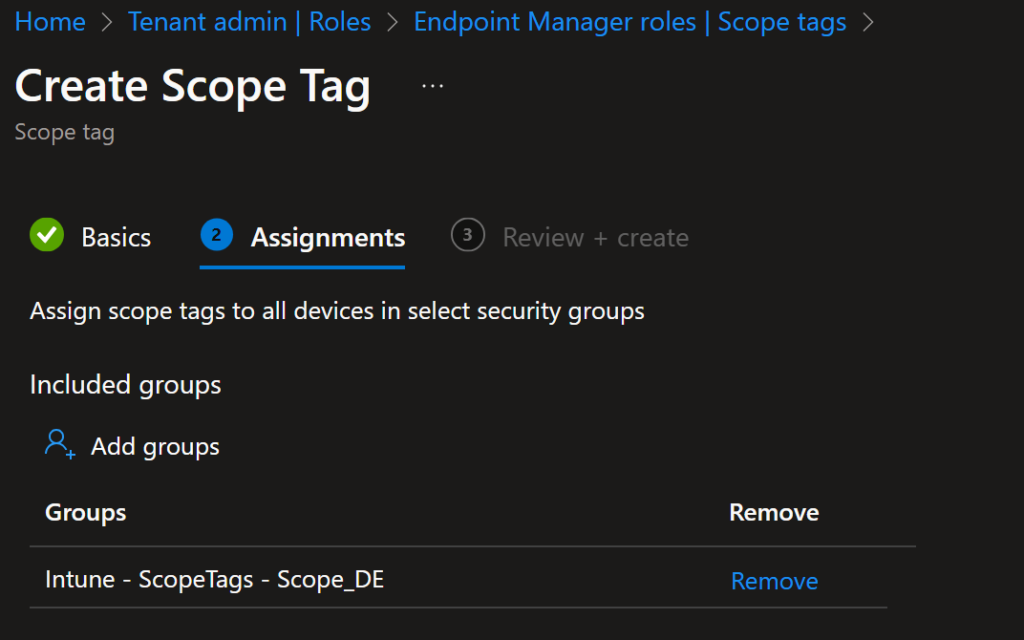
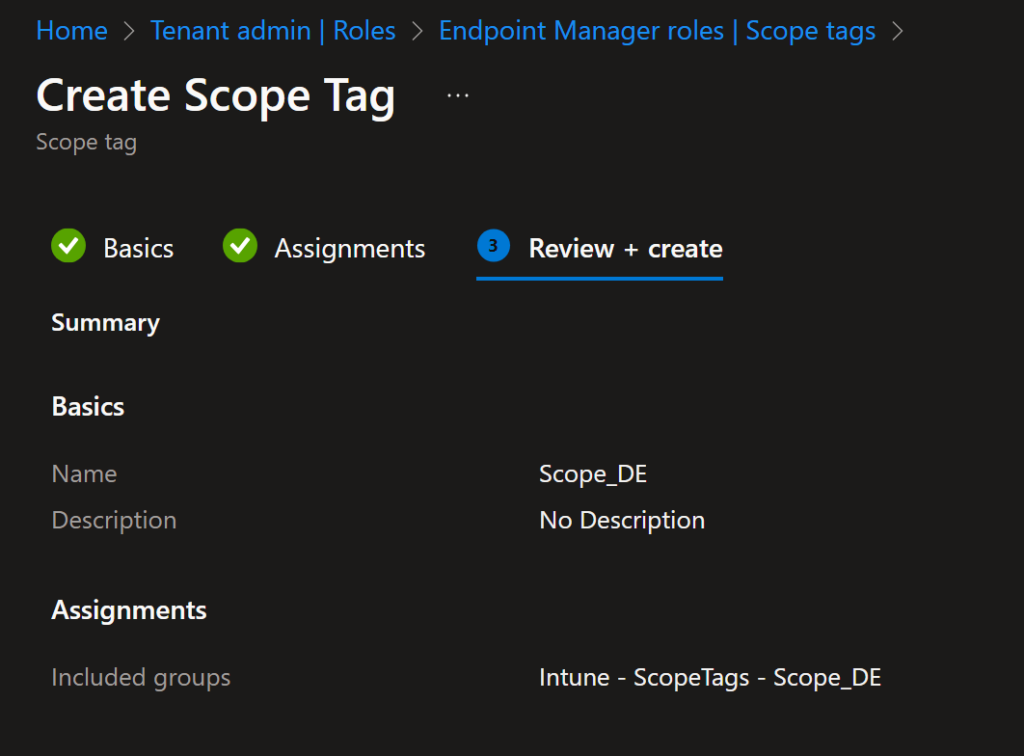
We can directly assign these Scope Tags to the previously created Entra ID groups.
Azure Automation
Now that we have fulfilled all our prerequisites, we can start with the automation account.
Azure Automation Account
To create the needed Azure Automation Account, we again need to go to the Azure Marketplace and search for the “Automation”
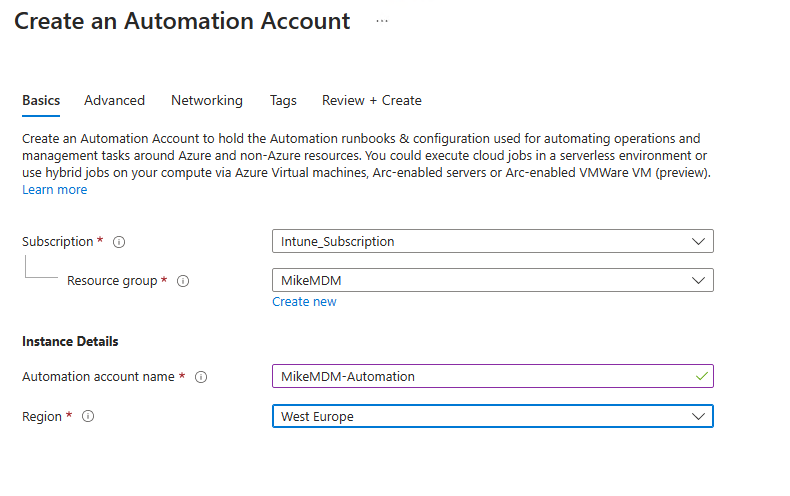
Give it a name and select the region:
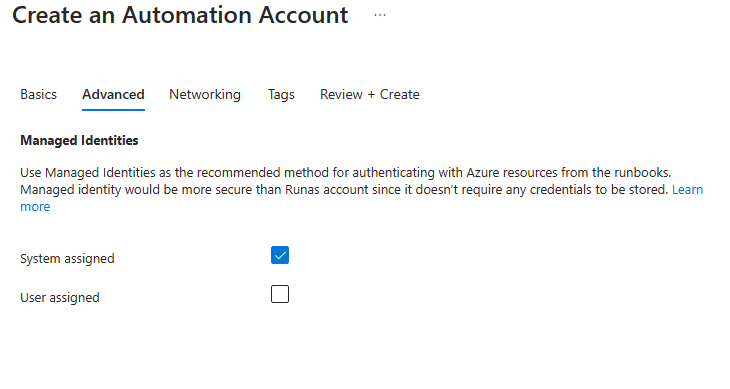
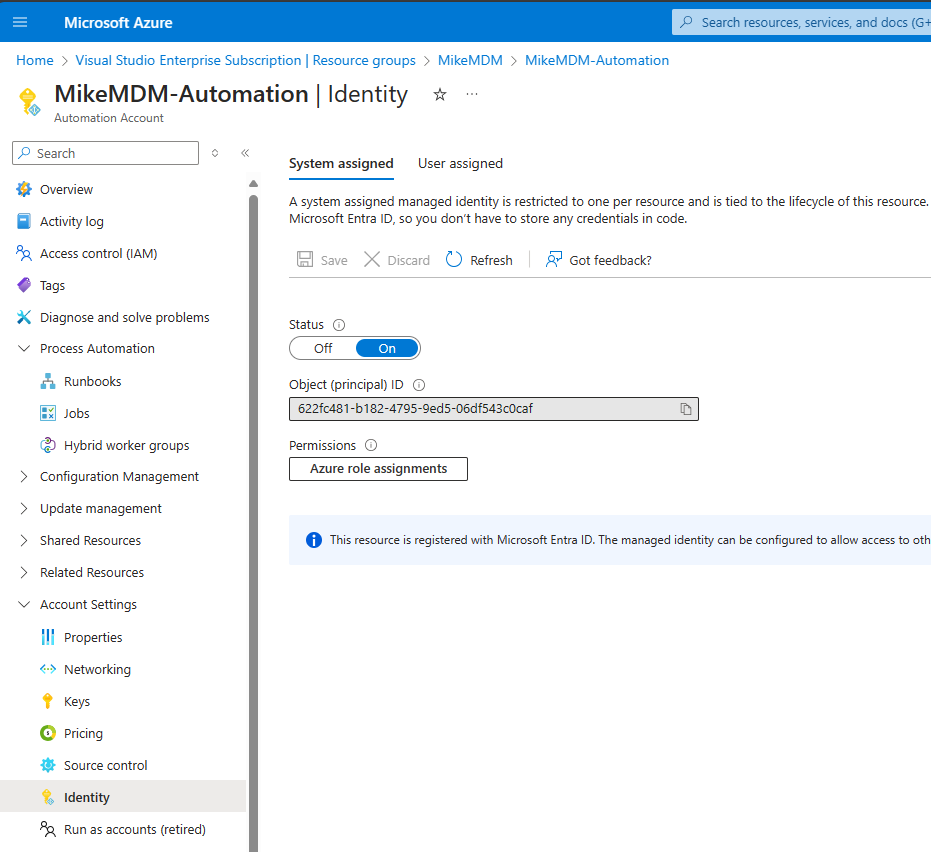
And make sure to enable the system managed identity:
Azure Automation Runbook
Once the Automation Account is created, we can assign the needed Permissions to the System Managed Identity. Just replace the ID from the Identity Tab of the Automation Account in the Script.
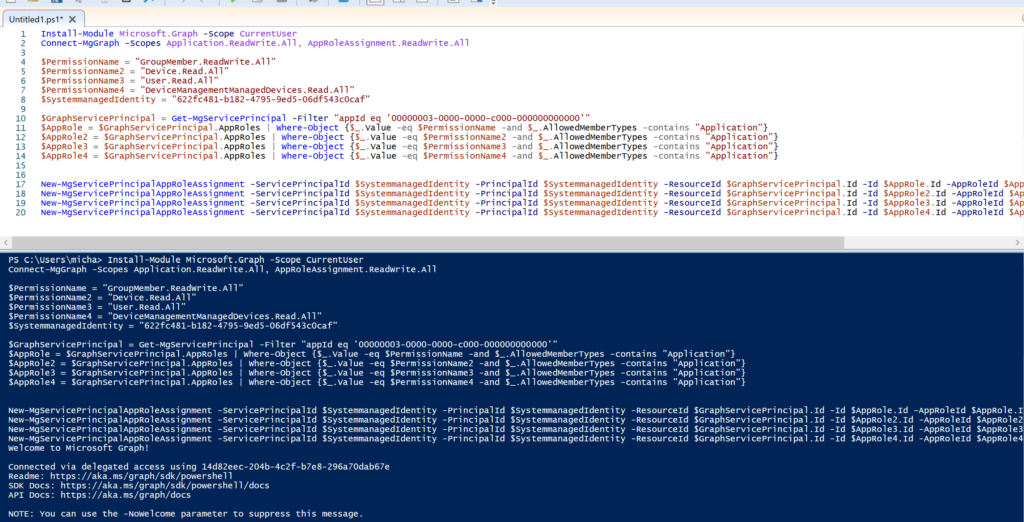
You can find the needed Script to assign the Permissions here: Assign Permissions
The Script will add the following permissions to the managed identity:
- GroupMember.ReadWrite.All
- Device.Read.All
- User.Read.All
- DeviceManagementManagedDevices.Read.All
Now that we have all prerequisites, we can create the actual Runbook in our Automation Account:
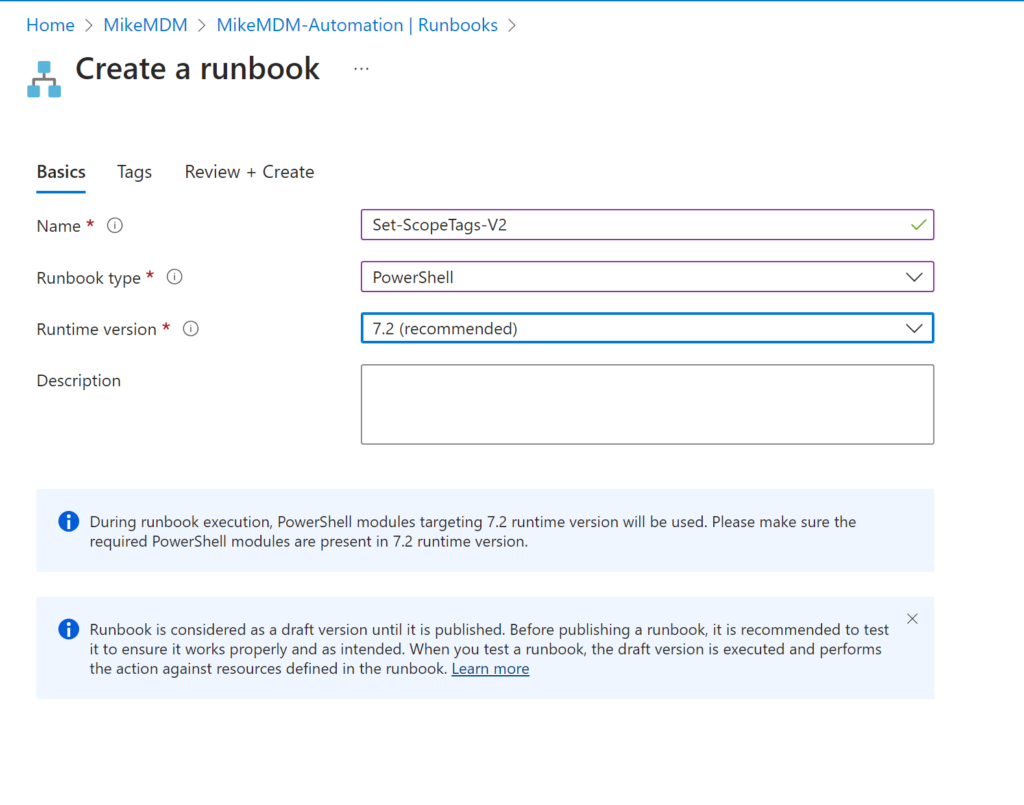
Give it a name and select PowerShell as Runbook type:
In the actual Runbook, copy the code from: https://github.com/mmeierm/Scripts/blob/main/ScopeTagsV2/ScopeTagsV2.ps1
As mentioned above, you can also modify the Group Prefix in line 7 to match your needs.
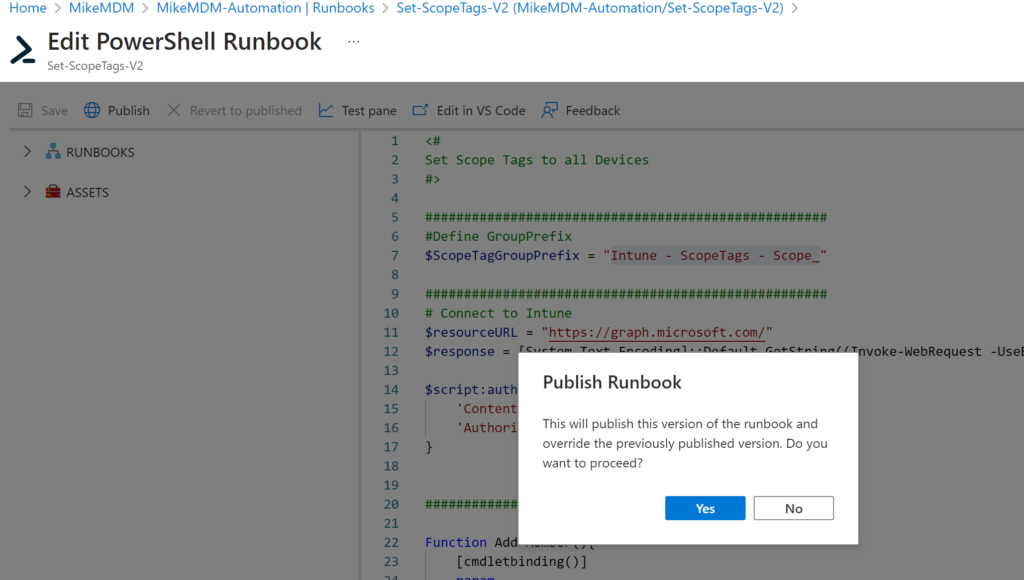
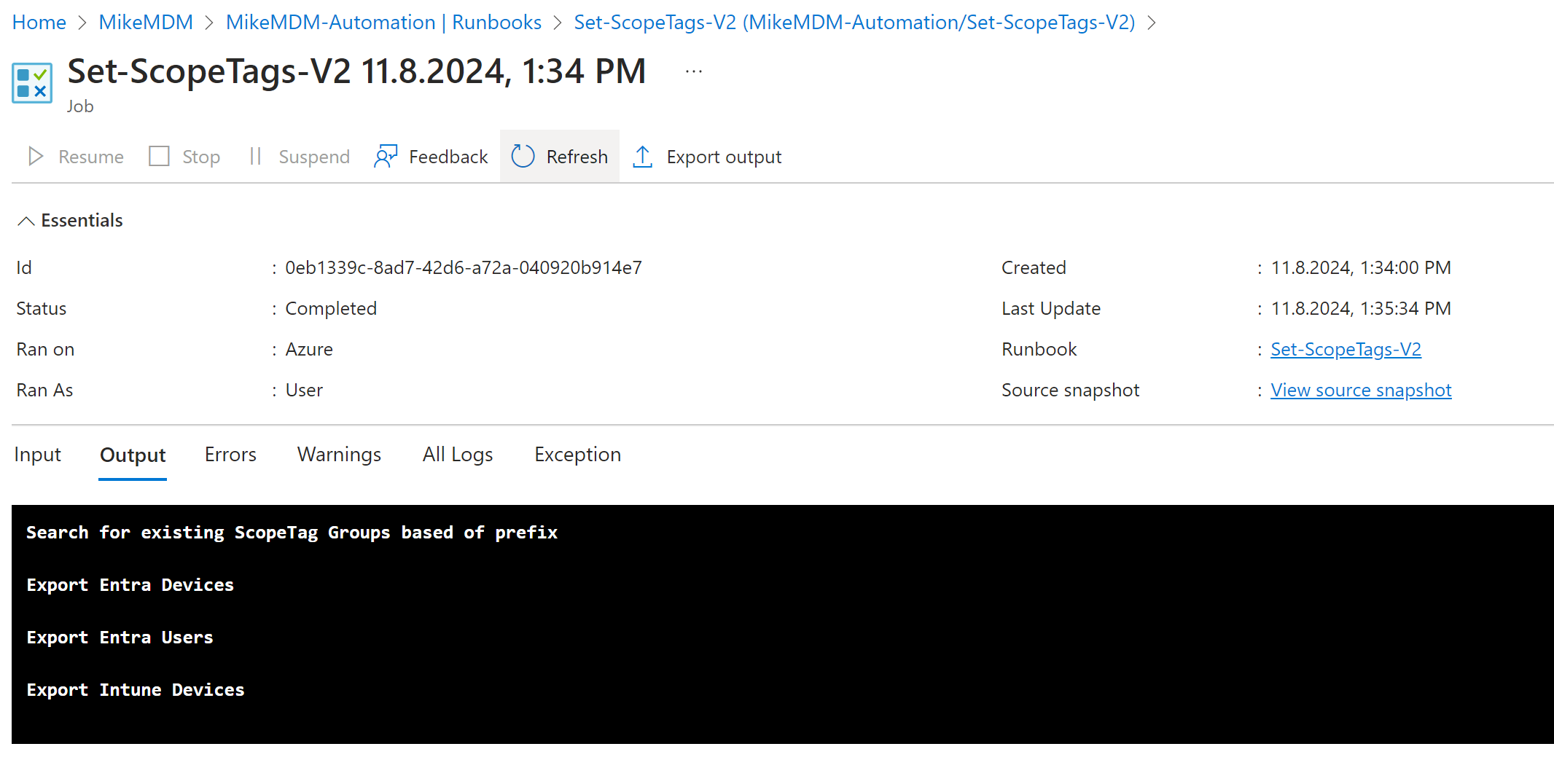
Once published, we can run it for the first time.
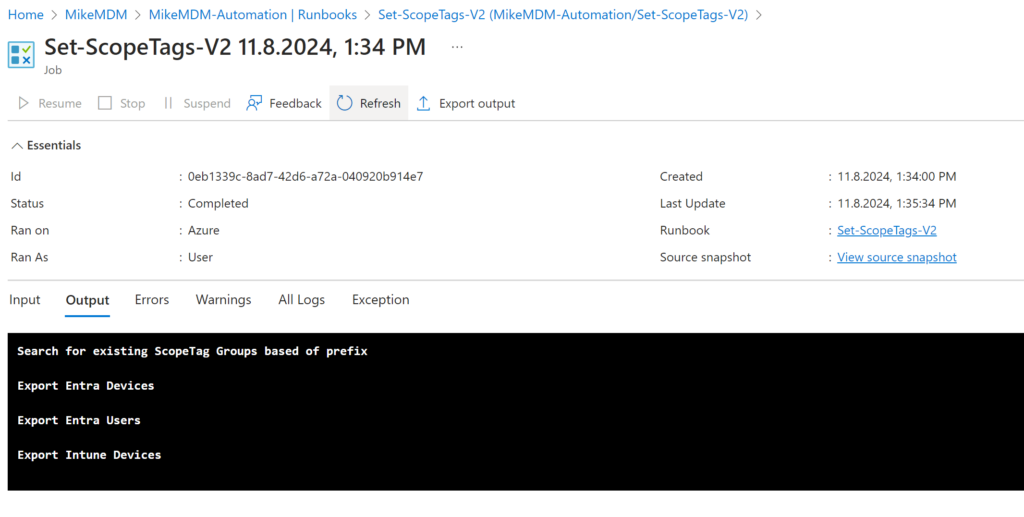
If everything worked, you should see the devices have been added to their respected groups:
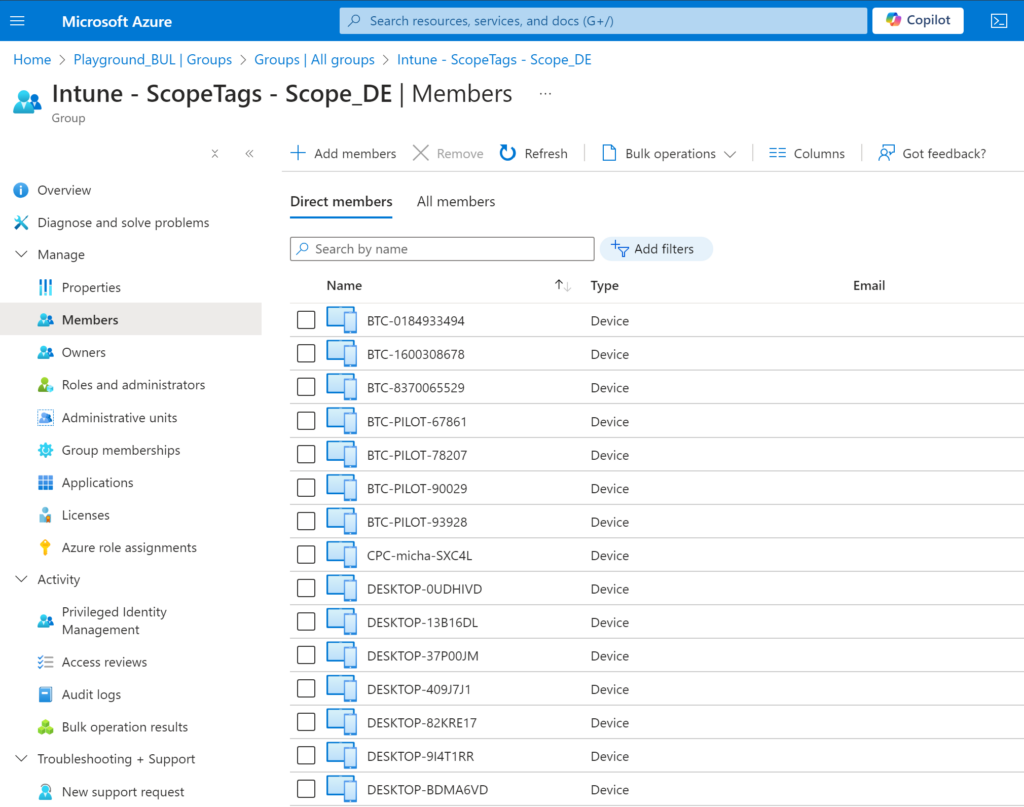
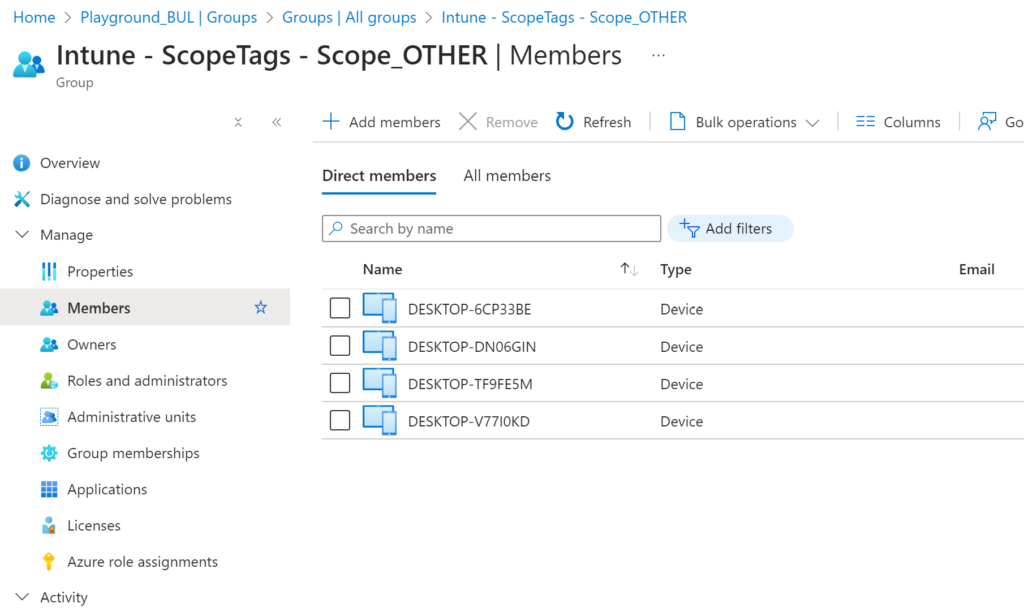
If you are happy with the result, you can now link a schedule to let the script run automatically.
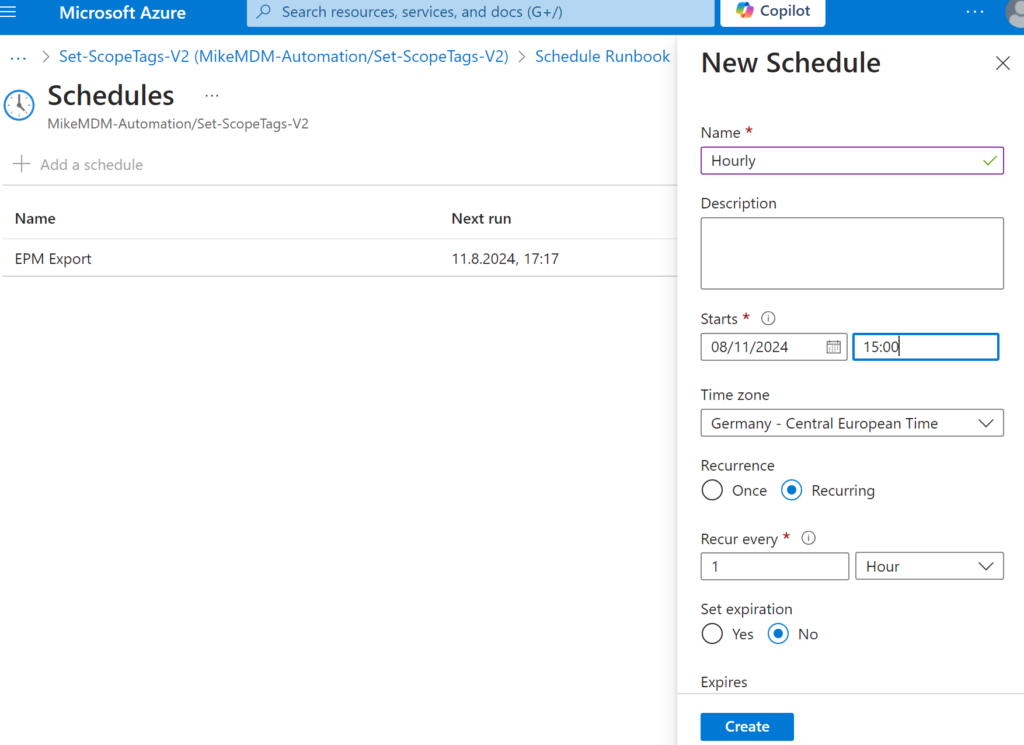
Create a new Schedule or select an existing one, that matches your needs.
Conclusion
Having an option to automatically assign Scope Tags, allows admins to assign permissions for distributed IT departments scoped to the needs. Hopefully one day this can be done directly in Intune, but for now the my new script allows you to do it in an automated way, and since we are now leveraging Entra ID Groups instead of assigning it directly, the script scales pretty well, even in bigger environments.
Leave a Reply